目录导航
0x01 前言
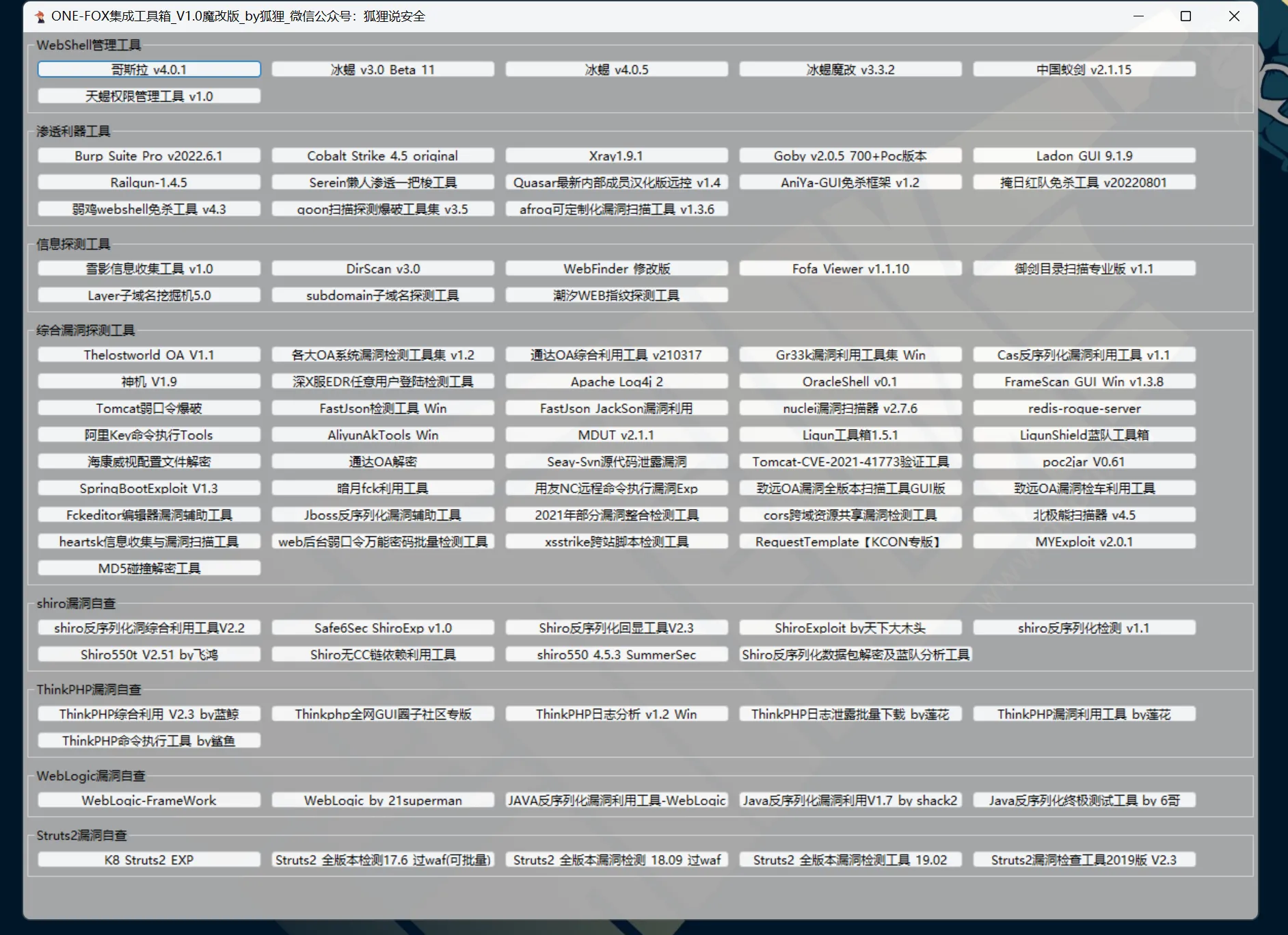
最近闲的无聊就把GUItools工具进行魔改加工了一波,去除了一些工具,新增些许新工具,修复BUG,更新了一些软件的版本。此1.0魔改版本的工具不是很全,我们会在后期的版本中持续更新。
此工具为python语言编写,未进行exe打包程序,未对代码进行加密,可二次开发,无任何后门,不要以谣传谣,代码都是开放的,不放心的师傅可以自行查看哈~~~
魔改版作者:狐狸
0x02 工具截图
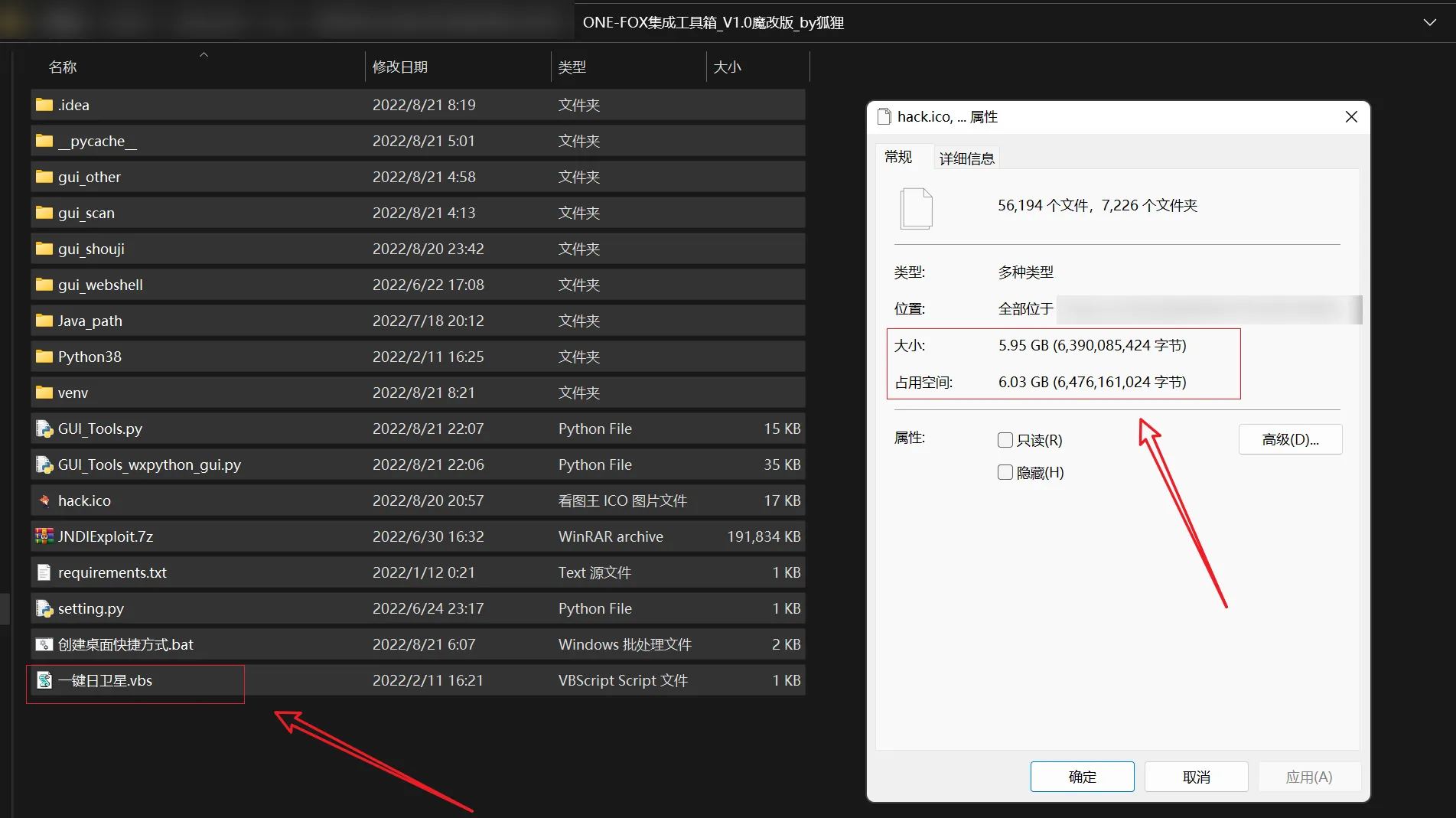
工具目录截图:
0x03部分目录列表
+---ONE-FOX集成工具箱_V1.0魔改版_by狐狸_www.ddosi.org.rar
| GUI_Tools.py
| GUI_Tools_wxpython_gui.py
| hack.ico
| JNDIExploit.7z
| requirements.txt
| setting.py
| 一键日卫星.vbs
| 创建桌面快捷方式.bat
|
+---.idea
| | ONE-FOX集成工具箱_V1.0魔改版_by狐狸.iml
| | workspace.xml
| |
| \---inspectionProfiles
| profiles_settings.xml
| Project_Default.xml
|
+---gui_other
| +---afrog
| | | afrog.bat
| | | afrog.exe
| | | afrog1.bat
| +---aniya
| | AniYa.bat
| | AniYa.exe
| +---burpsuite_pro
| | | autoDecoder-0.15.jar
| | | burp-log4shell.jar
| | | BurpCrypto-0.1.9.1-full.jar
| | | BurpFastJsonScan8.jar
| | | BurpLog4j2Scan-1.0-SNAPSHOT.jar
| | | BurpShiroPassiveScan-1.7.6.jar
| | | BurpSuite.icns
| | | BurpSuiteLoader-UI.jar
| | | BurpSuiteLoader_v2022.jar
| | | burpsuite_pro_v2022.6.1.jar
| | | Chunk-Proxy v1.10.jar
| | | chunked-coding-converter-0.4.0.jar
| | | config.cfg
| | | FastjsonScan.jar
| | | Fiora-v0.1-jar-with-dependencies.jar
| | | HackBar.jar
| | | HaE-2.3-J9.jar
| | | jython-standalone-2.7.2.jar
| | | knife-2.0-jar-with-dependencies.jar
| | | Log4J-Check-1.0.1-SNAPSHOT-jar-with-dependencies.jar
| | | log4j2burpscanner-0.19.0-jdk11.jar
| | | log4j2burpscanner-0.19.0-jdk8.jar
| | | Log4j2Scan-0.10-SNAPSHOT-01.jar
| | | Log4j2Scan-0.10-SNAPSHOT-02.jar
| | | Log4j2Scan-0.10-SNAPSHOT.jar
| | | log4j2Scan-1.3.0.jar
| | | Log4JScan-1.0.0-SNAPSHOT-jar-with-dependencies.jar
| | | LoggerPlusPlus.jar
| | | passive-scan-client-0.3.0.jar
| | | shiroPoc-0.5-SNAPSHOT-jar-with-dependencies.jar
| | | SpringScan_jdk11.jar
| | | SpringScan_jdk8.jar
| | | Struts2_Check.jar
| | | WooyunSearch-1.0-SNAPSHOT-jar-with-dependencies.jar
| | |
| | +---BurpBountyPro_v2.5.0
| | | | BurpBountyPro_v2.5_Cracked.jar
| | | |
| | | \---BurpBountyData
| | | +---profiles
| | | | AccessToken.bb
| | | | Action_parameters.bb
| | | | ACTIVE - HTTP Interaction.bb
| | | | ACTIVE - HTTP Response Splitting.bb
| | | | ACTIVE - Remote Code Execution.bb
| | | | ACTIVE - SQL Injection (Blind).bb
| | | | ACTIVE - Traversal.bb
| | | | ACTIVE - XSS.bb
| | | | ACTIVE-OpenRedirect.bb
| | | | ACTIVE-SQLi-Error-SQLmap.bb
| | | | All_Requests_And_Parameters.bb
| | | | AmazonAWS.bb
| | | | AmazonAWSRequest.bb
| | | | Amazon_AWS_S3_Url.bb
| | | | Amazon_AWS_Url.bb
| | | | Amazon_MWS_Auth_Token.bb
| | | | Android_WebView_JS.bb
| | | | ApiKeyRequest.bb
| | | | ApiKeyResponse.bb
| | | | ApiPath.bb
| | | | API_Keys.bb
| | | | Api_path.bb
| | | | Application_Resources.bb
| | | | Application_URLs.bb
| | | | Artica_Web.bb
| | | | Artica_Web_Proxy_Auth_Bypass_CVE-2020-17506.bb
| | | | Artica_Web_Request.bb
| | | | Artifactory_API_Token.bb
| | | | Artifactory_Password.bb
| | | | Atlassian_Crowd_RCE_CVE-2019-11580.bb
| | | | AuthorizationBearerToken.bb
| | | | Authorization_Bearer.bb
| | | | AWS_Access_Key_ID.bb
| | | | AWS_Client_Secret.bb
| | | | AWS_Creds_File.bb
| | | | AWS_EC2_Url.bb
| | | | AWS_Region.bb
| | | | AWS_Secret_Key.bb
| | | | Azure_Blob_Discovered.bb
| | | | Basic_Auth_Credentials.bb
| | | | Beacon.bb
| | | | Bitcoin_Address.bb
| | | | BlindRCE.bb
| | | | BlindSQLi-TimeBased.bb
| | | | BlindXSS.bb
| | | | BlindXXE.bb
| | | | BlindXXE_Xinclude_SSRF.bb
| | | | Blind_RCE_Linux.bb
| | | | Blind_RCE_Linux_GETParams.bb
| | | | Blind_RCE_Linux_POSTParams.bb
| | | | Blind_RCE_Windows.bb
| | | | Blind_RCE_Windows_GETParams.bb
| | | | Blind_RCE_Windows_POSTParams.bb
| | | | Blind_XSS.bb
| | | | Blind_XSS_append.bb
| | | | Blind_XSS_GETParams.bb
| | | | Blind_XSS_POSTParams.bb
| | | | Blind_XSS_replace.bb
| | | | Blind_XXE.bb
| | | | Cache-Control.bb
| | | | CDN_Detected.bb
| | | | Cisco_ASA_Device_Found.bb
| | | | Cisco_ASA_LFI-CVE-2020-3452.bb
| | | | Cisco_Request_Detected.bb
| | | | Cisco_Wan_VPN_disclosure-CVE-2019-1653.bb
| | | | Citrix_ADC_Directory_Traversal_CVE-2019-19781.bb
| | | | Citrix_Detection.bb
| | | | Citrix_ShareFile_File_Read_CVE-2020-8982.bb
| | | | Citrix_XenMobile_PathTraversal.bb
| | | | Cloudinary_Basic_Auth.bb
| | | | CMSDetection.bb
| | | | CMS_Found.bb
| | | | CodeClimate_Key.bb
| | | | Command-Injection-commix.bb
| | | | Command_Injection.bb
| | | | Content-Security-Policy.bb
| | | | CookieAttrubute-HttpOnly.bb
| | | | CookieAttrubute-SameSite.bb
| | | | CookieAttrubute-Secure.bb
| | | | Cookie_Security.bb
| | | | CORS Misconfiguration.bb
| | | | CouchDB_Admin_Exposure.bb
| | | | CouchDB_Request.bb
| | | | CouchDB_Response.bb
| | | | CredsDisclosed.bb
| | | | CRLF-Attack.bb
| | | | CRLF.bb
| | | | CRLF_append.bb
| | | | CRLF_GETParams.bb
| | | | CRLF_POSTParams.bb
| | | | CRLF_replace.bb
| | | | Custom_SSRF.bb
| | | | CVE-2017-9506_Jira_SSRF.bb
| | | | CVE-2018-1271_Spring_MVC_Path_Traversal.bb
| | | | CVE-2018-13379_FortiOS_Creds_Disclosure.bb
| | | | CVE-2019-11510_Pulse_Secure.bb
| | | | CVE-2019-11580_Atlassian_Crowd_RCE.bb
| | | | CVE-2019-1653_Cisco_Wan_VPN_disclosure.bb
| | | | CVE-2019-19781_Citrix_ADC_Directory_Traversal.bb
| | | | CVE-2019-3799_Spring_Cloud_Path_Traversal.bb
| | | | CVE-2019-5418_Ruby on Rails - WAF bypass.bb
| | | | CVE-2019-5418_Ruby on Rails.bb
| | | | CVE-2019-8442_Jira_Path_Traversal.bb
| | | | CVE-2019-8449_Jira_Unauthenticated_Sensitive_Info.bb
| | | | CVE-2020-10770_SSRF.bb
| | | | CVE-2020-11738_Wordpress_Duplicator_Plugin_LFI.bb
| | | | CVE-2020-13167_Netsweeper_code_injection.bb
| | | | CVE-2020-13379_Grafana_SSRF.bb
| | | | CVE-2020-14179_Jira_Info_Exposure.bb
| | | | CVE-2020-14181_Jira_User_Enum.bb
| | | | CVE-2020-14815_XSS.bb
| | | | CVE-2020-15129_Traefik_Open_Redirect.bb
| | | | CVE-2020-17506_Artica_Web_Proxy_Auth_Bypass.bb
| | | | CVE-2020-24312_File_Manager_Wordpress_Backups.bb
| | | | CVE-2020-2551_Oracle_WebLogic.bb
| | | | CVE-2020-3452_Cisco_ASA_LFI.bb
| | | | CVE-2020-5410_Path_Traversal_Spring_Cloud.bb
| | | | CVE-2020-5412_Spring_Cloud_Netflix.bb
| | | | CVE-2020-5777_MAMGI_Auth_Bypass.bb
| | | | CVE-2020-5902_F5-BigIP.bb
| | | | CVE-2020-8209_Citrix_XenMobile_PathTraversal.bb
| | | | CVE-2020-8982_Citrix_ShareFile_File_Read.bb
| | | | CVE-2020-9484_Tomcat_Groovy.bb
| | | | CVE-2021-26086_PathTraversal_Atlassian_Jira.bb
| | | | CVE-2021-3654_OpenRedirect.bb
| | | | CVE-2021-40438_Apache_mod_proxy_SSRF.bb
| | | | CVE-2021-40539_Zoho_ManageEngine_ADSelfService.bb
| | | | CVE-2021-43798_Grafana_LFI.bb
| | | | CVE-2021-43798_Path_Traversal.bb
| | | | CVE-2021-44228.bb
| | | | CVE-2021-44228_RCE_Log4j.bb
| | | | CVE-2021-44228_RCE_Log4j_GETPOST.bb
| | | | CVE-2021-44228_RCE_Log4j_urlEncode.bb
| | | | CVE-2021-44228_RCE_Log4j_WAF.bb
| | | | CVE-2022-1388_F5_Big_IP_RCE.bb
| | | | Debug Pages.bb
| | | | Debug_Logic_Parameters.bb
| | | | Debug_variables.bb
| | | | DefaultRDP.bb
| | | | DigitalOcean_Space_Discovered.bb
| | | | DirectoryListing.bb
| | | | Docker_API_Response.bb
| | | | DomainTakeOver_Strings.bb
| | | | DOM_XSS_Sinks.bb
| | | | Drupalgeddon.bb
| | | | Drupal_Response.bb
| | | | Drupal_User_Enum.bb
| | | | Drupal_User_Enum_Redirect.bb
| | | | easy_wp_smtp_listing_enabled.bb
| | | | Echo_RCE.bb
| | | | Echo_RCE_append.bb
| | | | Echo_RCE_replace.bb
| | | | EmailInput.bb
| | | | EndpointsExtractor.bb
| | | | Env_Vars.bb
| | | | ErrorMessage.bb
| | | | ErrorPages-JobApps.bb
| | | | ErrorSQLi.bb
| | | | Expect_RCE.bb
| | | | F5-BigIP_CVE-2020-5902.bb
| | | | Facebook_Client_ID.bb
| | | | Facebook_OAuth.bb
| | | | File_Manager_Wordpress_Backups_CVE-2020-24312.bb
| | | | Firebase DB detected.bb
| | | | Fortinet_Panel.bb
| | | | Fortinet_Request.bb
| | | | FortiOS_Creds_Disclosure_CVE-2018-13379.bb
| | | | Fuzzing_directories.bb
| | | | GCP_Service_Account.bb
| | | | GCP_Urls.bb
| | | | Generic-BlindSQLi.fuzzdb.bb
| | | | Generic-SQLi.bb
| | | | GitFinder.bb
| | | | Gmail_Oauth_2.0.bb
| | | | Google_Cloud_Buckets.bb
| | | | Google_Cloud_Platform_OAuth_2.0.bb
| | | | Google_Drive_OAuth.bb
| | | | Google_Oauth.bb
| | | | Graphql Introspection.bb
| | | | GraphqlPath.bb
| | | | GraphQL_Endpoint.bb
| | | | Heroku_OAuth_2.0.bb
| | | | Hidden Parameters.bb
| | | | HockeyApp_Key.bb
| | | | Host_Header_Injection.bb
| | | | HTTP_Response_Splitting.bb
| | | | IDOR_parameters.bb
| | | | Interesting_Keyworks.bb
| | | | Java_De-Serialization.bb
| | | | Jenkins_Response.bb
| | | | Jira_CVE-2018-20824.bb
| | | | Jira_Detection.bb
| | | | Jira_Info_Exposure_CVE-2020-14179.bb
| | | | Jira_Path_Traversal_CVE-2019-8442.bb
| | | | Jira_Request.bb
| | | | Jira_SSRF_CVE-2017-9506.bb
| | | | Jira_unauthenticated_Info.bb
| | | | JIRA_Unauthenticated_Sensitive_Info_CVE-2019-8449.bb
| | | | Jira_User_Enum_CVE-2020-14181.bb
| | | | Joomla detection.bb
| | | | Joomla-ArbitraryFileUpload.bb
| | | | Joomla-CVE-2015-7297.bb
| | | | Joomla-ReflectedXSS.bb
| | | | JoomlaSQLi-com_artforms.bb
| | | | JSON-Fuzz (SecLists).bb
| | | | JSON.Fuzzing.bb
| | | | JS_LinkFinder.bb
| | | | JS_Variables.bb
| | | | JWT-Request.bb
| | | | JWT-Response.bb
| | | | JWT.bb
| | | | Keys.bb
| | | | Key_Parameters.bb
| | | | Kubernetes_API_Exposed.bb
| | | | Kubernetes_Response.bb
| | | | LDAP.Fuzzinging.bb
| | | | LFI-JHADDIX.bb
| | | | LFI_RFI_Parameters.bb
| | | | LICENSE
| | | | LinkedIn_Client_ID.bb
| | | | LinkedIn_Secret.bb
| | | | Linux-Apache2-conf.bb
| | | | Linux-mysql-conf.bb
| | | | Linux-Path-bypass.bb
| | | | Linux-Path.bb
| | | | Linux-PathTraversal-MR.bb
| | | | Linux-PathTraversal.bb
| | | | Linux-php.ini.bb
| | | | Linux-self-environ.bb
| | | | Linux-source-list.bb
| | | | Linux-sshd-conf.bb
| | | | Linux-vsftpd-conf.bb
| | | | Linux-vsftpd-log.bb
| | | | MAC_Address.bb
| | | | MAGMI_Request.bb
| | | | MAGMI_Response.bb
| | | | Mailto.bb
| | | | MAMGI_Auth_Bypass_CVE-2020-5777.bb
| | | | MoodleRequestDetection.bb
| | | | Moodle_ReflectedXSS.bb
| | | | MySQL-SQLi-Login-Bypass.fuzzdb.bb
| | | | Netsweeper_code_injection_CVE-2020-13167.bb
| | | | Netsweeper_Request.bb
| | | | Netsweeper_Response.bb
| | | | NoSQL.bb
| | | | NoSQL_Session_Token.bb
| | | | NuGet_Api_Key.bb
| | | | OAuth2.bb
| | | | OAuth2response.bb
| | | | OAuth_parameters.bb
| | | | Octopus_API_Key.bb
| | | | OOB-Callbacks.bb
| | | | Open Firebase Database.bb
| | | | OpenRedirect-ParameterPollution.bb
| | | | OpenRedirect-ParameterPollution_Path.bb
| | | | OpenRedirect.bb
| | | | OpenRedirectActive.bb
| | | | OpenRedirect_GETParams.bb
| | | | OpenRedirect_POSTParams.bb
| | | | OpenRedirect_SSRF_Collaborator.bb
| | | | OpenRedirect_SSRF_Collaborator_GETParams.bb
| | | | OpenRedirect_SSRF_Collaborator_HTTP0_9.bb
| | | | OpenRedirect_SSRF_Collaborator_HTTP1_0.bb
| | | | OpenRedirect_SSRF_Collaborator_POSTParams.bb
| | | | OpenRedirect_SSRF_Parameters.bb
| | | | OpenRedirect_to_Account_Takeover.bb
| | | | Openredirect_to_XSS.bb
| | | | Open_Redirect.bb
| | | | Oracle_WebLogic_RCE_CVE-2020-2551.bb
| | | | Outlook_Team.bb
| | | | PASSIVE - Private Key Found.bb
| | | | PASSIVE - Subscribe Form Found.bb
| | | | PASSIVE-Errors_Vulns_Detect.bb
| | | | PASSIVE-swaggerFinder.bb
| | | | Password-Reset-Headers.bb
| | | | Password-Reset-Params.bb
| | | | Password-Reset-URL.bb
| | | | PathTraversal_Linux.bb
| | | | PathTraversal_Linux_GETParams.bb
| | | | PathTraversal_Linux_POSTParams.bb
| | | | PathTraversal_Windows.bb
| | | | PathTraversal_Windows_GETParams.bb
| | | | PathTraversal_Windows_POSTParams.bb
| | | | Path_Traversal_Spring_Cloud_CVE-2020-5410.bb
| | | | Paypal_Braintree_access_token.bb
| | | | PHP_RCE.bb
| | | | PHP_RCE_GETParams.bb
| | | | PHP_RCE_POSTParams.bb
| | | | Picatic_API_Key.bb
| | | | Possible XML Request_XXE.bb
| | | | Private_SSH_Key.bb
| | | | Pulse_Secure_CVE-2019-11510.bb
| | | | RCE-linux-Based.bb
| | | | RCE.bb
| | | | RCE_Linux.bb
| | | | RCE_Linux_GETParams.bb
| | | | RCE_Linux_POSTParams.bb
| | | | RCE_Parameters.bb
| | | | RCE_Windows.bb
| | | | RCE_Windows_GETParams.bb
| | | | RCE_Windows_POSTParams.bb
| | | | Reflected_Values.bb
| | | | Reflected_values_greater_than_three_characters.bb
| | | | RegisterUser_parameters.bb
| | | | Remote_Code_Execution.bb
| | | | RoR CVE-2019-5418 WAF Bypass.bb
| | | | RoR_CVE-2019-5418_WAF_Bypass.bb
| | | | Ruby on Rails CVE-2019-5418 - WAF bypass.bb
| | | | Ruby on Rails CVE-2019-5418.bb
| | | | Ruby_on_Rails_CVE-2019-5418.bb
| | | | Secret-keywords-SecLists.bb
| | | | Secrets_Request.bb
| | | | SecurityHeaders.bb
| | | | SerializedObject.bb
| | | | ServerBanner.bb
| | | | Server_Side_Template_Injection.bb
| | | | Software_Version.bb
| | | | Software_Version_revealed.bb
| | | | solarwinds_default_admin.bb
| | | | Solarwinds_Orion_Request.bb
| | | | Solarwinds_Orion_Response.bb
| | | | SonarQube_API_Key_Docs.bb
| | | | Source_code.bb
| | | | Spring Boot Actuators.bb
| | | | Springboot_Requests.bb
| | | | Spring_Cloud_Netflix_SSRF-CVE-2020-5412.bb
| | | | Spring_Cloud_Path_Traversal_CVE-2019-3799.bb
| | | | Spring_MVC_Path_Traversal_CVE-2018-1271.bb
| | | | SQLi-Error-SQLmap.bb
| | | | SQLi.bb
| | | | SQLi_Collaborator.bb
| | | | SQLi_Collaborator_GETParams.bb
| | | | SQLi_Collaborator_POSTParams.bb
| | | | SQLi_GETParams.bb
| | | | SQLi_Parameters.bb
| | | | SQLi_POSTParams.bb
| | | | SQLi_TimeBased.bb
| | | | SQLi_TimeBased_append.bb
| | | | SQLi_TimeBased_GETParams.bb
| | | | SQLi_TimeBased_POSTParams.bb
| | | | SQLi_TimeBased_replace.bb
| | | | SQL_Message_Detected.bb
| | | | SSI-Injection-JHADDIX.bb
| | | | SSRF-Collaborator.bb
| | | | SSRF-Collaborator_GETParams.bb
| | | | SSRF-Collaborator_POSTParams.bb
| | | | SSRF-URLScheme.bb
| | | | SSRF-URLScheme_GETParams.bb
| | | | SSRF-URLScheme_POSTParams.bb
| | | | SSRF_Collaborator_HTTP0_9.bb
| | | | SSRF_Collaborator_HTTP1_0.bb
| | | | SSTI.bb
| | | | SSTI_GET_Params.bb
| | | | SSTI_Parameters.bb
| | | | SSTI_POST_Params.bb
| | | | StackHawk_API_Key.bb
| | | | Strict-Transport-Security.bb
| | | | Subdomain_takeover.bb
| | | | SVNFinder.bb
| | | | Swagger-Finder.bb
| | | | Swagger_found.bb
| | | | Swagger_Request.bb
| | | | Symfony_Debug.bb
| | | | Symfony_Response.bb
| | | | tags.txt
| | | | Test_XSS_append.bb
| | | | Test_XSS_append_encoded.bb
| | | | Test_XSS_append_GetParams.bb
| | | | Test_XSS_append_POSTParams.bb
| | | | Test_XSS_discover.bb
| | | | Test_XSS_GET_POST.bb
| | | | Token_Found.bb
| | | | Token_Parameters.bb
| | | | Tomcat_Groovy_CVE-2020-9484.bb
| | | | Tomcat_Response_Detection.bb
| | | | Traefik_Open_Redirect-CVE-2020-15129.bb
| | | | Traefik_Response.bb
| | | | Traversal.bb
| | | | Twitter_Client_ID.bb
| | | | Twitter_OAuth.bb
| | | | UnixAttacks.fuzzdb.bb
| | | | URL_as_a_Value.bb
| | | | URL_Path_as_a_Value.bb
| | | | UserEnum_parameters.bb
| | | | US_SSN.bb
| | | | UUID_Request.bb
| | | | vBulletin_Response.bb
| | | | Version_Headers.bb
| | | | WAF_Found.bb
| | | | WebCachePoisoning.bb
| | | | WeblogicServer-UDDI_Explorer.bb
| | | | Weblogic_Request.bb
| | | | WebSphere_portal_SSRF.bb
| | | | Windows-Attacks.fuzzdb.bb
| | | | Windows-CommandInjection.bb
| | | | Woody_Wordpress_RCE.bb
| | | | WordPress Config.bb
| | | | WordPress detection.bb
| | | | WordPress-SensitiveDirectories.bb
| | | | WordPress_Config_Accessible.bb
| | | | WordPress_directory_listing.bb
| | | | WordPress_Duplicator_Plugin_LFI_CVE-2020-11738.bb
| | | | WordPress_JSmol2WP_SSRF.bb
| | | | WordPress_Path_Traversal.bb
| | | | wordpress_users_enum_yoastseo.bb
| | | | WordPress_user_enum_json.bb
| | | | WordPress_user_enum_oembed.bb
| | | | WordPress_XMLRPC_ListMethods.bb
| | | | WordPress_XMLRPC_Pingback.bb
| | | | WP_Config.bb
| | | | X-Content-Type-Options.bb
| | | | X-Frame-Options.bb
| | | | X-Headers-Collaborator-combined.bb
| | | | X-Headers-Collaborator.bb
| | | | X-XSS-Protection.bb
| | | | XML-FUZZ.bb
| | | | XSS - Akamai GHost bypass.bb
| | | | XSS-Akamai_GHost_bypass.bb
| | | | XSS-HtmlUrlEncode.bb
| | | | XSS-UrlEncode.bb
| | | | XSS.bb
| | | | XSSActive.bb
| | | | XSSHtmlUrlEncode.bb
| | | | XSSUrlEncode.bb
| | | | XSS_CVE-2020-14815.bb
| | | | XSS_GETPOST.bb
| | | | XSS_GET_Params.bb
| | | | XSS_HtmlUrlEncode.bb
| | | | XSS_Parameters.bb
| | | | XSS_POST_Params.bb
| | | | XSS_UrlEncode.bb
| | | | XXE-Fuzzing.bb
| | | | XXE.bb
| | | | XXE_Linux.bb
| | | | XXE_Windows.bb
| | | | XXE_Xinclude.bb
| | | | Youtube_Channel_ID.bb
| | |
| | +---BurpFastJsonScan8
| | | | log4j2Scan.jar
| | | |
| | | \---resources
| | | config.yml
| | |
| | \---log4j2Scan
| | | log4j2Scan.jar
| | |
| | \---resources
| | config.yml
| |
| +---Cobalt_Strike_4.5
| | | cobalt-4-5-user-guide.pdf
| | | cobalt-4-6-user-guide.pdf
| | | cobaltstrike
| | | cobaltstrike.exe
| | | cobaltstrike.jar
| | | cobaltstrike.sh
| | | cobaltstrike.store
| | | Cobalt_Strike_CN.bat
| | | Cobalt_Strike_CN.exe
| | | Cobalt_Strike_CN.vbs
| | | CSAgent.jar
| | | CSAgent.properties
| | | favicon.ico
| | | havex.profile
| | | icon.ico
| | | icon.jpg
| | | teamserver
| | | TeamServer.prop
| | | teamserver.sh
| | | teamserver_win.bat
| | |
| | +---plugin
| | | +---Ladon9.1.7_20220618
| | | | | CABARC.EXE
| | | | | Ladon.exe
| | | | | Ladon40.exe
| | | | | Ladon9.1.4_min.ps1
| | | | | Ladon9.1.7_all.ps1
| | | | | LadonExp.exe
| | | | | LadonGUI.exe
| | | | | Newtonsoft.Json.dll
| | | | | SubDomain.dic
| | | | | update.txt
| | | | | wiki.txt
| | | | |
| | | | \---scripts
| | | | | fun.txt
| | | | | Ladon-cn.cna
| | | | | Ladon.cna
| | | | | Ladon.exe
| | | |
| | | +---LSTAR
| | | | | LSTAR.cna
| | | | +---modules
| | | | | AuthMaintain.cna
| | | | | AuthPromote.cna
| | | | | BypassCxk.cna
| | | | | HavingFun.cna
| | | | | InfoCollect.cna
| | | | | IntrAgent.cna
| | | | | IntrScan.cna
| | | | | LateMovement.cna
| | | | | PassCapture.cna
| | | | | RemoteLogin.cna
| | | | | TraceClean.cna
| | | | |
| | | | \---scripts
| | | | +---AuthMaintain
| | | | | | SchTask.exe
| | | | | | ShadowUser.exe
| | | | | |
| | | | | +---AdUserApi
| | | | | | HaryyUser.exe
| | | | | |
| | | | | +---Exitservice
| | | | | | uinit.exe
| | | | | |
| | | | | +---Linkinfo
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Msdtc32
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Netapi32
| | | | | | api.dll
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---RdpEnable
| | | | | | reflective_dll.dll
| | | | | | SetRdpPort.ps1
| | | | | |
| | | | | +---Services
| | | | | | reflective_dll.dll
| | | | | | TransitEXE.exe
| | | | | |
| | | | | +---StartUp
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Task_Scheduler
| | | | | | reflective_dll.dll
| | | | | |
| | | | | \---Wmi
| | | | | Wmi_Persistence.ps1
| | | | |
| | | | +---AuthPromote
| | | | | | BadPotato.exe
| | | | | | cve-2014-4113.x64.dll
| | | | | | cve-2014-4113.x86.dll
| | | | | | cve-2015-1701.x64.dll
| | | | | | cve-2015-1701.x86.dll
| | | | | | cve-2016-0051.x86.dll
| | | | | | CVE-2020-0796.x64.dll
| | | | | | dazzleUP_Reflective_DLL.x64.dll
| | | | | | Invoke-EternalBlue.ps1
| | | | | | Invoke-MS16032.ps1
| | | | | | Invoke-MS16135.ps1
| | | | | | JuicyPotato.exe
| | | | | | JuicyPotato.x64.dll
| | | | | | JuicyPotato.x86.dll
| | | | | | ms15-051.exe
| | | | | | ms16-016.exe
| | | | | | ms16-032.exe
| | | | | | SharpBypassUAC.exe
| | | | | | SweetPotato.exe
| | | | | | Watson.exe
| | | | | |
| | | | | +---CVE-2021-1675
| | | | | | +---3.5
| | | | | | | SharpPrintNightmare.exe
| | | | | | |
| | | | | | \---4.5
| | | | | | SharpPrintNightmare.exe
| | | | | |
| | | | | \---res
| | | | | Ladon20.dat
| | | | | Ladon30.dat
| | | | | Ladon35.dat
| | | | | Ladon40.dat
| | | | |
| | | | +---BypassCxk
| | | | | adduser.exe
| | | | | Cl0neX.exe
| | | | | mimi.exe
| | | | | SharpUserAdd.exe
| | | | |
| | | | +---InfoCollect
| | | | | | AD.dll
| | | | | | AdFind.exe
| | | | | | Check-VM.ps1
| | | | | | Ladon.exe
| | | | | | LRC.exe
| | | | | | netview.exe
| | | | | | Powerview.ps1
| | | | | | SharpAVKB.exe
| | | | | | SharpChassisType.exe
| | | | | | SharpCheckInfo.exe
| | | | | | SharpClipHistory.exe
| | | | | | SharpDir.exe
| | | | | | SharpEDRChecker.exe
| | | | | | SharpEventLog.exe
| | | | | | SharpNetCheck.exe
| | | | | | SharpSQLDump.exe
| | | | | | SharpWebScan.exe
| | | | | |
| | | | | \---everything
| | | | | Everything.exe
| | | | | Everything.ini
| | | | |
| | | | +---IntrAgent
| | | | | +---x64
| | | | | | agent.exe
| | | | | | frpcx.exe
| | | | | | iox.exe
| | | | | | npc.exe
| | | | | |
| | | | | \---x86
| | | | | agent.exe
| | | | | frpcx.exe
| | | | | iox.exe
| | | | | npc.exe
| | | | |
| | | | +---IntrScan
| | | | | | SharpOXID-Find.exe
| | | | | | SharpSpray.exe
| | | | | | SharpWebScan.exe
| | | | | |
| | | | | +---x64
| | | | | | Allin.exe
| | | | | | cube.exe
| | | | | | fscan.exe
| | | | | |
| | | | | \---x86
| | | | | Allin.exe
| | | | | cube.exe
| | | | | fscan.exe
| | | | |
| | | | +---LateMovement
| | | | | | InternalMonologue.exe
| | | | | | MS14-068.exe
| | | | | | SharpDomainSpray.exe
| | | | | | SharpHound.exe
| | | | | | SharpShares.exe
| | | | | | sharpwmi.exe
| | | | | | SPNSearcher.exe
| | | | | | WMIHACKER.vbs
| | | | | |
| | | | | +---kekeo
| | | | | | +---samba
| | | | | | | lib_smb_pipe.c
| | | | | | | lib_smb_pipe_x64.so
| | | | | | | lib_smb_pipe_x86.so
| | | | | | |
| | | | | | +---Win32
| | | | | | | kekeo.exe
| | | | | | |
| | | | | | \---x64
| | | | | | 1.txt
| | | | | | kekeo.exe
| | | | | |
| | | | | \---ZeroLogon
| | | | | zerologon.x64.o
| | | | | zerologon.x86.o
| | | | |
| | | | +---PassCapture
| | | | | | BrowserGhost.exe
| | | | | | CatchChrome.exe
| | | | | | CredPhisher.exe
| | | | | | CVE-2021-36934.exe
| | | | | | FakeLogonScreenToFile.exe
| | | | | | InternalMonologue.exe
| | | | | | lazagne.exe
| | | | | | lock-screen.ps1
| | | | | | Minidump.exe
| | | | | | MiniDumpLsass.exe
| | | | | | navicatpwd.exe
| | | | | | Net-GPPPassword_dotNET_v2.exe
| | | | | | Safe360Browsergetpass.exe
| | | | | | SharpChromium.exe
| | | | | | SharpCloud.exe
| | | | | | SharpDecryptPwd.exe
| | | | | | SharpDecryptPwd40.exe
| | | | | | SharpWeb.exe
| | | | | | SharpWifiGrabber.exe
| | | | | |
| | | | | +---fakelogonscreen_trunk
| | | | | | | FakeLogonScreen.exe
| | | | | | | FakeLogonScreenToFile.exe
| | | | | | |
| | | | | | \---DOTNET35
| | | | | | FakeLogonScreen.exe
| | | | | | FakeLogonScreenToFile.exe
| | | | | |
| | | | | +---HackBrowserData
| | | | | | +---x64
| | | | | | | hack-browser-data.exe
| | | | | | |
| | | | | | \---x86
| | | | | | hack-browser-data.exe
| | | | | |
| | | | | \---LsassDump
| | | | | +---x64
| | | | | | LsassDump.exe
| | | | | |
| | | | | \---x86
| | | | | LsassDump.exe
| | | | |
| | | | \---RemoteLogin
| | | | CheckRdpStatus.ps1
| | | | EventLogFailed.ps1
| | | | EventLogSuccess.ps1
| | | | Invoke-WCMDump.ps1
| | | | KillEvenlogService.ps1
| | | | RegfDenyTSConnections.ps1
| | | | RegRdpPort.ps1
| | | | StartRdp.exe
| | | |
| | | +---OLa
| | | | | OLa.cna
| | | | |
| | | | |
| | | | +---modules
| | | | | AuthMaintain.cna
| | | | | bypass_tools.cna
| | | | | discovery.cna
| | | | | elevate.cna
| | | | | funny.cna
| | | | | Intranet_agent.cna
| | | | | Intranet_move.cna
| | | | | Intranet_scan.cna
| | | | | Passwd_Capture.cna
| | | | | trace_clean.cna
| | | | |
| | | | \---scripts
| | | | +---AuthMaintain
| | | | | +---AdUserApi
| | | | | | HaryyUser.exe
| | | | | |
| | | | | +---Exitservice
| | | | | | uinit.exe
| | | | | |
| | | | | +---Linkinfo
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Msdtc32
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Netapi32
| | | | | | api.dll
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Services
| | | | | | reflective_dll.dll
| | | | | | TransitEXE.exe
| | | | | |
| | | | | +---ShadowUser
| | | | | | scvhost.exe
| | | | | |
| | | | | +---StartUp
| | | | | | reflective_dll.dll
| | | | | |
| | | | | +---Task_Scheduler
| | | | | | reflective_dll.dll
| | | | | |
| | | | | \---Wmi
| | | | | Wmi_Persistence.ps1
| | | | |
| | | | +---bypass_tools
| | | | | adduser.exe
| | | | | mimi.exe
| | | | |
| | | | +---discovery-tools
| | | | | | AdFind.exe
| | | | | | browser.exe
| | | | | | Powerview.ps1
| | | | | | SharpAVKB.exe
| | | | | | SharpChassisType.exe
| | | | | | SharpCheckInfo.exe
| | | | | | SharpClipHistory.exe
| | | | | | SharpDecryptPwd.exe
| | | | | | SharpDir.exe
| | | | | | SharpEDRChecker.exe
| | | | | | SharpEventLog.exe
| | | | | | SharpSQLDump.exe
| | | | | | SharpWebScan.exe
| | | | | |
| | | | | +---everything
| | | | | | Everything.exe
| | | | | | Everything.ini
| | | | | |
| | | | | \---RAT
| | | | | sunloginpassword.exe
| | | | | Sunloginscreen.exe
| | | | | Sunloginscreentest.exe
| | | | | teamviewerpassword.exe
| | | | | TeamViewerscreen.exe
| | | | | Todeskscreen.exe
| | | | |
| | | | +---elevate
| | | | | | cve-2014-4113.x64.dll
| | | | | | cve-2014-4113.x86.dll
| | | | | | cve-2015-1701.x64.dll
| | | | | | cve-2015-1701.x86.dll
| | | | | | cve-2016-0051.x86.dll
| | | | | | CVE-2020-0796.x64.dll
| | | | | | FilelessUACBypass.ps1
| | | | | | Invoke-EventVwrBypass.ps1
| | | | | | Invoke-MS16032.ps1
| | | | | | Invoke-MS16135.ps1
| | | | | | Invoke-WScriptBypassUAC.ps1
| | | | | | JuicyPotato.x64.dll
| | | | | | JuicyPotato.x86.dll
| | | | | | potato.x64.dll
| | | | | | potato.x86.dll
| | | | | | UAC-TokenMagic.ps1
| | | | | | UACME.zip
| | | | | | uac_bypass_silentcleanup.exe
| | | | | |
| | | | | \---CVE-2021-1675
| | | | | +---3.5
| | | | | | SharpPrintNightmare.exe
| | | | | |
| | | | | \---4.5
| | | | | SharpPrintNightmare.exe
| | | | |
| | | | +---Intranet_agent
| | | | | frpcx.exe
| | | | | iox.exe
| | | | | nb.exe
| | | | | npc.exe
| | | | | SharpNetCheck.exe
| | | | |
| | | | +---Intranet_move
| | | | | | InternalMonologue.exe
| | | | | | SharpDomainSpray.exe
| | | | | | SharpHound.exe
| | | | | | SharpOXID-Find.exe
| | | | | | SharpShares.exe
| | | | | | sharpwmi.exe
| | | | | | SPNSearcher.exe
| | | | | | WMIHACKER.vbs
| | | | | |
| | | | | \---RDP
| | | | | | RegRdpPort.ps1
| | | | | | StartRdp.exe
| | | | | |
| | | | | \---SharpRDPThief
| | | | | EasyHook.dll
| | | | | EasyHook.xml
| | | | | EasyHook32.dll
| | | | | EasyHook32Svc.exe
| | | | | EasyHook64.dll
| | | | | EasyHook64Svc.exe
| | | | | EasyLoad32.dll
| | | | | EasyLoad64.dll
| | | | | RDPHook.dll
| | | | | RDPHook.pdb
| | | | | SharpRDPThief.exe
| | | | | SharpRDPThief.exe.config
| | | | | SharpRDPThief.pdb
| | | | | SharpRDPThief.vshost.exe
| | | | | SharpRDPThief.vshost.exe.config
| | | | | SharpRDPThief.vshost.exe.manifest
| | | | |
| | | | +---Intranet_scan
| | | | | | crack.exe
| | | | | | Fvuln.exe
| | | | | | SharpSpray.exe
| | | | | | SharpWebScan.exe
| | | | | |
| | | | | +---fscan
| | | | | | +---x64
| | | | | | | fscan.exe
| | | | | | |
| | | | | | \---x86
| | | | | | fscan.exe
| | | | | |
| | | | | \---TailorScan
| | | | | +---x64
| | | | | | TailorScan.exe
| | | | | |
| | | | | \---x86
| | | | | TailorScan.exe
| | | | |
| | | | \---Passwd_Capture
| | | | | BrowserGhost.exe
| | | | | CredPhisher.exe
| | | | | CVE-2021-36934.exe
| | | | | InternalMonologue.exe
| | | | | lazagne.exe
| | | | | lock-screen.ps1
| | | | | MiniDumpLsass.exe
| | | | | navicatpwd.exe
| | | | | Net-GPPPassword_dotNET_v2.exe
| | | | | SharpChromium.exe
| | | | | SharpCloud.exe
| | | | | SharpDecryptPwd.exe
| | | | | SharpDecryptPwd40.exe
| | | | | SharpWeb.exe
| | | | | SharpWifiGrabber.exe
| | | | |
| | | | +---fakelogonscreen_trunk
| | | | | | FakeLogonScreen.exe
| | | | | | FakeLogonScreenToFile.exe
| | | | | |
| | | | | \---DOTNET35
| | | | | FakeLogonScreen.exe
| | | | | FakeLogonScreenToFile.exe
| | | | |
| | | | +---HackBrowserData
| | | | | +---x64
| | | | | | hack-browser-data.exe
| | | | | |
| | | | | \---x86
| | | | | hack-browser-data.exe
| | | | |
| | | | \---LsassDump
| | | | +---x64
| | | | | LsassDump.exe
| | | | |
| | | | \---x86
| | | | LsassDump.exe
| | | |
| | | +---TaoWu
| | | | | TaoWu.cna
| | | | |
| | | | +---modules
| | | | | | about.cna
| | | | | | brute force.cna
| | | | | | credential access.cna
| | | | | | discovery.cna
| | | | | | entertainment.cna
| | | | | | Intranet penetration.cna
| | | | | | Intranet.cna
| | | | | | Lateral movement.cna
| | | | | | privilege escalation.cna
| | | | | | privilege.cna
| | | | | | RdpThief.cna
| | | | | | SharpDPAPI.cna
| | | | | | system.cna
| | | | | | Vulnerability.cna
| | | | | | win-notify.cna
| | | | | |
| | | | | \---aggressor
| | | | | spoolsystem.cna
| | | | |
| | | | \---script
| | | | | 0803.exe
| | | | | 360bowser.exe
| | | | | ATPMiniDump.exe
| | | | | blocketw.exe
| | | | | blue.exe
| | | | | BrowserGhost.exe
| | | | | BypassAddUser.exe
| | | | | certexp.exe
| | | | | chfs.exe
| | | | | ClearnEventRecordID.ps1
| | | | | ClearnIpAddress.ps1
| | | | | ClearnTempLog.ps1
| | | | | crack.exe
| | | | | CredPhisher.exe
| | | | | cve-2014-4113.x64.dll
| | | | | cve-2014-4113.x86.dll
| | | | | cve-2015-1701.x64.dll
| | | | | cve-2015-1701.x86.dll
| | | | | cve-2016-0051.x86.dll
| | | | | CVE-2020-0796.x64.dll
| | | | | CVE-2021-1675.x64.dll
| | | | | dazzleUP_Reflective_DLL.x64.dll
| | | | | DecryptAutoLogon.exe
| | | | | DecryptTeamViewer.exe
| | | | | dis_defender.exe
| | | | | EfsPotato.exe
| | | | | encode
| | | | | encode.exe
| | | | | EncryptedZIP.exe
| | | | | FakeLogonScreen.exe
| | | | | FullPowers.dll
| | | | | Gopher.exe
| | | | | GPSCoordinates.exe
| | | | | hack-browser-data.exe
| | | | | InternalMonologue.exe
| | | | | Invoke-EternalBlue.ps1
| | | | | Invoke-MS16032.ps1
| | | | | Invoke-MS16135.ps1
| | | | | Invoke-Phant0m.ps1
| | | | | iox.exe
| | | | | JuicyPotato.x64.dll
| | | | | JuicyPotato.x86.dll
| | | | | KillEvenlogService.ps1
| | | | | Ladon.exe
| | | | | Ladon1.exe
| | | | | lazagne.exe
| | | | | ListAllUsers.ps1
| | | | | ListLogged-inUsers.ps1
| | | | | ListRDPConnections.exe
| | | | | LocalSessionManager.ps1
| | | | | LPE_Reflect_Elevate.x64.dll
| | | | | MaceTrap.exe
| | | | | napwd.exe
| | | | | Net-GPPPassword.exe
| | | | | NoAmci.exe
| | | | | noNetApiAdd.exe
| | | | | NoPowerShell.exe
| | | | | nssm.exe
| | | | | phant0m-rdll.dll
| | | | | RdpThief_x64.tmp
| | | | | Recon-AD-AllLocalGroups.dll
| | | | | Recon-AD-Computers.dll
| | | | | Recon-AD-Domain.dll
| | | | | Recon-AD-Groups.dll
| | | | | Recon-AD-LocalGroups.dll
| | | | | Recon-AD-SPNs.dll
| | | | | Recon-AD-Users.dll
| | | | | ReflectiveDll.x64.dll
| | | | | RegRdpPort.ps1
| | | | | rpcscan.dll
| | | | | SafetyKatz.exe
| | | | | scout.exe
| | | | | scrying.exe
| | | | | Seatbelt.exe
| | | | | SessionGopher.ps1
| | | | | SessionSearcher.exe
| | | | | Sharp3389.exe
| | | | | SharpAVKB.exe
| | | | | SharpBypassUAC.exe
| | | | | SharpChassisType.exe
| | | | | SharpCheckInfo.exe
| | | | | SharpChromium.exe
| | | | | SharpClipHistory.exe
| | | | | SharpCloud.exe
| | | | | SharpCrashEventLog.exe
| | | | | SharpDecryptPwd.exe
| | | | | SharpDecryptPwd2.exe
| | | | | SharpDir.exe
| | | | | SharpDirLister.exe
| | | | | SharpDomainSpray.exe
| | | | | SharpDoor.exe
| | | | | SharpDPAPI.exe
| | | | | SharpDump.exe
| | | | | SharpEDRChecker.exe
| | | | | SharPersist.exe
| | | | | SharpEventLog.exe
| | | | | SharpExcelibur.exe
| | | | | SharpExec.exe
| | | | | SharpGetTitle.exe
| | | | | SharpGPOAbuse.exe
| | | | | SharpHide.exe
| | | | | SharpHound.exe
| | | | | SharpNetCheck.exe
| | | | | SharpOXID-Find.exe
| | | | | SharpSCshell.exe
| | | | | SharpShares.exe
| | | | | SharpSpray.exe
| | | | | SharpSpray1.exe
| | | | | SharpSQLDump.exe
| | | | | SharpSQLTools.exe
| | | | | SharpStay.exe
| | | | | SharpTask.exe
| | | | | SharpWeb.exe
| | | | | SharpWebScan.exe
| | | | | SharpWifiGrabber.exe
| | | | | sharpwmi.exe
| | | | | SharpXDecrypt.exe
| | | | | SharpZeroLogon.exe
| | | | | SharpZip.exe
| | | | | Shhmon.exe
| | | | | SolarFlare.exe
| | | | | SPNSearcher.exe
| | | | | SpoolTrigger.x64.dll
| | | | | SpoolTrigger.x86.dll
| | | | | Stealer.exe
| | | | | StickyNotesExtract.exe
| | | | | SweetPotato.exe
| | | | | Telemetry.exe
| | | | | Telemetry3.5.exe
| | | | | temp.exe
| | | | | Watson.exe
| | | | | WeblogicRCE.exe
| | | | | WireTap.exe
| | | | | WMIHACKER.vbs
| | | | |
| | | | +---RottenPotato
| | | | | x64.dll
| | | | | x86.dll
| | | | |
| | | | +---SharpDomainSpray
| | | | | SharpDomainSpray.exe
| | | | |
| | | | +---x64
| | | | | bypass.exe
| | | | | fscan.exe
| | | | | modify.exe
| | | | | nc.exe
| | | | | npc.exe
| | | | | PrintSpoofer.dll
| | | | | PrintSpoofer.exe
| | | | |
| | | | \---x86
| | | | bypass.exe
| | | | fscan.exe
| | | | modify.exe
| | | | npc.exe
| | | | PrintSpoofer.dll
| | | | PrintSpoofer.exe
| | | |
| | | \---XieGongZi
| | | | main.cna
| | | |
| | | +---dll
| | | +---exe
| | | | 1.jpg
| | | | AdFind.exe
| | | | get_all.exe
| | | | MS17-010-Nessus.exe
| | | | privilege_DarkSchtask.exe
| | | | PsLoggedon.exe
| | | | PVEFindADUser.exe
| | | | schtasks.vbs
| | | | SharpClipHistory.exe
| | | | SharpSQLTools.exe
| | | | SharpWebScan.exe
| | | | smb_t.exe
| | | | Telemetry.exe
| | | |
| | | +---modules
| | | | powershell相关.cna
| | | | RDP相关.cna
| | | | 信息收集.cna
| | | | 关于.cna
| | | | 内网探测.cna
| | | | 内网穿透.cna
| | | | 凭据获取.cna
| | | | 域渗透.cna
| | | | 娱乐.cna
| | | | 工作目录.cna
| | | | 权限提升.cna
| | | | 权限维持.cna
| | | | 用户相关.cna
| | | | 痕迹清除.cna
| | | | 远程文件下载.cna
| | | | 防火墙相关.cna
| | | |
| | | +---powershell
| | | | ASREPRoast.ps1
| | | | Check-VM.ps1
| | | | CheckRdpStatus.ps1
| | | | Discover-PSInterestingServices.ps1
| | | | Discover-PSMSExchangeServers.ps1
| | | | Discover-PSMSSQLServers.ps1
| | | | DomainPasswordSpray.ps1
| | | | EventLogFailed.ps1
| | | | EventLogSuccess.ps1
| | | | Find-PotentiallyCrackableAccounts.ps1
| | | | Get-DomainSpn.psm1
| | | | GetUserSPNs.ps1
| | | | Get_Port_Process.ps1
| | | | Invoke-ADSDPropagation.ps1
| | | | Invoke-EternalBlue.ps1
| | | | Invoke-EternalScan.ps1
| | | | Invoke-MS16032.ps1
| | | | Invoke-MS16135.ps1
| | | | Invoke-WCMDump.ps1
| | | | KillEvenlogService.ps1
| | | | PowerView.ps1
| | | | powerview2.ps1
| | | | RegfDenyTSConnections.ps1
| | | | RegRdpPort.ps1
| | | |
| | | \---zip
| | | RouterScan.zip
| | |
| | +---resources
| | | bdetails.txt
| | | bhelp.txt
| | | translation.txt
| | |
| | +---scripts
| | | default.cna
| | |
| | \---third-party
| | README.winvnc.txt
| | winvnc.x64.dll
| | winvnc.x86.dll
| |
| +---gorailgun
| | | gorailgun-1.4.5.exe
| | | railgun渗透工具使用说明书-1.4.4.pdf
| | |
| | +---conf
| | | data.db
| | |
| | \---modules
| | +---anxiliary
| | | \---antivrus
| | | av.json
| | | waf.json
| | |
| | +---exps
| | | \---dnslog
| | | Bash.txt
| | | dnslog-ping-timeout.ps1
| | | dnslog-ping.ps1
| | | Perl.txt
| | | Powershell.txt
| | | Python.txt
| | | readme.txt
| | |
| | \---gather
| | | cms_finger.db
| | |
| | +---brute_dict
| | | +---dict_cobaltstrike
| | | | dic_password_cobaltstrike.txt
| | | | dic_username_cobaltstrike.txt
| | | |
| | | +---dict_ftp
| | | | dic_password_ftp.txt
| | | | dic_username_ftp.txt
| | | |
| | | +---dict_memcache
| | | | dic_password_memcache.txt
| | | | dic_username_memcache.txt
| | | |
| | | +---dict_mongodb
| | | | dic_password_mongodb.txt
| | | | dic_username_mongodb.txt
| | | |
| | | +---dict_mssql
| | | | dic_password_mssql.txt
| | | | dic_username_mssql.txt
| | | |
| | | +---dict_mysql
| | | | dic_password_mysql.txt
| | | | dic_username_mysql.txt
| | | |
| | | +---dict_oracle
| | | | dic_password_oracle.txt
| | | | dic_username_oracle.txt
| | | | oracle_servicename.txt
| | | |
| | | +---dict_postgresql
| | | | dic_password_postgresql.txt
| | | | dic_username_postgresql.txt
| | | |
| | | +---dict_rdp
| | | | dic_password_rdp.txt
| | | | dic_username_rdp.txt
| | | |
| | | +---dict_redis
| | | | dic_password_redis.txt
| | | | dic_username_redis.txt
| | | |
| | | +---dict_smb
| | | | dic_password_smb.txt
| | | | dic_username_smb.txt
| | | |
| | | +---dict_ssh
| | | | dic_password_ssh.txt
| | | | dic_username_ssh.txt
| | | |
| | | +---dict_svn
| | | | dic_password_svn.txt
| | | | dic_username_svn.txt
| | | |
| | | +---dict_telnet
| | | | dic_password_telnet.txt
| | | | dic_username_telnet.txt
| | | |
| | | +---dict_tomcat
| | | | dic_password_tomcat.txt
| | | | dic_username_tomcat.txt
| | | |
| | | +---dict_vnc
| | | | dic_password_vnc.txt
| | | | dic_username_vnc.txt
| | | |
| | | +---dict_webauth
| | | | dic_password_webauth.txt
| | | | dic_username_webauth.txt
| | | |
| | | \---dict_wmi
| | | dic_password_wmi.txt
| | | dic_username_wmi.txt
| | |
| | \---dirscan
| | asp.txt
| | aspx.txt
| | back.txt
| | db.txt
| | dir.txt
| | dir_big.txt
| | jsp.txt
| | php.txt
| | py.txt
| | springboot.txt
| |
| +---ladon
| | | CABARC.EXE
| | | Ladon.exe
| | | Ladon.ps1
| | | Ladon40.exe
| | | Ladon48.exe
| | | Ladon9.1.4_min.ps1
| | | Ladon9.1.7_all.ps1
| | | LadonExp.exe
| | | LadonGUI.exe
| | | Newtonsoft.Json.dll
| | | SubDomain.dic
| | | update.txt
| | | wiki.txt
| | |
| | \---scripts
| | | fun.txt
| | | Ladon-cn.cna
| | | Ladon.cna
| | | Ladon.exe
| |
| +---quasar
| | | BouncyCastle.Crypto.dll
| | | client.bin
| | | Gma.System.MouseKeyHook.dll
| | | LICENSE
| | | Mono.Cecil.dll
| | | Mono.Cecil.Pdb.dll
| | | Mono.Cecil.Rocks.dll
| | | Open.Nat.dll
| | | protobuf-net.dll
| | | quasar.bat
| | | Quasar.Common.dll
| | | Quasar.exe
| | | Quasar.exe.config
| | | quasar.p12
| | | Quasar_zh-CHS.exe
| | | Quasar最新内部成员汉化版远控工具.rar
| | | Vestris.ResourceLib.dll
| | |
| | +---3rdPartyLicenses
| | | Be.HexEditor_license.txt
| | | BouncyCastle_license.html
| | | GlobalMouseKeyHook_license.txt
| | | Mono.Cecil_license.txt
| | | Open.Nat_license.txt
| | | protobuf-net_license.txt
| | | ResourceLib_license.txt
| | | SilkIcons_license.txt
| | |
| | \---Quasar最新内部成员汉化版远控
| | \---Quasar v1.4.0
| +---ruoji
| | re.txt
| | webshell_bypass_4.3.bat
| | webshell_bypass_4.3.py
| | webshell_bypass_4.3a.bat
| |
| +---Serein
| | | logo.ico
| | | requirements.txt
| | | Serein.bat
| | | Serein.py
| | | Serein1.bat
| | |
| | \---exp
| | | Apache_Hadoop_Yarn_RPC_RCE.py
| | | apache_spark_cve_2022_33891.py
| | | Citrix_rce_cve_2019_19781.py
| | | clickhouse_unauthorized_visit.py
| | | CVE_2020_25078.py
| | | CVE_2022_22954.py
| | | CVE_2022_23337.py
| | | CVE_2022_26134.py
| | | CVE_2022_29464.py
| | | CVE_2022_8515.py
| | | Dap_2020_anyfile_read_cve_2021_27250.py
| | | doccms_keyword_sql.py
| | | dvr_login_bypass.py
| | | E_Weaver_any_file_read.py
| | | f5_big_ip.py
| | | fikker_weak_password.py
| | | Fortigate_CVE_2018_13379.py
| | | Franklin_Fueling_Systems_anyfile_read_cve_2021_46417.py
| | | fumengyun_sql.py
| | | FW_Eoffice_unauthorized.py
| | | harbor.py
| | | hkv_rce.py
| | | iceWarp_webClient_rce.py
| | | kkFileView_readfile_CVE_2021_43734.py
| | | Landray_oa_treexml_rce.py
| | | magicflow_readfile.py
| | | metabase_readfile.py
| | | Microsoft_proxyshell_cve_2021_34473.py
| | | node_red_anyfile_read.py
| | | Rails_anyfile_read_cve_2019_5418.py
| | | Redis_auth_2022.py
| | | ruijie_admin_passwd_leak.py
| | | ruijie_phpinfo_leak.py
| | | Sapido_RCE.py
| | | SolarView_rce_CVE_2022_29303.py
| | | sonicwall_ssl_vpn.py
| | | sophos_firewall_rce_cve_2022_1040.py
| | | spring4shell_exp.py
| | | Tenda_W15E_config_leak.py
| | | Thinkphp_5_0_x_gethell.py
| | | VoIPmonitor_RCE_CVE_2021_30461.py
| | | VOS3000_readfile.py
| | | Weaver_HrmCareerApplyPerView_sql.py
| | | wordpress_any_file_read_CVE_2022_1119.py
| | | xiaomi_wifi_anyfile_read_cve_2019_18371.py
| | | xrk_rce.py
| | | yync_rce.py
| | | yyu8_testsql.py
| | | zabbix_auth_bypass.py
| | | zabbix_sql.py
| | | Zyxel_rce_CVE_2022_30525.py
| | |
| | \---__pycache__
| | Apache_Hadoop_Yarn_RPC_RCE.cpython-310.pyc
| | apache_spark_cve_2022_33891.cpython-310.pyc
| | Citrix_rce_cve_2019_19781.cpython-310.pyc
| | clickhouse_unauthorized_visit.cpython-310.pyc
| | CVE_2020_25078.cpython-310.pyc
| | CVE_2022_22954.cpython-310.pyc
| | CVE_2022_23337.cpython-310.pyc
| | CVE_2022_26134.cpython-310.pyc
| | CVE_2022_29464.cpython-310.pyc
| | CVE_2022_8515.cpython-310.pyc
| | Dap_2020_anyfile_read_cve_2021_27250.cpython-310.pyc
| | doccms_keyword_sql.cpython-310.pyc
| | dvr_login_bypass.cpython-310.pyc
| | E_Weaver_any_file_read.cpython-310.pyc
| | f5_big_ip.cpython-310.pyc
| | fikker_weak_password.cpython-310.pyc
| | Fortigate_CVE_2018_13379.cpython-310.pyc
| | Franklin_Fueling_Systems_anyfile_read_cve_2021_46417.cpython-310.pyc
| | fumengyun_sql.cpython-310.pyc
| | FW_Eoffice_unauthorized.cpython-310.pyc
| | harbor.cpython-310.pyc
| | hkv_rce.cpython-310.pyc
| | iceWarp_webClient_rce.cpython-310.pyc
| | kkFileView_readfile_CVE_2021_43734.cpython-310.pyc
| | Landray_oa_treexml_rce.cpython-310.pyc
| | magicflow_readfile.cpython-310.pyc
| | metabase_readfile.cpython-310.pyc
| | Microsoft_proxyshell_cve_2021_34473.cpython-310.pyc
| | node_red_anyfile_read.cpython-310.pyc
| | Rails_anyfile_read_cve_2019_5418.cpython-310.pyc
| | ruijie_admin_passwd_leak.cpython-310.pyc
| | ruijie_phpinfo_leak.cpython-310.pyc
| | Sapido_RCE.cpython-310.pyc
| | SolarView_rce_CVE_2022_29303.cpython-310.pyc
| | sonicwall_ssl_vpn.cpython-310.pyc
| | spring4shell_exp.cpython-310.pyc
| | Tenda_W15E_config_leak.cpython-310.pyc
| | Thinkphp_5_0_x_gethell.cpython-310.pyc
| | VoIPmonitor_RCE_CVE_2021_30461.cpython-310.pyc
| | VOS3000_readfile.cpython-310.pyc
| | Weaver_HrmCareerApplyPerView_sql.cpython-310.pyc
| | wordpress_any_file_read_CVE_2022_1119.cpython-310.pyc
| | xiaomi_wifi_anyfile_read_cve_2019_18371.cpython-310.pyc
| | xrk_rce.cpython-310.pyc
| | yync_rce.cpython-310.pyc
| | yyu8_testsql.cpython-310.pyc
| | zabbix_auth_bypass.cpython-310.pyc
| | zabbix_sql.cpython-310.pyc
| | Zyxel_rce_CVE_2022_30525.cpython-310.pyc
| |
| +---xray
| | module.xray.yaml
| | plugin.xray.yaml
| | start.bat
| | xray-license.lic
| | xray.yaml
| | xray_windows_amd64.exe
| | 运行Xray基础爬虫模式进行扫描.ps1
| |
| \---yanri
| yanri.bat
| yanri.exe
|
+---gui_scan
| | 2021-09-06-11-49-38.mv.db
| | 2021-09-06-11-49-38.trace.db
| | aksk_tool.jar
| | CAS_cc2_Exploit-1.0-SNAPSHOTv1.1-all.jar
| | CVE-2021-41773.exe
| | fastjson_exploit-1.0-SNAPSHOT-all.jar
| | Fckeditor辅助工具.exe
| | hikvision-decrypter.exe
| | jd-gui-1.6.6.jar
| | jd-gui.cfg
| | Liqunkit_tools.jar
| | MYExploit.jar
| | oracleShell.jar
| | Seay-Svn源代码泄露漏洞利用工具.exe
| | SeayDzend.exe
| | SJ-V1.9.jar
| | TDOA20210726.jar
| | X-GUI.exe
| | 暗月fck利用工具.exe
| | 深X服edr任意用户登陆检测工具.jar
| | 阿里Key命令执行Tools.exe
| |
| +---AliyunAkTools
| | AliyunAkTools.exe
| |
| +---bjx
| | | Polarscan.exe
| | | Uninstall.exe
| | | Uninstall.ini
| | |
| | \---配置文件
| | | log.txt
| | | user.ini
| | | 代理.txt
| | |
| | +---WEB
| | | | Error.html
| | | | fallback.css
| | | | jquery-1.7.1.min.js
| | | | selectivizr.js
| | | | style.css
| | | | WEB.rc
| | +---任务备份
| | | +---dat
| | | \---xls
| | +---任务计划
| | +---密码字典
| | | ftppass.txt
| | | ftpuser.txt
| | | pass.txt
| | | user.txt
| | |
| | +---崩溃备份
| | +---我的收藏
| | +---扫描备份
| | +---扫描报告
| | +---数据中心
| | | IP数据_01.txt
| | | IP数据_02.txt
| | | IP数据_03.txt
| | |
| | +---普通路径
| | | asp.txt
| | | ASPX.txt
| | | cfm.txt
| | | cgi.txt
| | | DIR.txt
| | | ewebeditor.txt
| | | FCKeditor.txt
| | | JSP.txt
| | | MDB.txt
| | | PHP.txt
| | | py.txt
| | | 压缩包.txt
| | | 备份.txt
| | | 高危.txt
| | |
| | +---漏洞盒子
| | | appcms.txt
| | | aspcms.txt
| | | C9静态.txt
| | | Discuz.txt
| | | dkcms.txt
| | | ECSHOP.txt
| | | espcms.txt
| | | FCKeditor编辑器.txt
| | | JoekoeCMS.txt
| | | phpcms.txt
| | | phpMyAdmin.txt
| | | phpweb.txt
| | | S2命令执行.txt
| | | shopex.txt
| | | ThinkPHP.txt
| | | wordpress.txt
| | | Z-BLOG.txt
| | | 乔客.txt
| | | 其他CMS.txt
| | | 动力.txt
| | | 动易.txt
| | | 动网.txt
| | | 千博.txt
| | | 南方数据.txt
| | | 夏茂OA.txt
| | | 天天团购.txt
| | | 子域名.txt
| | | 汇成cms.txt
| | | 科讯.txt
| | | 织梦.txt
| | | 西部商务.txt
| | | 迪科.txt
| | | 逐浪cms.txt
| | | 风讯.txt
| | | 风讯foosunCMS.txt
| | |
| | \---爬虫设定
| | XSS跨站脚本.txt
| | 一句话木马.txt
| | 上传关键字.txt
| | 允许爬行文件格式.txt
| | 登录关键字.txt
| | 自定义关键字.txt
| | 资源收集.txt
| |
| +---CORScanner-master
| | | .gitignore
| | | cors_scan.bat
| | | cors_scan.py
| | | cors_scan1.bat
| | | LICENSE
| | | origins.json
| | | requirements.txt
| | | top_100_domains.txt
| +---exp2021
| | 2021年部分漏洞整合检测工具.bat
| | exp2021.exe
| |
| +---FastJson_JackSon
| | FastJson_JackSon 使用说明.jpg
| | FastJson_JackSon.jar
| |
| +---FrameScan-GUI
| | | FrameScan-GUI-v1.3.8.zip
| | | FrameScan-GUI.exe
| | +---Modules
| | | | BaseInfo.py
| | | | CyberCalculate.py
| | | | ProbeDefine.py
| | | | PythonHighlighter.py
| | | | Vuln_Exp.py
| | | | Vuln_Scanner.py
| | |
| | +---Plugins
| | | +---Exp_Plugins
| | | | shell.asp
| | | | shell.aspx
| | | | shell.jsp
| | | | shell.jspx
| | | | shell.php
| | | |
| | | +---Plugins_Template
| | | | Plugins_漏洞插件模板.py
| | | |
| | | \---Vuln_Plugins
| | | \---test
| | | | Plugins_test.py
| | |
| |
| +---goby
| | +---goby-win-x64-2.0.5
| | | | Goby.exe
| | | |
| | | +---config
| | | | config.json
| | | +---extensions
| | | +---golib
| | | | | extensionDB.sqlite3
| | | | | ftp_user_pass.dict
| | | | | goby-cmd.exe
| | | | | mssql_user_pass.dict
| | | | | mysql_user_pass.dict
| | | | | postgres_user_pass.dict
| | | | | rdp_user_pass.dict
| | | | | scan.sqlite3
| | | | | scan.sqlite3-shm
| | | | | scan.sqlite3-wal
| | | | | smb_user_pass.dict
| | | | | snmp_pass.dict
| | | | | ssh_user_pass.dict
| | | | | tomcat_user_pass.dict
| | | | | useOfLegalStatements.txt
| | | | | user_pass.dict
| | | | | vnc_user_pass.dict
| | | | |
| | | | +---exploits
| | | | | +---system
| | | | | \---user
| | | | | | 360_TianQing_ccid_SQL_injectable.json
| | | | | | admin-file-search.yaml
| | | | | |
| | | | | +---goby_pocs
| | | | | | 360_TianQing_ccid_SQL_injectable.json
| | | | | | 360_Tianqing_database_information_disclosure.json
| | | | | | AceNet_AceReporter_Report_component_Arbitrary_file_download.go
| | | | | | Active_UC_index.action_RCE.json
| | | | | | ACTI_camera_images_File_read.go
| | | | | | Adobe_ColdFusion_LFI_CVE-2010-2861.json
| | | | | | ADSelfService_Plus_RCE_CVE-2021-40539.json
| | | | | | ADSelfService_Plus_RCE_CVE_2021_40539.json
| | | | | | Adslr_Enterprise_online_behavior_management_system_Information_leak.json
| | | | | | Adslr_Enterprise_online_behavior_management_system_Information_leakage.json
| | | | | | Alibaba Nacos 控制台默认弱口令.json
| | | | | | Alibaba Nacos 未授权访问漏洞.json
| | | | | | alibaba_canal_default_password.json
| | | | | | Alibaba_Nacos_Add_user_not_authorized.json
| | | | | | Alibaba_Nacos_Default_password.json
| | | | | | Ametys_CMS_infoleak_CVE_2022_26159.json
| | | | | | Apache ActiveMQ Console控制台弱口令.json
| | | | | | Apache Cocoon Xml 注入 CVE-2020-11991.json
| | | | | | Apache Kylin Console 控制台弱口令.json
| | | | | | Apache Kylin 未授权配置泄露 CVE-2020-13937.json
| | | | | | Apache Solr Log4j JNDI RCE.go
| | | | | | Apache Solr任意文件读取漏洞.json
| | | | | | Apache_2.4.49_Path_Traversal_CVE_2021_41773.json
| | | | | | Apache_2.4.49_RCE_CVE_2021_41773_and_2.4.50_CVE_2021_42013.json
| | | | | | Apache_ActiveMQ_Console_Weak_Password.json
| | | | | | Apache_ActiveMQ_default_admin_account.json
| | | | | | Apache_Airflow_Unauthorized.json
| | | | | | Apache_APISIX_Admin_API_Default_Token_CVE_2020_13945.json
| | | | | | Apache_APISIX_Dashboard_API_Unauthorized_Access_CVE-2021-45232.json
| | | | | | Apache_APISIX_Dashboard_CVE_2021_45232.json
| | | | | | Apache_APISIX_Dashboard_RCE_CVE_2021_45232.json
| | | | | | Apache_Cocoon_XML_Injection_CVE_2020_11991.json
| | | | | | Apache_CouchDB_Remote_Privilege_Escalation_CVE-2017-12635.json
| | | | | | Apache_CouchDB_Unauth.json
| | | | | | Apache_Druid_Abritrary_File_Read_CVE-2021-36749.json
| | | | | | Apache_Druid_Abritrary_File_Read_CVE_2021_36749.json
| | | | | | Apache_Druid_Arbitrary_File_Read_CVE_2021_36749.json
| | | | | | Apache_Druid_Log4shell_CVE-2021-44228.json
| | | | | | Apache_Druid_Log4shell_CVE_2021_44228.json
| | | | | | Apache_Dubbo_Admin_Default_Password.json
| | | | | | Apache_Flink_CVE_2020_17519.json
| | | | | | Apache_HTTP_Server_2.4.48_mod_proxy_SSRF_CVE_2021_40438.json
| | | | | | Apache_HTTP_Server_2.4.49_2.4.50_Path_Traversal_CVE_2021_42013.json
| | | | | | Apache_HTTP_Server_2.4.49_Path_Traversal_CVE_2021_41773.json
| | | | | | Apache_HTTP_Server_2.4.49_RCE_CVE_2021_41773.json
| | | | | | Apache_HTTP_Server_Arbitrary_File_Read_CVE_2021_41773.json
| | | | | | Apache_HTTP_Server_SSRF_CVE-2021-40438.json
| | | | | | Apache_HTTP_Server_SSRF_CVE_2021_40438.json
| | | | | | Apache_JSPWiki_Log4shell_CVE-2021-44228_(1).json
| | | | | | Apache_JSPWiki_Log4shell_CVE-2021-44228_(2).json
| | | | | | Apache_JSPWiki_Log4shell_CVE_2021_44228_1.json
| | | | | | Apache_JSPWiki_Log4shell_CVE_2021_44228_2.json
| | | | | | Apache_Kylin_Console_Default_password.json
| | | | | | Apache_Kylin_Unauthorized_configuration_disclosure.json
| | | | | | Apache_OFBiz_Log4shell_CVE-2021-44228.json
| | | | | | Apache_OFBiz_Log4shell_CVE_2021_44228.json
| | | | | | Apache_ShenYu_Admin_Unauth_Access_CVE_2022_23944.json
| | | | | | Apache_SkyWalking_Log4shell_CVE-2021-44228.json
| | | | | | Apache_SkyWalking_Log4shell_CVE_2021_44228.json
| | | | | | Apache_Solr_Arbitrary_File_Read.json
| | | | | | Apache_Solr_Log4j2CVE_2021_44228.json
| | | | | | Apache_Solr_RemoteStreaming_File_Read.json
| | | | | | Apache_Struts2_S2_053_RCE_CVE_2017_12611.json
| | | | | | Apache_Struts2_S2_059_RCE_CVE_2019_0230.json
| | | | | | Apache_Struts2_S2_062_RCE_CVE_2021_31805.json
| | | | | | Aspcms_Backend_Leak.json
| | | | | | AspCMS_commentList.asp_SQLinjection_vulnerability.json
| | | | | | Atlassian Jira 信息泄露漏洞 CVE-2020-14181.json
| | | | | | Atlassian_Confluence_OGNL_injection_CVE_2021_26084.json
| | | | | | Atlassian_Confluence_OGNL_Injection_RCE_CVE_2022_26134.json
| | | | | | Atlassian_Confluence_Webwork_OGNL_Inject_CVE_2022_26134.go
| | | | | | Atlassian_Jira_Path_Traversal_CVE_2021_26086.json
| | | | | | Atlassian_Jira_Seraph_Authentication_bypass_CVE_2022_0540.json
| | | | | | Atlassian_Jira_user_information_disclosure.json
| | | | | | Atlassian_Jira_user_information_disclosure_CVE_2020_14181.json
| | | | | | AVCON6_org_execl_download.action_file_down.json
| | | | | | BigAnt_Server_v5.6.06_Path_Traversal_CVE_2022_23347.json
| | | | | | BSPHP_index.php_unauthorized_access_information.json
| | | | | | Cacti_Weathermap_File_Write.json
| | | | | | Casdoor_1.13.0_SQL_InjectionCVE_2022_24124.json
| | | | | | Cerebro_request_SSRF.json
| | | | | | chanjet_CRM_get_usedspace.php_sql_injection.json
| | | | | | Chanjet_CRM_get_usedspace.php_sql_injection_CNVD_2021_12845.json
| | | | | | China_Mobile_Yu_routed_the_login_bypass.json
| | | | | | China_Mobile_Yu_Routing_ExportSettings.sh_Info_Leak_CNVD_2020_67110.json
| | | | | | China_Mobile_Yu_Routing_Login_Bypass.json
| | | | | | China_Mobile_Yu_Routing_Sensitive_Information_Leaks_Vulnerability.json
| | | | | | Citrix_unauthenticated_LFI_CVE-2020-8193.json
| | | | | | Citrix_Unauthorized_CVE_2020_8193.json
| | | | | | ClickHouse_SQLI.json
| | | | | | ClusterEngineV4.0_RCE_.json
| | | | | | ClusterEngine_V4.0_Shell_cluster_RCE.json
| | | | | | CmsEasy_crossall_act.php_SQL_injection_vulnerability.json
| | | | | | Coldfusion_LFI_CVE_2010_2861.json
| | | | | | Confluence_RCE_CVE_2021_26084.json
| | | | | | Consul_Rexec_RCE.json
| | | | | | Coremail_configuration_information_disclosure.json
| | | | | | Coremail_Config_Disclosure.json
| | | | | | CouchCMS_Infoleak_CVE-2018-7662.json
| | | | | | Couchdb_Add_User_Not_Authorized_CVE_2017_12635.json
| | | | | | Couchdb_Unauth.json
| | | | | | Couch_CMS_Infoleak_CVE_2018_7662.json
| | | | | | CraftCMS_Seomatic_RCE_CVE_2020_9597.json
| | | | | | CraftCMS_SEOmatic_Server-Side_Template_Injection_CVE-2020-9597.json
| | | | | | CVE_2018_19367_.json
| | | | | | cve_2022_1388_goby.json
| | | | | | CVE_2022_22947.json
| | | | | | D-Link AC集中管理系统默认弱口令.json
| | | | | | D-Link DCS系列监控 CNVD-2020-25078.json
| | | | | | D-Link DCS系列监控 账号密码信息泄露漏洞 CNVD-2020-25078.json
| | | | | | D-Link_AC_management_system_Default_Password.json
| | | | | | D-Link_DCS_2530L_Administrator_password_disclosure_CVE_2020_25078.json
| | | | | | D-Link_DIR-850L_Info_Leak.json
| | | | | | D-Link_DIR_868L_x_DIR_817LW_Info_Leak_CVE_2019_17506.json
| | | | | | D-Link_Info_Leak_CVE-2019-17506.json
| | | | | | D-Link_ShareCenter_DNS_320_RCE.json
| | | | | | dahua_DSS_Arbitrary_file_download.json
| | | | | | dahua_DSS_Arbitrary_file_download_cnvd_2020_61986.go
| | | | | | Datang_AC_Default_Password.json
| | | | | | DedeCMS_Carbuyaction_FileInclude.json
| | | | | | DedeCMS_InfoLeak_CVE-2018-6910.json
| | | | | | DedeCMS_InfoLeak_CVE_2018_6910.json
| | | | | | Discuz!ML_3.x_RCE_CNVD-2019-22239.json
| | | | | | Discuz_ML_3.x_RCE__CNVD_2019_22239.json
| | | | | | Discuz_RCE_WOOYUN_2010_080723.json
| | | | | | Discuz_v72_SQLI.json
| | | | | | Discuz_Wechat_Plugins_Unauth.json
| | | | | | Dlink_850L_Info_Leak.json
| | | | | | Dlink_Info_Leak_CVE_2019_17506.json
| | | | | | Dlink_RCE_CVE_2019_16920.json
| | | | | | DocCMS_keyword_SQL_injection_Vulnerability.json
| | | | | | Docker_Registry_API_Unauth.json
| | | | | | DotCMS_Arbitrary_File_Upload_CVE_2022_26352.json
| | | | | | Dubbo_Admin_Default_Password.json
| | | | | | D_Link_AC_Centralized_management_system__Default_weak_password.json
| | | | | | D_Link_DC_Disclosure_of_account_password_information.json
| | | | | | D_Link_Dir_645_getcfg.php_Account_password_disclosure_CVE_2019_17506.go
| | | | | | D_Link_DIR_868L_getcfg.php_Account_password_leakage.json
| | | | | | D_Link_ShareCenter_DNS_320_RCE.json
| | | | | | D_Link_ShareCenter_DNS_320_system_mgr.cgi_RCE.go
| | | | | | Elasticsearch_Remote_Code_Execution_CVE_2014_3120.go
| | | | | | Elasticsearch_Remote_Code_Execution_CVE_2015_1427.go
| | | | | | ESAFENET_DLP_dataimport_RCE.go
| | | | | | Eyou_Mail_system_RCE.json
| | | | | | Eyou_Mail_System_RCE_CNVD_2021_26422.json
| | | | | | F5_BIG_IP_iControl_REST_API_auth_bypass_CVE_2022_1388.json
| | | | | | F5_BIG_IP_iControl_REST_Unauthenticated_RCE_CVE_2021_22986.json
| | | | | | F5_BIG_IP_login_bypass_CVE_2022_1388.go
| | | | | | F5_BIG_IP_RCE_CVE_2021_22986_exp.json
| | | | | | fahuo100_sql_injection_CNVD_2021_30193.json
| | | | | | Fastmeeting_Arbitrary_File_Read.json
| | | | | | feishimei_struts2_remote_code.json
| | | | | | FineReport_Directory_traversal.json
| | | | | | FineReport_v8.0_Arbitrary_file_read_.json
| | | | | | FineReport_v8.0_Fileread_CNVD_2018_04757.json
| | | | | | FineReport_v8.0_v9.0_Directory_Traversal.json
| | | | | | FineReport_v9_Arbitrary_File_Overwrite.json
| | | | | | Finetree_5MP_default_password_or_Unauthorized_user_added.json
| | | | | | Finetree_5MP_Network_Camera_Default_Login_unauthorized_user_add.json
| | | | | | firewall_Leaked_user_name_and_password.json
| | | | | | FLIR_AX8_Arbitrary_File_Download_Vulnerability_CNVD-2021-39018.go
| | | | | | ForgeRock_AM_RCE_CVE_2021_35464.go
| | | | | | fumengyun AjaxMethod.ashx SQL injection.json
| | | | | | GitLab Graphql邮箱信息泄露漏洞 CVE-2020-26413.json
| | | | | | GitLab_Graphql_Email_information_disclosure.json
| | | | | | GitLab_Graphql_Email_information_disclosure_CVE_2020_26413.json
| | | | | | GitLab_RCE_CVE-2021-22205.json
| | | | | | Gitlab_RCE_CVE_2021_22205.json
| | | | | | GitLab_SSRF_CVE_2021_22214.json
| | | | | | GoCD_Arbitrary_file_reading_CVE_2021_43287.json
| | | | | | GoCD_Unauthorized_Path_Traversal_CVE_2021_43287.json
| | | | | | Grafana_Angularjs_Rendering_XSS_CVE_2021_41174.json
| | | | | | Grafana_Arbitrary_file_read.json
| | | | | | Grafana_Plugins_Arbitrary_File_Read.json
| | | | | | Grafana_v8.x_Arbitrary_File_Read_CVE_2021_43798.json
| | | | | | H3C_HG659_lib_File_read.go
| | | | | | H3C_IMC_dynamiccontent.properties.xhtm_RCE.go
| | | | | | H3C_IMC_RCE.json
| | | | | | H3C_Next_generation_firewall_File_read.go
| | | | | | H3C_SecPath_Operation_Login_bypass.go
| | | | | | H5S_CONSOLE_Video_Platform_GetSrc_Information_Leak_CNVD_2021_25919.json
| | | | | | H5S_video_platform_GetSrc_information_leakage.json
| | | | | | H5S_video_platform_GetUserInfo_Account_password_leakage.json
| | | | | | H5S_Video_Platform_GetUserInfo_Info_Leak_CNVD_2021_35567.json
| | | | | | HanWang_Time_Attendance_SQL_injection.go
| | | | | | HEJIA_PEMS_SystemLog.cgi_Arbitrary_file_download.go
| | | | | | HIKVISION 视频编码设备接入网关 任意文件下载.json
| | | | | | HIKVISION.json
| | | | | | Hikvision_RCE_CVE_2021_36260.json
| | | | | | Hikvision_Unauthenticated_RCE_CVE-2021-36260.json
| | | | | | HIKVISION_Video_coding_equipment_Download_any_file.json
| | | | | | Hikvision_Video_Encoding_Device_Access_Gateway_Any_File_Download.json
| | | | | | Holographic_AI_network_operation_and_maintenance_platform_RCE.go
| | | | | | HotelDruid_Hotel_Management_Software_v3.0.3_XSS_CVE_2022_26564.json
| | | | | | Hsmedia_Hgateway_Default_account.json
| | | | | | huatiandongliOA_8000workFlowService_SQLinjection.json
| | | | | | Huijietong_cloud_video_fileDownload_File_read.go
| | | | | | Huijietong_cloud_video_list_Information_leakage.go
| | | | | | IceWarp_WebClient_basic_RCE.json
| | | | | | IFW8_Enterprise_router_Password_leakage_.json
| | | | | | IFW8_Router_ROM_v4.31_Credential_Discovery_CVE_2019_16313.json
| | | | | | IRDM4000_Smart_station_Unauthorized_access.json
| | | | | | JEEWMS_Arbitrary_File_Read_Vulnerability.go
| | | | | | Jellyfin_10.7.0_Unauthenticated_Abritrary_File_Read_CVE_2021_21402.json
| | | | | | Jellyfin_10.7.2_SSRF_CVE-2021-29490.json
| | | | | | Jellyfin_Audio_File_read_CVE_2021_21402.go
| | | | | | Jellyfin_prior_to_10.7.0_Unauthenticated_Arbitrary_File_Read_CVE_2021_21402.json
| | | | | | Jellyfin_SSRF_CVE_2021_29490.json
| | | | | | Jetty_WEB_INF_FileRead_CVE_2021_28169.json
| | | | | | Jetty_WEB_INF_FileRead_CVE_2021_34429.json
| | | | | | JingHe_OA_C6_Default_password.json
| | | | | | JingHe_OA_download.asp_File_read.go
| | | | | | Jinher_OA_C6_download.jsp_Arbitrary_file_read.json
| | | | | | JinHe_OA_C6_Default_password.json
| | | | | | JinHe_OA_C6_download.jsp_Arbitrary_fileread.json
| | | | | | Jinshan_V8.json
| | | | | | Jitong_EWEBS_arbitrary_file_read.json
| | | | | | Jitong_EWEBS_Fileread.json
| | | | | | Jitong_EWEBS_phpinfo_leak.json
| | | | | | JQuery_1.7.2Version_site_foreground_arbitrary_file_download.json
| | | | | | JQuery_1.7.2_Filedownload.json
| | | | | | KEDACOM_MTS_transcoding_server_Arbitrary_file_download_CNVD_2020_48650.json
| | | | | | KEDACOM_MTS_transcoding_server_Fileread_CNVD_2020_48650.json
| | | | | | Kingdee_EAS_server_file_Directory_traversal.go
| | | | | | Kingsoft_V8_Arbitrary_file_read.json
| | | | | | Kingsoft_V8_Default_weak_password.json
| | | | | | Kingsoft_V8_Terminal_Security_System_Default_Login_CNVD_2021_32425.json
| | | | | | Kingsoft_V8_Terminal_Security_System_Fileread.json
| | | | | | Konga_Default_JWT_KEY.json
| | | | | | Kyan.json
| | | | | | Kyan_Account_password_leak.json
| | | | | | Kyan_design_account_password_disclosure.json
| | | | | | Kyan_network_monitoring_device_account_password_leak.json
| | | | | | Kyan_network_monitoring_device_run.php_RCE.json
| | | | | | Kyan_run.php_RCE.json
| | | | | | landray_OA_Arbitrary_file_read.json
| | | | | | Landray_OA_custom.jsp_Fileread.json
| | | | | | landray_oa_treexml_rce.go
| | | | | | LanhaiZuoyue_system_debug.php_RCE.go
| | | | | | LanhaiZuoyue_system_download.php_File_read.go
| | | | | | Lanproxy 目录遍历漏洞 CVE-2021-3019.json
| | | | | | Lanproxy_Arbitrary_File_Read_CVE_2021_3019.json
| | | | | | Lanproxy_Directory_traversal_CVE_2021_3019.json
| | | | | | Laravel .env 配置文件泄露 CVE-2017-16894.json
| | | | | | Laravel_.env_configuration_file_leaks_(CVE-2017-16894).json
| | | | | | Laravel_.env_configuration_file_leaks_CVE_2017_16894.json
| | | | | | Leadsec_ACM_infoleak_CNVD-2016-08574.json
| | | | | | Leadsec_ACM_information_leakage_CNVD_2016_08574.json
| | | | | | Longjing_Technology_BEMS_API_1.21_Remote_Arbitrary_File_Download.go
| | | | | | mallgard.json
| | | | | | Mallgard_Firewall_Default_Login_CNVD_2020_73282.json
| | | | | | Many_network_devices_have_arbitrary_file_downloads.go
| | | | | | Many_network_devices_have_password_leaks.go
| | | | | | MessageSolution 邮件归档系统EEA 信息泄露漏洞 CNVD-2021-10543.json
| | | | | | MessageSolution_EEA_information_disclosure.json
| | | | | | MessageSolution_EEA_information_disclosure_CNVD_2021_10543.json
| | | | | | Metabase_geojson_Arbitrary_file_reading_CVE_2021_41277.json
| | | | | | Metabase_Geojson_Arbitrary_File_Read_CVE-2021-41277.json
| | | | | | Metabase_Geojson_Arbitrary_File_Read_CVE_2021_41277.json
| | | | | | Microsoft Exchange SSRF漏洞 CVE-2021-26885.json
| | | | | | Microsoft_Exchange_Server_SSRF_CVE_2021_26885.json
| | | | | | Micro_module_monitoring_system_User_list.php_information_leakage.json
| | | | | | MinIO_Browser_API_SSRF_CVE_2021_21287.json
| | | | | | MobileIron_Log4shell_CVE-2021-44228.json
| | | | | | MobileIron_Log4shell_CVE_2021_44228.json
| | | | | | MPSec_ISG1000_Gateway_Filedownload_CNVD_2021_43984.json
| | | | | | MPSec_ISG1000_Security_Gateway_Arbitrary_File_Download_Vulnerability.json
| | | | | | Node-RED_ui_base_Arbitrary_File_Read_CVE-2021-3223.json
| | | | | | Node.js_Path_Traversal_CVE_2017_14849.json
| | | | | | Node_RED_ui_base_Arbitrary_File_Read.json
| | | | | | Node_red_UI_base_Arbitrary_File_Read_Vulnerability_CVE_2021_3223.go
| | | | | | nsoft_EWEBS_casmain.xgi_File_read.go
| | | | | | NVS3000_integrated_video_surveillance_platform_is_not_accessible.go
| | | | | | OpenSNS_Application_ShareController.class.php__remote_command_execution_vulnerability.json
| | | | | | OpenSNS_RCE.json
| | | | | | Oracle_Weblogic_LDAP_RCE_CVE_2021_2109.json
| | | | | | Oracle_Weblogic_SearchPublicRegistries.jsp_SSRF_CVE_2014_4210.json
| | | | | | Oracle_WebLogic_Server_Path_Traversal_CVE_2022_21371.json
| | | | | | Oray_Sunlogin_RCE_CNVD_2022_03672_CNVD_2022_10270.json
| | | | | | Panabit_Application_Gateway_ajax_top_backstage_RCE.go
| | | | | | Panabit_iXCache_ajax_cmd_backstage_RCE.go
| | | | | | Panabit_Panalog_cmdhandle.php_backstage_RCE.go
| | | | | | php8.1backdoor.json
| | | | | | PHP_8.1.0-dev_Zerodium_Backdoor_RCE.json
| | | | | | Portainer_Init_Deploy_CVE_2018_19367.json
| | | | | | qilaiOA_messageurl.aspx_SQLinjection.json
| | | | | | qilaiOA_treelist.aspx_SQLinjection.json
| | | | | | Qilai_OA_CloseMsg.aspx_SQL_injection.go
| | | | | | red_fan_OA_hospital_ioFileExport.aspx_file_read.json
| | | | | | RG_UAC.json
| | | | | | Riskscanner_list_SQL_injection.json
| | | | | | Ruijie_Networks_EWEB_Network_Management_System_RCE_CNVD_2021_09650.json
| | | | | | Ruijie_RG_UAC_Password_leakage_CNVD_2021_14536.json
| | | | | | Ruijie_Smartweb_Default_Password_CNVD_2020_56167.json
| | | | | | Ruijie_Smartweb_Management_System_Password_Information_Disclosure_CNVD_2021_17369.json
| | | | | | Ruijie_smartweb_password_information_disclosure.json
| | | | | | Ruijie_smartweb_weak_password.json
| | | | | | RuoYi_Druid_Unauthorized_access.json
| | | | | | Samsung_WLAN_AP_RCE.json
| | | | | | Samsung_WLAN_AP_WEA453e_RCE.json
| | | | | | Samsung_WLAN_AP_wea453e_router_RCE.json
| | | | | | sangfor_Behavior_perception_system_c.php_RCE.json
| | | | | | SDWAN_Smart_Gateway_Default_Password.json
| | | | | | SDWAN_smart_gateway_weak_password.json
| | | | | | Security_Devices_Hardcoded_Password.json
| | | | | | SECWORLD_Next_generation_firewall_pki_file_download_File_read.go
| | | | | | Seeyon_OA_A6_DownExcelBeanServlet_User_information_leakage.json
| | | | | | Seeyon_OA_A6_initDataAssess.jsp_User_information_leakage.json
| | | | | | Seeyon_OA_A6_setextno.jsp_SQL_injection.json
| | | | | | Seeyon_OA_A6_test.jsp_SQL_injection.json
| | | | | | Seeyon_OA_A6__Disclosure_of_database_sensitive_information.json
| | | | | | Seeyon_OA_A8_m_Information_leakage.json
| | | | | | Selea_OCR_ANPR_get_file.php_File_read.go
| | | | | | Selea_OCR_ANPR_SeleaCamera_File_read.go
| | | | | | Shenzhen_West_dieter_Technology_Co_LTD_CPE_WiFi__ping_RCE.go
| | | | | | Shenzhen_West_dieter_Technology_Co_LTD_CPE_WiFi__tracert_RCE.go
| | | | | | ShiziyuCms_ApiController.class.php_SQL_injection.go
| | | | | | ShiziyuCms_ApiController.class.php_SQL_injection.go.json
| | | | | | ShiziyuCms_ApigoodsController.class.php_SQL_injection.go
| | | | | | ShiziyuCms_ApigoodsController.class.php_SQL_injection.go.json
| | | | | | ShiziyuCms_wxapp.php_File_update.go
| | | | | | ShopXO_download_Arbitrary_file_read_CNVD_2021_15822.json
| | | | | | ShopXO_download_File_read_CNVD_2021_15822.go
| | | | | | ShopXO_Fileread_CNVD_2021_15822.json
| | | | | | showDocGo.go
| | | | | | showDocJson.go
| | | | | | shtermQiZhi_Fortress_Arbitrary_User_Login.json
| | | | | | Shterm_QiZhi_Fortress_Unauthorized_Access_CNVD_2019_27717.json
| | | | | | SonarQube_search_projects_information.json
| | | | | | SonarQube_unauth_CVE-2020-27986.json
| | | | | | SonarQube_unauth_CVE_2020_27986.json
| | | | | | SonicWall SSL-VPN 远程命令执行漏洞.json
| | | | | | Sonicwall_SSLVPN_ShellShock_RCE.json
| | | | | | SonicWall_SSL_VPN_RCE.json
| | | | | | SpiderFlow_save__remote_code.json
| | | | | | SPON_IP_network_intercom_broadcast_system_exportrecord.php_any_file_download.go
| | | | | | SPON_IP_network_intercom_broadcast_system_getjson.php_Arbitrary_file_read.go
| | | | | | SPON_IP_network_intercom_broadcast_system_ping.php_RCE.go
| | | | | | SPON_IP_network_intercom_broadcast_system_rj_get_token.php_any_file_read.go
| | | | | | Spring_Boot_Actuator_Logview_Path_Traversal_CVE_2021_21234.json
| | | | | | Spring_boot_actuator_unauthorized_access.json
| | | | | | Spring_Cloud_Function_SpEL_RCE_CVE_2022_22963.json
| | | | | | Spring_Cloud_Gateway_Actuator_API_SpEL_Code_Injection_CVE_2022_22947.json
| | | | | | Spring_Framework_Data_Binding_Rules_Spring4Shell_RCE_CVE_2022_22965.json
| | | | | | Struts2_Log4Shell_CVE-2021-44228_(1).json
| | | | | | Struts2_Log4Shell_CVE-2021-44228_(2).json
| | | | | | Struts2_Log4Shell_CVE-2021-44228_(3).json
| | | | | | Struts2_Log4Shell_CVE_2021_44228_1.json
| | | | | | Struts2_Log4Shell_CVE_2021_44228_2.json
| | | | | | Struts2_Log4Shell_CVE_2021_44228_3.json
| | | | | | TamronOS_IPTV_Arbitrary_file_download.json
| | | | | | TamronOS_IPTV_ping_RCE.go
| | | | | | TamronOS_IPTV_RCE.json
| | | | | | TamronOS_IPTV_system_Filedownload_CNVD_2021_45711.json
| | | | | | TamronOS_IPTV_system_RCE.json
| | | | | | Tianwen_ERP_system_FileUpload_CNVD_2020_28119.json
| | | | | | Tianwen_ERP_system__uploadfile.aspx_Arbitraryvfilevupload.json
| | | | | | tongdaoa_unauth.json
| | | | | | Tongda_OA_api.ali.php_RCE.go
| | | | | | TopSec_Reporter_Arbitrary_file_download_CNVD_2021_41972.go
| | | | | | Tuchuang_Library_System_Arbitrary_Reading_File_CNVD_2021_34454.go
| | | | | | U8_OA.json
| | | | | | Unauthenticated_Multiple_D-Link_Routers_RCE_CVE-2019-16920.json
| | | | | | UniFi_Network_Log4shell_CVE-2021-44228.json
| | | | | | UniFi_Network_Log4shell_CVE_2021_44228.json
| | | | | | VENGD_Arbitrary_File_Upload.json
| | | | | | VMWare_Horizon_Log4shell_CVE-2021-44228.json
| | | | | | VMWare_Horizon_Log4shell_CVE_2021_44228.json
| | | | | | VMware_NSX_Log4shell_CVE-2021-44228.json
| | | | | | VMware_NSX_Log4shell_CVE_2021_44228.json
| | | | | | VMWare_Operations_vRealize_Operations_Manager_API_SSRF_CVE_2021_21975.json
| | | | | | VMware_vCenter_Log4shell_CVE-2021-44228_(1).json
| | | | | | VMware_vCenter_Log4shell_CVE_2021_44228_1.json
| | | | | | VMware_vCenter_v7.0.2_Arbitrary_File_Read.json
| | | | | | VMware_Workspace_ONE_Access_and_Identity_Manager_Server_Side_Template_Injection_CVE_2022_22954.json
| | | | | | VMware_Workspace_ONE_Access_RCE_CVE_2022_22954.json
| | | | | | WangKang_Next_generation_firewall_router_RCE.go
| | | | | | WangKang_NS_ASG_cert_download.php_File_read.go
| | | | | | wangyixingyun_waf_Information_leakage.json
| | | | | | WAVLINK_WN535G3_POST_XSS_CVE_2022_30489.json
| | | | | | Wayos AC集中管理系统默认弱口令 CNVD-2021-00876.json
| | | | | | Wayos_AC_Centralized_management_system_Default_Password_CNVD_2021_00876.json
| | | | | | Wayos_AC_Centralized_management_system_Default_weak_password.json
| | | | | | Weaver_EOffice_Arbitrary_File_Upload_CNVD-2021-49104.json
| | | | | | Weaver_EOffice_Arbitrary_File_Upload_CNVD_2021_49104.json
| | | | | | Weaver_e_cology_OA_XStream_RCE_CVE_2021_21350.go
| | | | | | Weaver_e_office_UploadFile.php_file_upload_CNVD_2021_49104.json
| | | | | | Weaver_OA_8_SQL_injection.json
| | | | | | weaver_OA_E_Cology_getSqlData_SQL_injection_vulnerability.json
| | | | | | Weaver_OA_E_Cology_Workflowservicexml_RCE.go
| | | | | | Webgrind_File_read_cve_2018_12909.go
| | | | | | Weblogic LDAP Internet RCE CVE-2021-2109.json
| | | | | | Weblogic LDAP 远程代码执行漏洞 CVE-2021-2109.json
| | | | | | Weblogic SSRF漏洞 CVE-2014-4210.json
| | | | | | Weblogic_LDAP_RCE_CVE_2021_2109.json
| | | | | | Weblogic_SSRF.json
| | | | | | WebSVN_before_2.6.1_Injection_RCE_CVE_2021_32305.json
| | | | | | WordPress_Simple_Ajax_Chat_plugin_InfoLeak_CVE_2022_27849.json
| | | | | | WordPress_WPQA_plugin_Unauthenticated_Private_Message_Disclosure_CVE_2022_1598.json
| | | | | | WSO2_fileupload_CVE_2022_29464.json
| | | | | | WSO2_Management_Console_Reflected_XSS_CVE_2022_29548.json
| | | | | | WSO2_Management_Console_Unrestricted_Arbitrary_File_Upload_RCE_CVE_2022_29464.json
| | | | | | xiaomi_Mi_wiFi_From_File_Read_To_Login_CVE_2019_18370.go
| | | | | | Xieda_oa.json
| | | | | | Xieda_OA_Filedownload_CNVD_2021_29066.json
| | | | | | XXL-JOB 任务调度中心 后台默认弱口令.json
| | | | | | XXL_JOB_Default_Login.json
| | | | | | XXL_JOB_Default_password.json
| | | | | | YAPI_RCE.json
| | | | | | YCCMS_XSS.json
| | | | | | Yinpeng_Hanming_Video_Conferencing_Filedownload_CNVD_2020_62437.json
| | | | | | Yinpeng_Hanming_Video_Conferencing__Arbitrary_file_read.json
| | | | | | yiyou__moni_detail.do_Remote_command_execution.json
| | | | | | yongyou_NC_bsh.servlet.BshServlet_RCE.json
| | | | | | Yonyou_UFIDA_NC_bsh.servlet.BshServlet_rce.json
| | | | | | yuanchuangxianfeng_unauthorized_access_vulnerability.json
| | | | | | yunshidai_ERP_SQL_injection.json
| | | | | | yycms_XSS.json
| | | | | | zabbix_saml_cve_2022_23131.json
| | | | | | Zhejiang_Dahua_DSS_System_Filedownload_CNVD_2020_61986.json
| | | | | | zhihuipingtai_FileDownLoad.aspx_Arbitrary_file_read_vulnerability.json
| | | | | | ZhongkeWangwei_Next_generation_firewall_File_read.go
| | | | | | ZhongQing_naibo_Education_Cloud_Platform_Information_leakage.go
| | | | | | ZhongQing_naibo_Education_Cloud_platform_reset_password.go
| | | | | | Zhongxing_F460_web_shell_cmd.gch_RCE.go
| | | | | | ZhongXinJingDun_Default_administrator_password.json
| | | | | | ZhongXinJingDun_Information_Security_Management_System_Default_Login.json
| | | | | | ZhongYuan_iAudit_get_luser_by_sshport.php_RCE.go
| | | | | | ziguang_editPass.html_SQL_injection_CNVD_2021_41638.json
| | | | | | ZZZCMS_parserSearch_RCE.go
| | | | | | ZZZCMS_parserSearch_RCE.go.json
| | | | | | 帆软报表 v8.0 任意文件读取漏洞 CNVD-2018-04757.json
| | | | | | 来福云SQL注入漏洞.json
| | | | | | 致远OA A6 数据库敏感信息泄露.json
| | | | | | 致远OA A6 用户敏感信息泄露.json
| | | | | | 致远OA webmail.do任意文件下载 CNVD-2020-62422.json
| | | | | | 蜂网互联 企业级路由器v4.31 密码泄露漏洞 CVE-2019-16313.json
| | | | | | 锐捷NBR路由器 EWEB网管系统 远程命令执行漏洞.json
| | | | | |
| | | | | +---images
| | | | | | goby.jpg
| | | | | |
| | | | | \---nuclei_pocs
| | | | | admin-file-search.yaml
| | | | | aem-detection.yaml
| | | | | AEM_misconfig.yaml
| | | | | alibaba-canal-info-leak.yaml
| | | | | apache-druid-detect.yaml
| | | | | apache-druid-unauth.yaml
| | | | | apache-filename-brute-force.yaml
| | | | | apache-loadbalancer.yaml
| | | | | apache-nifi-unauth.yaml
| | | | | apache-serverstatus.yaml
| | | | | apache-status-page.yaml
| | | | | api-keys.yaml
| | | | | api_endpoints.yaml
| | | | | apple_app_site.yaml
| | | | | application-ini.yaml
| | | | | artifactory_deploy.yaml
| | | | | auth-js.yaml
| | | | | avtech-dvr-exposure.yaml
| | | | | aws-ec2-sto.yaml
| | | | | aws-metadata.yaml
| | | | | aws-s3-open-bucket.yaml
| | | | | axis2-detect.yaml
| | | | | base64_strings.yaml
| | | | | basic-auth-detection.yaml
| | | | | beward-ipcamera-disclosure.yaml
| | | | | blind-xxe.yaml
| | | | | cacti-detect.yaml
| | | | | chamilo-lms-xss.yaml
| | | | | circarlife-default-login.yaml
| | | | | circleci-config.yaml
| | | | | circleci-ssh-config.yaml
| | | | | clickhouse-db-detect.yaml
| | | | | clickhouse-db-unauth.yaml
| | | | | coldfusion-lucee-auth-bypass.yaml
| | | | | common-error-00.yaml
| | | | | common-error-01.yaml
| | | | | common-forbidden-bypass.yaml
| | | | | comtrend-ct5367-remote-root.yaml
| | | | | config-file.yaml
| | | | | config-ini.yaml
| | | | | config-js.yaml
| | | | | connect-proxy.yaml
| | | | | content_injection.yaml
| | | | | control4-default-login.yaml
| | | | | cors-00.yaml
| | | | | cors-01.yaml
| | | | | couchbase-buckets-rest-api.yaml
| | | | | crlf.yaml
| | | | | CVE-2005-2428.yaml
| | | | | CVE-2007-0885.yaml
| | | | | CVE-2009-0545.yaml
| | | | | CVE-2009-4223.yaml
| | | | | CVE-2010-1871.yaml
| | | | | CVE-2011-4618.yaml
| | | | | CVE-2011-4624.yaml
| | | | | CVE-2011-4926.yaml
| | | | | CVE-2011-5107.yaml
| | | | | CVE-2011-5179.yaml
| | | | | CVE-2011-5181.yaml
| | | | | CVE-2011-5265.yaml
| | | | | CVE-2012-0901.yaml
| | | | | CVE-2012-2371.yaml
| | | | | CVE-2012-4242.yaml
| | | | | CVE-2012-5913.yaml
| | | | | CVE-2013-2287.yaml
| | | | | CVE-2013-3526.yaml
| | | | | CVE-2014-2321.yaml
| | | | | CVE-2014-2323.yaml
| | | | | CVE-2014-9094.yaml
| | | | | CVE-2015-6477.yaml
| | | | | CVE-2016-0957.yaml
| | | | | CVE-2017-0929.yaml
| | | | | CVE-2017-10075.yaml
| | | | | CVE-2017-11444.yaml
| | | | | CVE-2017-12615.yaml
| | | | | CVE-2017-14849.yaml
| | | | | CVE-2017-15715.yaml
| | | | | CVE-2017-16806.yaml
| | | | | CVE-2017-17562.yaml
| | | | | CVE-2017-5487.yaml
| | | | | CVE-2017-5638.yaml
| | | | | CVE-2017-6360.yaml
| | | | | CVE-2017-6361.yaml
| | | | | CVE-2017-7391.yaml
| | | | | CVE-2017-7529.yaml
| | | | | CVE-2017-9506.yaml
| | | | | CVE-2017-9841.yaml
| | | | | CVE-2018-0296.yaml
| | | | | CVE-2018-1000129.yaml
| | | | | CVE-2018-1000600.yaml
| | | | | CVE-2018-11409.yaml
| | | | | CVE-2018-11759.yaml
| | | | | CVE-2018-11784.yaml
| | | | | CVE-2018-1247.yaml
| | | | | CVE-2018-12634.yaml
| | | | | CVE-2018-1271.yaml
| | | | | CVE-2018-13379.yaml
| | | | | CVE-2018-14728.yaml
| | | | | CVE-2018-15640.yaml
| | | | | CVE-2018-16341.yaml
| | | | | CVE-2018-16668.yaml
| | | | | CVE-2018-16670.yaml
| | | | | CVE-2018-16671.yaml
| | | | | CVE-2018-16763.yaml
| | | | | CVE-2018-18069.yaml
| | | | | CVE-2018-18264.yaml
| | | | | CVE-2018-18326.yaml
| | | | | CVE-2018-19386.yaml
| | | | | CVE-2018-19439.yaml
| | | | | CVE-2018-20062.yaml
| | | | | CVE-2018-20824.yaml
| | | | | CVE-2018-2791.yaml
| | | | | CVE-2018-2894.yaml
| | | | | CVE-2018-3167.yaml
| | | | | CVE-2018-3714.yaml
| | | | | CVE-2018-3760.yaml
| | | | | CVE-2018-5230.yaml
| | | | | CVE-2018-6389.yaml
| | | | | CVE-2018-7490.yaml
| | | | | CVE-2018-9126.yaml
| | | | | CVE-2019-0230.yaml
| | | | | CVE-2019-10475.yaml
| | | | | CVE-2019-11043.yaml
| | | | | CVE-2019-11248.yaml
| | | | | CVE-2019-11510.yaml
| | | | | CVE-2019-11580.yaml
| | | | | cve-2019-11581.yaml
| | | | | CVE-2019-11600.yaml
| | | | | CVE-2019-12314.yaml
| | | | | CVE-2019-12461.yaml
| | | | | CVE-2019-12593.yaml
| | | | | CVE-2019-14205.yaml
| | | | | CVE-2019-14322.yaml
| | | | | CVE-2019-14470.yaml
| | | | | CVE-2019-14696.yaml
| | | | | CVE-2019-14974.yaml
| | | | | CVE-2019-15043.yaml
| | | | | CVE-2019-15859.yaml
| | | | | CVE-2019-15889.yaml
| | | | | CVE-2019-16097.yaml
| | | | | CVE-2019-16278.yaml
| | | | | CVE-2019-1653.yaml
| | | | | CVE-2019-16662.yaml
| | | | | CVE-2019-16759.yaml
| | | | | CVE-2019-17382.yaml
| | | | | CVE-2019-17558.yaml
| | | | | CVE-2019-18394.yaml
| | | | | CVE-2019-19368.yaml
| | | | | CVE-2019-19719.yaml
| | | | | CVE-2019-19781.yaml
| | | | | CVE-2019-19908.yaml
| | | | | CVE-2019-19985.yaml
| | | | | CVE-2019-20141.yaml
| | | | | CVE-2019-2588.yaml
| | | | | CVE-2019-2725.yaml
| | | | | CVE-2019-3799.yaml
| | | | | CVE-2019-5418.yaml
| | | | | CVE-2019-6112.yaml
| | | | | CVE-2019-7192.yaml
| | | | | CVE-2019-7238.yaml
| | | | | CVE-2019-7609.yaml
| | | | | CVE-2019-8442.yaml
| | | | | CVE-2019-8446.yaml
| | | | | CVE-2019-8449.yaml
| | | | | CVE-2019-8451.yaml
| | | | | CVE-2019-8903.yaml
| | | | | CVE-2019-8982.yaml
| | | | | CVE-2019-9082.yaml
| | | | | cve-2019-9670.yaml
| | | | | CVE-2019-9978.yaml
| | | | | CVE-2020-0618.yaml
| | | | | CVE-2020-10148.yaml
| | | | | CVE-2020-10199.yaml
| | | | | CVE-2020-10204.yaml
| | | | | CVE-2020-10220.yaml
| | | | | CVE-2020-11034.yaml
| | | | | CVE-2020-11450.yaml
| | | | | CVE-2020-1147.yaml
| | | | | CVE-2020-11530.yaml
| | | | | CVE-2020-11710.yaml
| | | | | CVE-2020-11854.yaml
| | | | | CVE-2020-12145.yaml
| | | | | CVE-2020-12271.yaml
| | | | | CVE-2020-12720.yaml
| | | | | CVE-2020-13167.yaml
| | | | | CVE-2020-13379.yaml
| | | | | CVE-2020-13937.yaml
| | | | | CVE-2020-13942.yaml
| | | | | CVE-2020-14179.yaml
| | | | | CVE-2020-14181.yaml
| | | | | CVE-2020-14750.yaml
| | | | | CVE-2020-14882-1.yaml
| | | | | CVE-2020-14882-2.yaml
| | | | | CVE-2020-14882.yaml
| | | | | CVE-2020-15004.yaml
| | | | | CVE-2020-15129.yaml
| | | | | CVE-2020-15505.yaml
| | | | | CVE-2020-15920.yaml
| | | | | CVE-2020-16139.yaml
| | | | | CVE-2020-16270.yaml
| | | | | CVE-2020-16846.yaml
| | | | | CVE-2020-16952.yaml
| | | | | CVE-2020-17506.yaml
| | | | | CVE-2020-19625.yaml
| | | | | CVE-2020-2096.yaml
| | | | | CVE-2020-2140.yaml
| | | | | CVE-2020-2199.yaml
| | | | | CVE-2020-22840.yaml
| | | | | CVE-2020-23517.yaml
| | | | | CVE-2020-24223.yaml
| | | | | CVE-2020-24312.yaml
| | | | | CVE-2020-24550.yaml
| | | | | CVE-2020-24609.yaml
| | | | | CVE-2020-24765.yaml
| | | | | CVE-2020-24949.yaml
| | | | | CVE-2020-25213.yaml
| | | | | CVE-2020-2551.yaml
| | | | | CVE-2020-25540.yaml
| | | | | CVE-2020-26073.yaml
| | | | | CVE-2020-27982.yaml
| | | | | CVE-2020-28188.yaml
| | | | | CVE-2020-29164.yaml
| | | | | CVE-2020-29395.yaml
| | | | | CVE-2020-3187.yaml
| | | | | CVE-2020-3452.yaml
| | | | | CVE-2020-35846.yaml
| | | | | CVE-2020-36112.yaml
| | | | | CVE-2020-3952.yaml
| | | | | CVE-2020-4038.yaml
| | | | | CVE-2020-4463.yaml
| | | | | CVE-2020-5284.yaml
| | | | | CVE-2020-5377.yaml
| | | | | CVE-2020-5398.yaml
| | | | | CVE-2020-5405.yaml
| | | | | CVE-2020-5410.yaml
| | | | | CVE-2020-5412.yaml
| | | | | CVE-2020-5777.yaml
| | | | | CVE-2020-5902.yaml
| | | | | CVE-2020-6287.yaml
| | | | | CVE-2020-7048.yaml
| | | | | CVE-2020-7209.yaml
| | | | | CVE-2020-7246.yaml
| | | | | CVE-2020-7473.yaml
| | | | | CVE-2020-8091.yaml
| | | | | CVE-2020-8115.yaml
| | | | | CVE-2020-8163.yaml
| | | | | CVE-2020-8193.yaml
| | | | | CVE-2020-8209.yaml
| | | | | CVE-2020-8512.yaml
| | | | | CVE-2020-8772.yaml
| | | | | CVE-2020-8982.yaml
| | | | | CVE-2020-9047.yaml
| | | | | CVE-2020-9054.yaml
| | | | | CVE-2020-9315.yaml
| | | | | CVE-2020-9344.yaml
| | | | | CVE-2020-9402.yaml
| | | | | CVE-2020-9484.yaml
| | | | | CVE-2020-9757.yaml
| | | | | CVE-2021-20837.yaml
| | | | | CVE-2021-21402.yaml
| | | | | CVE-2021-21972.yaml
| | | | | CVE-2021-21975.yaml
| | | | | CVE-2021-21978.yaml
| | | | | CVE-2021-22122.yaml
| | | | | CVE-2021-22873.yaml
| | | | | CVE-2021-24286.yaml
| | | | | CVE-2021-24291.yaml
| | | | | CVE-2021-25646.yaml
| | | | | CVE-2021-26475.yaml
| | | | | CVE-2021-27132.yaml
| | | | | CVE-2021-28937.yaml
| | | | | CVE-2021-29622.yaml
| | | | | CVE-2021-30461.yaml
| | | | | CVE-2021-31249.yaml
| | | | | CVE-2021-31250.yaml
| | | | | CVE-2021-31537.yaml
| | | | | CVE-2021-31581.yaml
| | | | | CVE-2021-31800.yaml
| | | | | CVE-2021-32820.yaml
| | | | | CVE-2021-33221.yaml
| | | | | CVE-2021-3374.yaml
| | | | | CVE-2021-3377.yaml
| | | | | CVE-2021-3378.yaml
| | | | | CVE-2021-33904.yaml
| | | | | darkstat-detect.yaml
| | | | | db-schema.yaml
| | | | | dbeaver-credentials.yaml
| | | | | dbeaver-data-sources.yaml
| | | | | default-config.yaml
| | | | | detect-dns-over-https.yaml
| | | | | detect-drone.yaml
| | | | | detect-rsyncd.yaml
| | | | | detect-tracer-sc-web.yaml
| | | | | detect-workerman-websocket-server.yaml
| | | | | developer_notes.yaml
| | | | | development-logs.yaml
| | | | | dir-listing.yaml
| | | | | dir-traversal.yaml
| | | | | display-via-header.yaml
| | | | | django-debug-enable.yaml
| | | | | django-debug-toolbar.yaml
| | | | | django-debug.yaml
| | | | | Django-DebugMode.yaml
| | | | | django-secret.key.yaml
| | | | | docker-k8s.yaml
| | | | | docker-registry.yaml
| | | | | dockercfg.yaml
| | | | | dom-xss.yaml
| | | | | elasticsearch-cluster-health.yaml
| | | | | email-extraction.yaml
| | | | | error-based-sql-injection.yaml
| | | | | error-logs.yaml
| | | | | errors-n-vulns.yaml
| | | | | esmtprc.yaml
| | | | | exposed-bitkeeper.yaml
| | | | | exposed-bzr.yaml
| | | | | exposed-darcs.yaml
| | | | | exposed-hg.yaml
| | | | | exposed-pii.yaml
| | | | | eyelock-nano-lfd.yaml
| | | | | favinizer.yaml
| | | | | ffserver-detect.yaml
| | | | | firebase-config.yaml
| | | | | firebase_urls.yaml
| | | | | fps-config.yaml
| | | | | ftpconfig.yaml
| | | | | fuzz-oauth.yaml
| | | | | ganglia-xml-grid-monitor.yaml
| | | | | git-credentials.yaml
| | | | | git-mailmap.yaml
| | | | | gitleak.yaml
| | | | | globalprotect-xss.yaml
| | | | | gloo-unauth.yaml
| | | | | glpi-fusioninventory-misconfig.yaml
| | | | | gmail-api-client-secrets.yaml
| | | | | go-pprof-exposed.yaml
| | | | | go-pprof.yaml
| | | | | gogs-install-exposure.yaml
| | | | | goliath-detect.yaml
| | | | | google-floc-disabled.yaml
| | | | | graphite-browser-default-credential.yaml
| | | | | graphite-browser-detect.yaml
| | | | | graphql-playround-xss.yaml
| | | | | graphql_get.yaml
| | | | | hadoop-unauth.yaml
| | | | | haproxy-stat.yaml
| | | | | hashicorp-consul-rce.yaml
| | | | | header-blind-sql-injection.yaml
| | | | | header-blind-ssrf.yaml
| | | | | header-command-injection.yaml
| | | | | header_blind_xss.yaml
| | | | | header_reflection.yaml
| | | | | header_reflection_body.yaml
| | | | | header_sqli.yaml
| | | | | header_user_id.yaml
| | | | | homeworks-illumination-web-keypad.yaml
| | | | | host-header-auth-bypass.yaml
| | | | | host-header-injection.yaml
| | | | | htpasswd-detection.yaml
| | | | | huawei-dg8045-auth-bypass.yaml
| | | | | iis-directory-listing.yaml
| | | | | java-melody-stat.yaml
| | | | | jetbrains-webservers-xml.yaml
| | | | | jetty-information-disclosure.yaml
| | | | | jira-service-desk-signup.yaml
| | | | | joomla-host-injection.yaml
| | | | | joomla-lfi-comfabrik.yaml
| | | | | joomla-sqli-hdwplayer.yaml
| | | | | jupyter-ipython-unauth.yaml
| | | | | kafdrop-xss.yaml
| | | | | kafka-misconfig.yaml
| | | | | kentico-open-redirect.yaml
| | | | | keys-js.yaml
| | | | | kong-detect.yaml
| | | | | kube-dashboard-detect.yaml
| | | | | kubeflow-dashboard-unauth.yaml
| | | | | kubernetes-api-detect.yaml
| | | | | landfill-remote-monitoring-control.yaml
| | | | | laravel-telescope-exposed.yaml
| | | | | laravel-telescope.yaml
| | | | | lfi-00.yaml
| | | | | lfi-01.yaml
| | | | | lfi-02.yaml
| | | | | lfi-03.yaml
| | | | | lfi-04.yaml
| | | | | lfi-05.yaml
| | | | | lfi-06.yaml
| | | | | logins.yaml
| | | | | lucee-detect.yaml
| | | | | lutron-iot-default-login.yaml
| | | | | magento-config.yaml
| | | | | missing-csp.yaml
| | | | | monitorix-exposure.yaml
| | | | | moodle-auth-xss.yaml
| | | | | mrtg-detect.yaml
| | | | | munin-monitoring.yaml
| | | | | netdata-unauth.yaml
| | | | | netgear-router-disclosure.yaml
| | | | | netrc.yaml
| | | | | nginx-conf-exposed.yaml
| | | | | nginx-vhost-traffic-status.yaml
| | | | | nginx-vhost-xss.yaml
| | | | | nginx-vhosts-stat.yaml
| | | | | node-nunjucks-ssti.yaml
| | | | | npmrc.yaml
| | | | | old-copyright.yaml
| | | | | open-redirect-00.yaml
| | | | | open-redirect-01.yaml
| | | | | open-redirect-02.yaml
| | | | | open-redirect-03.yaml
| | | | | open-redirect-04.yaml
| | | | | open-redirect.yaml
| | | | | opengear-detect.yaml
| | | | | openstack-user-secrets.yaml
| | | | | oracle-ebs-config-disclosure.yaml
| | | | | oracle-ebs-credentials-disclosure.yaml
| | | | | oracle-ebs-desr.yaml
| | | | | oracle-ebs-lfi.yaml
| | | | | oracle-ebs-sqllog-disclosure.yaml
| | | | | oracle-ebs-xss.yaml
| | | | | oracle-stat.yaml
| | | | | pagespeed-global-admin.yaml
| | | | | perl-status-page.yaml
| | | | | php-debug-bar.yaml
| | | | | php-fpm-status.yaml
| | | | | php-ini.yaml
| | | | | php-symfony-debug.yaml
| | | | | php-timeclock-xss.yaml
| | | | | php-user-ini.yaml
| | | | | pi-hole-detect.yaml
| | | | | pinpoint-unauth.yaml
| | | | | pmb-directory-traversal.yaml
| | | | | production-logs.yaml
| | | | | prtg-detect.yaml
| | | | | public-documents.yaml
| | | | | putty-user-keyfile.yaml
| | | | | pyramid-debug-toolbar.yaml
| | | | | rails-secret-token.yaml
| | | | | random-fuzz-00.yaml
| | | | | random-fuzz-01.yaml
| | | | | random-fuzz-02.yaml
| | | | | random-fuzz-03.yaml
| | | | | redis-conf.yaml
| | | | | redmine-cli-detect.yaml
| | | | | redmine-db-config.yaml
| | | | | remote-sync.yaml
| | | | | rescro.yaml
| | | | | robomongo.yaml
| | | | | rocketmq-console.yaml
| | | | | route-bypass.yaml
| | | | | routes-ini.yaml
| | | | | rpcbind-portmapper.yaml
| | | | | s3cfg.yaml
| | | | | salesforce-login.yaml
| | | | | sap-directory-listing.yaml
| | | | | schneider-lights.yaml
| | | | | searches.yaml
| | | | | secret.yaml
| | | | | selea-ip-camera.yaml
| | | | | server-private-keys.yaml
| | | | | service-now-exposed.yaml
| | | | | setPreferences-xss.yaml
| | | | | sftp-config.yaml
| | | | | sftp-deployment-config.yaml
| | | | | shells.yaml
| | | | | shell_scripts.yaml
| | | | | simple-xss.yaml
| | | | | soap-defination-probing.yaml
| | | | | solar-log-500.yaml
| | | | | sonarqube-cred.yaml
| | | | | sony-bravia-disclosure.yaml
| | | | | spark-unauth.yaml
| | | | | spidercontrol-scada-server-info.yaml
| | | | | sqli-00.yaml
| | | | | sqli-01.yaml
| | | | | squid-analysis-report-generator.yaml
| | | | | squid-detect.yaml
| | | | | SquirrelMail.yaml
| | | | | ssh-authorized-keys.yaml
| | | | | ssh-known-hosts.yaml
| | | | | ssrf-by-proxy.yaml
| | | | | stats.yaml
| | | | | svn-leak.yaml
| | | | | swagger-xss.yaml
| | | | | symfony-detect.yaml
| | | | | tectuus-scada-monitor.yaml
| | | | | telerik-derserial.yaml
| | | | | template-injection.yaml
| | | | | terraform-detect.yaml
| | | | | tor-socks-proxy.yaml
| | | | | tox-ini.yaml
| | | | | unauthen-elastic.yaml
| | | | | unauthen-kibana.yaml
| | | | | upnp-device.yaml
| | | | | ventrilo-config.yaml
| | | | | vernemq-status.yaml
| | | | | viewlinc-crlf-injection.yaml
| | | | | vscode-sftp.yaml
| | | | | web-config.yaml
| | | | | werkzeug-debug.yaml
| | | | | wordpress-accessible-wpconfig.yaml
| | | | | wordpress-directory-listing.yaml
| | | | | wordpress-misconfig.yaml
| | | | | wordpress-rest-api.yaml
| | | | | wordpress-user-enum.yaml
| | | | | wp-ambience-xss.yaml
| | | | | wp-church-admin-xss.yaml
| | | | | wp-finder-xss.yaml
| | | | | wp-knews-xss.yaml
| | | | | wp-phpfreechat-xss.yaml
| | | | | wp-securimage-xss.yaml
| | | | | wp-socialfit-xss.yaml
| | | | | ws-config.yaml
| | | | | x-hacker.yaml
| | | | | xmlrpc-pingback-ssrf.yaml
| | | | | xss-fuzz.yaml
| | | | | yii-debugger.yaml
| | | | | zabbix-creds.yaml
| | | | | zeroshell-kerbynet-lfd.yaml
| | | | | zipkin-unauth.yaml
| | | | | zwave2mqtt-health-check.yaml
| | | | |
| | |
| | +---goby_pocs
| | | 360_TianQing_ccid_SQL_injectable.json
| | | 360_Tianqing_database_information_disclosure.json
| | | AceNet_AceReporter_Report_component_Arbitrary_file_download.go
| | | Active_UC_index.action_RCE.json
| | | ACTI_camera_images_File_read.go
| | | Adobe_ColdFusion_LFI_CVE-2010-2861.json
| | | ADSelfService_Plus_RCE_CVE-2021-40539.json
| | | ADSelfService_Plus_RCE_CVE_2021_40539.json
| | | Adslr_Enterprise_online_behavior_management_system_Information_leak.json
| | | Adslr_Enterprise_online_behavior_management_system_Information_leakage.json
| | | Alibaba Nacos 控制台默认弱口令.json
| | | Alibaba Nacos 未授权访问漏洞.json
| | | alibaba_canal_default_password.json
| | | Alibaba_Nacos_Add_user_not_authorized.json
| | | Alibaba_Nacos_Default_password.json
| | | Ametys_CMS_infoleak_CVE_2022_26159.json
| | | Apache ActiveMQ Console控制台弱口令.json
| | | Apache Cocoon Xml 注入 CVE-2020-11991.json
| | | Apache Kylin Console 控制台弱口令.json
| | | Apache Kylin 未授权配置泄露 CVE-2020-13937.json
| | | Apache Solr Log4j JNDI RCE.go
| | | Apache Solr任意文件读取漏洞.json
| | | Apache_2.4.49_Path_Traversal_CVE_2021_41773.json
| | | Apache_2.4.49_RCE_CVE_2021_41773_and_2.4.50_CVE_2021_42013.json
| | | Apache_ActiveMQ_Console_Weak_Password.json
| | | Apache_ActiveMQ_default_admin_account.json
| | | Apache_Airflow_Unauthorized.json
| | | Apache_APISIX_Admin_API_Default_Token_CVE_2020_13945.json
| | | Apache_APISIX_Dashboard_API_Unauthorized_Access_CVE-2021-45232.json
| | | Apache_APISIX_Dashboard_CVE_2021_45232.json
| | | Apache_APISIX_Dashboard_RCE_CVE_2021_45232.json
| | | Apache_Cocoon_XML_Injection_CVE_2020_11991.json
| | | Apache_CouchDB_Remote_Privilege_Escalation_CVE-2017-12635.json
| | | Apache_CouchDB_Unauth.json
| | | Apache_Druid_Abritrary_File_Read_CVE-2021-36749.json
| | | Apache_Druid_Abritrary_File_Read_CVE_2021_36749.json
| | | Apache_Druid_Arbitrary_File_Read_CVE_2021_36749.json
| | | Apache_Druid_Log4shell_CVE-2021-44228.json
| | | Apache_Druid_Log4shell_CVE_2021_44228.json
| | | Apache_Dubbo_Admin_Default_Password.json
| | | Apache_Flink_CVE_2020_17519.json
| | | Apache_HTTP_Server_2.4.48_mod_proxy_SSRF_CVE_2021_40438.json
| | | Apache_HTTP_Server_2.4.49_2.4.50_Path_Traversal_CVE_2021_42013.json
| | | Apache_HTTP_Server_2.4.49_Path_Traversal_CVE_2021_41773.json
| | | Apache_HTTP_Server_2.4.49_RCE_CVE_2021_41773.json
| | | Apache_HTTP_Server_Arbitrary_File_Read_CVE_2021_41773.json
| | | Apache_HTTP_Server_SSRF_CVE-2021-40438.json
| | | Apache_HTTP_Server_SSRF_CVE_2021_40438.json
| | | Apache_JSPWiki_Log4shell_CVE-2021-44228_(1).json
| | | Apache_JSPWiki_Log4shell_CVE-2021-44228_(2).json
| | | Apache_JSPWiki_Log4shell_CVE_2021_44228_1.json
| | | Apache_JSPWiki_Log4shell_CVE_2021_44228_2.json
| | | Apache_Kylin_Console_Default_password.json
| | | Apache_Kylin_Unauthorized_configuration_disclosure.json
| | | Apache_OFBiz_Log4shell_CVE-2021-44228.json
| | | Apache_OFBiz_Log4shell_CVE_2021_44228.json
| | | Apache_ShenYu_Admin_Unauth_Access_CVE_2022_23944.json
| | | Apache_SkyWalking_Log4shell_CVE-2021-44228.json
| | | Apache_SkyWalking_Log4shell_CVE_2021_44228.json
| | | Apache_Solr_Arbitrary_File_Read.json
| | | Apache_Solr_Log4j2CVE_2021_44228.json
| | | Apache_Solr_RemoteStreaming_File_Read.json
| | | Apache_Struts2_S2_053_RCE_CVE_2017_12611.json
| | | Apache_Struts2_S2_059_RCE_CVE_2019_0230.json
| | | Apache_Struts2_S2_062_RCE_CVE_2021_31805.json
| | | Aspcms_Backend_Leak.json
| | | AspCMS_commentList.asp_SQLinjection_vulnerability.json
| | | Atlassian Jira 信息泄露漏洞 CVE-2020-14181.json
| | | Atlassian_Confluence_OGNL_injection_CVE_2021_26084.json
| | | Atlassian_Confluence_OGNL_Injection_RCE_CVE_2022_26134.json
| | | Atlassian_Confluence_Webwork_OGNL_Inject_CVE_2022_26134.go
| | | Atlassian_Jira_Path_Traversal_CVE_2021_26086.json
| | | Atlassian_Jira_Seraph_Authentication_bypass_CVE_2022_0540.json
| | | Atlassian_Jira_user_information_disclosure.json
| | | Atlassian_Jira_user_information_disclosure_CVE_2020_14181.json
| | | AVCON6_org_execl_download.action_file_down.json
| | | BigAnt_Server_v5.6.06_Path_Traversal_CVE_2022_23347.json
| | | BSPHP_index.php_unauthorized_access_information.json
| | | Cacti_Weathermap_File_Write.json
| | | Casdoor_1.13.0_SQL_InjectionCVE_2022_24124.json
| | | Cerebro_request_SSRF.json
| | | chanjet_CRM_get_usedspace.php_sql_injection.json
| | | Chanjet_CRM_get_usedspace.php_sql_injection_CNVD_2021_12845.json
| | | China_Mobile_Yu_routed_the_login_bypass.json
| | | China_Mobile_Yu_Routing_ExportSettings.sh_Info_Leak_CNVD_2020_67110.json
| | | China_Mobile_Yu_Routing_Login_Bypass.json
| | | China_Mobile_Yu_Routing_Sensitive_Information_Leaks_Vulnerability.json
| | | Citrix_unauthenticated_LFI_CVE-2020-8193.json
| | | Citrix_Unauthorized_CVE_2020_8193.json
| | | ClickHouse_SQLI.json
| | | ClusterEngineV4.0_RCE_.json
| | | ClusterEngine_V4.0_Shell_cluster_RCE.json
| | | CmsEasy_crossall_act.php_SQL_injection_vulnerability.json
| | | Coldfusion_LFI_CVE_2010_2861.json
| | | Confluence_RCE_CVE_2021_26084.json
| | | Consul_Rexec_RCE.json
| | | Coremail_configuration_information_disclosure.json
| | | Coremail_Config_Disclosure.json
| | | CouchCMS_Infoleak_CVE-2018-7662.json
| | | Couchdb_Add_User_Not_Authorized_CVE_2017_12635.json
| | | Couchdb_Unauth.json
| | | Couch_CMS_Infoleak_CVE_2018_7662.json
| | | CraftCMS_Seomatic_RCE_CVE_2020_9597.json
| | | CraftCMS_SEOmatic_Server-Side_Template_Injection_CVE-2020-9597.json
| | | CVE_2018_19367_.json
| | | cve_2022_1388_goby.json
| | | CVE_2022_22947.json
| | | D-Link AC集中管理系统默认弱口令.json
| | | D-Link DCS系列监控 CNVD-2020-25078.json
| | | D-Link DCS系列监控 账号密码信息泄露漏洞 CNVD-2020-25078.json
| | | D-Link_AC_management_system_Default_Password.json
| | | D-Link_DCS_2530L_Administrator_password_disclosure_CVE_2020_25078.json
| | | D-Link_DIR-850L_Info_Leak.json
| | | D-Link_DIR_868L_x_DIR_817LW_Info_Leak_CVE_2019_17506.json
| | | D-Link_Info_Leak_CVE-2019-17506.json
| | | D-Link_ShareCenter_DNS_320_RCE.json
| | | dahua_DSS_Arbitrary_file_download.json
| | | dahua_DSS_Arbitrary_file_download_cnvd_2020_61986.go
| | | Datang_AC_Default_Password.json
| | | DedeCMS_Carbuyaction_FileInclude.json
| | | DedeCMS_InfoLeak_CVE-2018-6910.json
| | | DedeCMS_InfoLeak_CVE_2018_6910.json
| | | Discuz!ML_3.x_RCE_CNVD-2019-22239.json
| | | Discuz_ML_3.x_RCE__CNVD_2019_22239.json
| | | Discuz_RCE_WOOYUN_2010_080723.json
| | | Discuz_v72_SQLI.json
| | | Discuz_Wechat_Plugins_Unauth.json
| | | Dlink_850L_Info_Leak.json
| | | Dlink_Info_Leak_CVE_2019_17506.json
| | | Dlink_RCE_CVE_2019_16920.json
| | | DocCMS_keyword_SQL_injection_Vulnerability.json
| | | Docker_Registry_API_Unauth.json
| | | DotCMS_Arbitrary_File_Upload_CVE_2022_26352.json
| | | Dubbo_Admin_Default_Password.json
| | | D_Link_AC_Centralized_management_system__Default_weak_password.json
| | | D_Link_DC_Disclosure_of_account_password_information.json
| | | D_Link_Dir_645_getcfg.php_Account_password_disclosure_CVE_2019_17506.go
| | | D_Link_DIR_868L_getcfg.php_Account_password_leakage.json
| | | D_Link_ShareCenter_DNS_320_RCE.json
| | | D_Link_ShareCenter_DNS_320_system_mgr.cgi_RCE.go
| | | Elasticsearch_Remote_Code_Execution_CVE_2014_3120.go
| | | Elasticsearch_Remote_Code_Execution_CVE_2015_1427.go
| | | ESAFENET_DLP_dataimport_RCE.go
| | | Eyou_Mail_system_RCE.json
| | | Eyou_Mail_System_RCE_CNVD_2021_26422.json
| | | F5_BIG_IP_iControl_REST_API_auth_bypass_CVE_2022_1388.json
| | | F5_BIG_IP_iControl_REST_Unauthenticated_RCE_CVE_2021_22986.json
| | | F5_BIG_IP_login_bypass_CVE_2022_1388.go
| | | F5_BIG_IP_RCE_CVE_2021_22986_exp.json
| | | fahuo100_sql_injection_CNVD_2021_30193.json
| | | Fastmeeting_Arbitrary_File_Read.json
| | | feishimei_struts2_remote_code.json
| | | FineReport_Directory_traversal.json
| | | FineReport_v8.0_Arbitrary_file_read_.json
| | | FineReport_v8.0_Fileread_CNVD_2018_04757.json
| | | FineReport_v8.0_v9.0_Directory_Traversal.json
| | | FineReport_v9_Arbitrary_File_Overwrite.json
| | | Finetree_5MP_default_password_or_Unauthorized_user_added.json
| | | Finetree_5MP_Network_Camera_Default_Login_unauthorized_user_add.json
| | | firewall_Leaked_user_name_and_password.json
| | | FLIR_AX8_Arbitrary_File_Download_Vulnerability_CNVD-2021-39018.go
| | | ForgeRock_AM_RCE_CVE_2021_35464.go
| | | fumengyun AjaxMethod.ashx SQL injection.json
| | | GitLab Graphql邮箱信息泄露漏洞 CVE-2020-26413.json
| | | GitLab_Graphql_Email_information_disclosure.json
| | | GitLab_Graphql_Email_information_disclosure_CVE_2020_26413.json
| | | GitLab_RCE_CVE-2021-22205.json
| | | Gitlab_RCE_CVE_2021_22205.json
| | | GitLab_SSRF_CVE_2021_22214.json
| | | GoCD_Arbitrary_file_reading_CVE_2021_43287.json
| | | GoCD_Unauthorized_Path_Traversal_CVE_2021_43287.json
| | | Grafana_Angularjs_Rendering_XSS_CVE_2021_41174.json
| | | Grafana_Arbitrary_file_read.json
| | | Grafana_Plugins_Arbitrary_File_Read.json
| | | Grafana_v8.x_Arbitrary_File_Read_CVE_2021_43798.json
| | | H3C_HG659_lib_File_read.go
| | | H3C_IMC_dynamiccontent.properties.xhtm_RCE.go
| | | H3C_IMC_RCE.json
| | | H3C_Next_generation_firewall_File_read.go
| | | H3C_SecPath_Operation_Login_bypass.go
| | | H5S_CONSOLE_Video_Platform_GetSrc_Information_Leak_CNVD_2021_25919.json
| | | H5S_video_platform_GetSrc_information_leakage.json
| | | H5S_video_platform_GetUserInfo_Account_password_leakage.json
| | | H5S_Video_Platform_GetUserInfo_Info_Leak_CNVD_2021_35567.json
| | | HanWang_Time_Attendance_SQL_injection.go
| | | HEJIA_PEMS_SystemLog.cgi_Arbitrary_file_download.go
| | | HIKVISION 视频编码设备接入网关 任意文件下载.json
| | | HIKVISION.json
| | | Hikvision_RCE_CVE_2021_36260.json
| | | Hikvision_Unauthenticated_RCE_CVE-2021-36260.json
| | | HIKVISION_Video_coding_equipment_Download_any_file.json
| | | Hikvision_Video_Encoding_Device_Access_Gateway_Any_File_Download.json
| | | Holographic_AI_network_operation_and_maintenance_platform_RCE.go
| | | HotelDruid_Hotel_Management_Software_v3.0.3_XSS_CVE_2022_26564.json
| | | Hsmedia_Hgateway_Default_account.json
| | | huatiandongliOA_8000workFlowService_SQLinjection.json
| | | Huijietong_cloud_video_fileDownload_File_read.go
| | | Huijietong_cloud_video_list_Information_leakage.go
| | | IceWarp_WebClient_basic_RCE.json
| | | IFW8_Enterprise_router_Password_leakage_.json
| | | IFW8_Router_ROM_v4.31_Credential_Discovery_CVE_2019_16313.json
| | | IRDM4000_Smart_station_Unauthorized_access.json
| | | JEEWMS_Arbitrary_File_Read_Vulnerability.go
| | | Jellyfin_10.7.0_Unauthenticated_Abritrary_File_Read_CVE_2021_21402.json
| | | Jellyfin_10.7.2_SSRF_CVE-2021-29490.json
| | | Jellyfin_Audio_File_read_CVE_2021_21402.go
| | | Jellyfin_prior_to_10.7.0_Unauthenticated_Arbitrary_File_Read_CVE_2021_21402.json
| | | Jellyfin_SSRF_CVE_2021_29490.json
| | | Jetty_WEB_INF_FileRead_CVE_2021_28169.json
| | | Jetty_WEB_INF_FileRead_CVE_2021_34429.json
| | | JingHe_OA_C6_Default_password.json
| | | JingHe_OA_download.asp_File_read.go
| | | Jinher_OA_C6_download.jsp_Arbitrary_file_read.json
| | | JinHe_OA_C6_Default_password.json
| | | JinHe_OA_C6_download.jsp_Arbitrary_fileread.json
| | | Jinshan_V8.json
| | | Jitong_EWEBS_arbitrary_file_read.json
| | | Jitong_EWEBS_Fileread.json
| | | Jitong_EWEBS_phpinfo_leak.json
| | | JQuery_1.7.2Version_site_foreground_arbitrary_file_download.json
| | | JQuery_1.7.2_Filedownload.json
| | | KEDACOM_MTS_transcoding_server_Arbitrary_file_download_CNVD_2020_48650.json
| | | KEDACOM_MTS_transcoding_server_Fileread_CNVD_2020_48650.json
| | | Kingdee_EAS_server_file_Directory_traversal.go
| | | Kingsoft_V8_Arbitrary_file_read.json
| | | Kingsoft_V8_Default_weak_password.json
| | | Kingsoft_V8_Terminal_Security_System_Default_Login_CNVD_2021_32425.json
| | | Kingsoft_V8_Terminal_Security_System_Fileread.json
| | | Konga_Default_JWT_KEY.json
| | | Kyan.json
| | | Kyan_Account_password_leak.json
| | | Kyan_design_account_password_disclosure.json
| | | Kyan_network_monitoring_device_account_password_leak.json
| | | Kyan_network_monitoring_device_run.php_RCE.json
| | | Kyan_run.php_RCE.json
| | | landray_OA_Arbitrary_file_read.json
| | | Landray_OA_custom.jsp_Fileread.json
| | | landray_oa_treexml_rce.go
| | | LanhaiZuoyue_system_debug.php_RCE.go
| | | LanhaiZuoyue_system_download.php_File_read.go
| | | Lanproxy 目录遍历漏洞 CVE-2021-3019.json
| | | Lanproxy_Arbitrary_File_Read_CVE_2021_3019.json
| | | Lanproxy_Directory_traversal_CVE_2021_3019.json
| | | Laravel .env 配置文件泄露 CVE-2017-16894.json
| | | Laravel_.env_configuration_file_leaks_(CVE-2017-16894).json
| | | Laravel_.env_configuration_file_leaks_CVE_2017_16894.json
| | | Leadsec_ACM_infoleak_CNVD-2016-08574.json
| | | Leadsec_ACM_information_leakage_CNVD_2016_08574.json
| | | Longjing_Technology_BEMS_API_1.21_Remote_Arbitrary_File_Download.go
| | | mallgard.json
| | | Mallgard_Firewall_Default_Login_CNVD_2020_73282.json
| | | Many_network_devices_have_arbitrary_file_downloads.go
| | | Many_network_devices_have_password_leaks.go
| | | MessageSolution 邮件归档系统EEA 信息泄露漏洞 CNVD-2021-10543.json
| | | MessageSolution_EEA_information_disclosure.json
| | | MessageSolution_EEA_information_disclosure_CNVD_2021_10543.json
| | | Metabase_geojson_Arbitrary_file_reading_CVE_2021_41277.json
| | | Metabase_Geojson_Arbitrary_File_Read_CVE-2021-41277.json
| | | Metabase_Geojson_Arbitrary_File_Read_CVE_2021_41277.json
| | | Microsoft Exchange SSRF漏洞 CVE-2021-26885.json
| | | Microsoft_Exchange_Server_SSRF_CVE_2021_26885.json
| | | Micro_module_monitoring_system_User_list.php_information_leakage.json
| | | MinIO_Browser_API_SSRF_CVE_2021_21287.json
| | | MobileIron_Log4shell_CVE-2021-44228.json
| | | MobileIron_Log4shell_CVE_2021_44228.json
| | | MPSec_ISG1000_Gateway_Filedownload_CNVD_2021_43984.json
| | | MPSec_ISG1000_Security_Gateway_Arbitrary_File_Download_Vulnerability.json
| | | Node-RED_ui_base_Arbitrary_File_Read_CVE-2021-3223.json
| | | Node.js_Path_Traversal_CVE_2017_14849.json
| | | Node_RED_ui_base_Arbitrary_File_Read.json
| | | Node_red_UI_base_Arbitrary_File_Read_Vulnerability_CVE_2021_3223.go
| | | nsoft_EWEBS_casmain.xgi_File_read.go
| | | NVS3000_integrated_video_surveillance_platform_is_not_accessible.go
| | | OpenSNS_Application_ShareController.class.php__remote_command_execution_vulnerability.json
| | | OpenSNS_RCE.json
| | | Oracle_Weblogic_LDAP_RCE_CVE_2021_2109.json
| | | Oracle_Weblogic_SearchPublicRegistries.jsp_SSRF_CVE_2014_4210.json
| | | Oracle_WebLogic_Server_Path_Traversal_CVE_2022_21371.json
| | | Oray_Sunlogin_RCE_CNVD_2022_03672_CNVD_2022_10270.json
| | | Panabit_Application_Gateway_ajax_top_backstage_RCE.go
| | | Panabit_iXCache_ajax_cmd_backstage_RCE.go
| | | Panabit_Panalog_cmdhandle.php_backstage_RCE.go
| | | php8.1backdoor.json
| | | PHP_8.1.0-dev_Zerodium_Backdoor_RCE.json
| | | Portainer_Init_Deploy_CVE_2018_19367.json
| | | qilaiOA_messageurl.aspx_SQLinjection.json
| | | qilaiOA_treelist.aspx_SQLinjection.json
| | | Qilai_OA_CloseMsg.aspx_SQL_injection.go
| | | red_fan_OA_hospital_ioFileExport.aspx_file_read.json
| | | RG_UAC.json
| | | Riskscanner_list_SQL_injection.json
| | | Ruijie_Networks_EWEB_Network_Management_System_RCE_CNVD_2021_09650.json
| | | Ruijie_RG_UAC_Password_leakage_CNVD_2021_14536.json
| | | Ruijie_Smartweb_Default_Password_CNVD_2020_56167.json
| | | Ruijie_Smartweb_Management_System_Password_Information_Disclosure_CNVD_2021_17369.json
| | | Ruijie_smartweb_password_information_disclosure.json
| | | Ruijie_smartweb_weak_password.json
| | | RuoYi_Druid_Unauthorized_access.json
| | | Samsung_WLAN_AP_RCE.json
| | | Samsung_WLAN_AP_WEA453e_RCE.json
| | | Samsung_WLAN_AP_wea453e_router_RCE.json
| | | sangfor_Behavior_perception_system_c.php_RCE.json
| | | SDWAN_Smart_Gateway_Default_Password.json
| | | SDWAN_smart_gateway_weak_password.json
| | | Security_Devices_Hardcoded_Password.json
| | | SECWORLD_Next_generation_firewall_pki_file_download_File_read.go
| | | Seeyon_OA_A6_DownExcelBeanServlet_User_information_leakage.json
| | | Seeyon_OA_A6_initDataAssess.jsp_User_information_leakage.json
| | | Seeyon_OA_A6_setextno.jsp_SQL_injection.json
| | | Seeyon_OA_A6_test.jsp_SQL_injection.json
| | | Seeyon_OA_A6__Disclosure_of_database_sensitive_information.json
| | | Seeyon_OA_A8_m_Information_leakage.json
| | | Selea_OCR_ANPR_get_file.php_File_read.go
| | | Selea_OCR_ANPR_SeleaCamera_File_read.go
| | | Shenzhen_West_dieter_Technology_Co_LTD_CPE_WiFi__ping_RCE.go
| | | Shenzhen_West_dieter_Technology_Co_LTD_CPE_WiFi__tracert_RCE.go
| | | ShiziyuCms_ApiController.class.php_SQL_injection.go
| | | ShiziyuCms_ApiController.class.php_SQL_injection.go.json
| | | ShiziyuCms_ApigoodsController.class.php_SQL_injection.go
| | | ShiziyuCms_ApigoodsController.class.php_SQL_injection.go.json
| | | ShiziyuCms_wxapp.php_File_update.go
| | | ShopXO_download_Arbitrary_file_read_CNVD_2021_15822.json
| | | ShopXO_download_File_read_CNVD_2021_15822.go
| | | ShopXO_Fileread_CNVD_2021_15822.json
| | | showDocGo.go
| | | showDocJson.go
| | | shtermQiZhi_Fortress_Arbitrary_User_Login.json
| | | Shterm_QiZhi_Fortress_Unauthorized_Access_CNVD_2019_27717.json
| | | SonarQube_search_projects_information.json
| | | SonarQube_unauth_CVE-2020-27986.json
| | | SonarQube_unauth_CVE_2020_27986.json
| | | SonicWall SSL-VPN 远程命令执行漏洞.json
| | | Sonicwall_SSLVPN_ShellShock_RCE.json
| | | SonicWall_SSL_VPN_RCE.json
| | | SpiderFlow_save__remote_code.json
| | | SPON_IP_network_intercom_broadcast_system_exportrecord.php_any_file_download.go
| | | SPON_IP_network_intercom_broadcast_system_getjson.php_Arbitrary_file_read.go
| | | SPON_IP_network_intercom_broadcast_system_ping.php_RCE.go
| | | SPON_IP_network_intercom_broadcast_system_rj_get_token.php_any_file_read.go
| | | Spring_Boot_Actuator_Logview_Path_Traversal_CVE_2021_21234.json
| | | Spring_boot_actuator_unauthorized_access.json
| | | Spring_Cloud_Function_SpEL_RCE_CVE_2022_22963.json
| | | Spring_Cloud_Gateway_Actuator_API_SpEL_Code_Injection_CVE_2022_22947.json
| | | Spring_Framework_Data_Binding_Rules_Spring4Shell_RCE_CVE_2022_22965.json
| | | Struts2_Log4Shell_CVE-2021-44228_(1).json
| | | Struts2_Log4Shell_CVE-2021-44228_(2).json
| | | Struts2_Log4Shell_CVE-2021-44228_(3).json
| | | Struts2_Log4Shell_CVE_2021_44228_1.json
| | | Struts2_Log4Shell_CVE_2021_44228_2.json
| | | Struts2_Log4Shell_CVE_2021_44228_3.json
| | | TamronOS_IPTV_Arbitrary_file_download.json
| | | TamronOS_IPTV_ping_RCE.go
| | | TamronOS_IPTV_RCE.json
| | | TamronOS_IPTV_system_Filedownload_CNVD_2021_45711.json
| | | TamronOS_IPTV_system_RCE.json
| | | Tianwen_ERP_system_FileUpload_CNVD_2020_28119.json
| | | Tianwen_ERP_system__uploadfile.aspx_Arbitraryvfilevupload.json
| | | tongdaoa_unauth.json
| | | Tongda_OA_api.ali.php_RCE.go
| | | TopSec_Reporter_Arbitrary_file_download_CNVD_2021_41972.go
| | | Tuchuang_Library_System_Arbitrary_Reading_File_CNVD_2021_34454.go
| | | U8_OA.json
| | | Unauthenticated_Multiple_D-Link_Routers_RCE_CVE-2019-16920.json
| | | UniFi_Network_Log4shell_CVE-2021-44228.json
| | | UniFi_Network_Log4shell_CVE_2021_44228.json
| | | VENGD_Arbitrary_File_Upload.json
| | | VMWare_Horizon_Log4shell_CVE-2021-44228.json
| | | VMWare_Horizon_Log4shell_CVE_2021_44228.json
| | | VMware_NSX_Log4shell_CVE-2021-44228.json
| | | VMware_NSX_Log4shell_CVE_2021_44228.json
| | | VMWare_Operations_vRealize_Operations_Manager_API_SSRF_CVE_2021_21975.json
| | | VMware_vCenter_Log4shell_CVE-2021-44228_(1).json
| | | VMware_vCenter_Log4shell_CVE_2021_44228_1.json
| | | VMware_vCenter_v7.0.2_Arbitrary_File_Read.json
| | | VMware_Workspace_ONE_Access_and_Identity_Manager_Server_Side_Template_Injection_CVE_2022_22954.json
| | | VMware_Workspace_ONE_Access_RCE_CVE_2022_22954.json
| | | WangKang_Next_generation_firewall_router_RCE.go
| | | WangKang_NS_ASG_cert_download.php_File_read.go
| | | wangyixingyun_waf_Information_leakage.json
| | | WAVLINK_WN535G3_POST_XSS_CVE_2022_30489.json
| | | Wayos AC集中管理系统默认弱口令 CNVD-2021-00876.json
| | | Wayos_AC_Centralized_management_system_Default_Password_CNVD_2021_00876.json
| | | Wayos_AC_Centralized_management_system_Default_weak_password.json
| | | Weaver_EOffice_Arbitrary_File_Upload_CNVD-2021-49104.json
| | | Weaver_EOffice_Arbitrary_File_Upload_CNVD_2021_49104.json
| | | Weaver_e_cology_OA_XStream_RCE_CVE_2021_21350.go
| | | Weaver_e_office_UploadFile.php_file_upload_CNVD_2021_49104.json
| | | Weaver_OA_8_SQL_injection.json
| | | weaver_OA_E_Cology_getSqlData_SQL_injection_vulnerability.json
| | | Weaver_OA_E_Cology_Workflowservicexml_RCE.go
| | | Webgrind_File_read_cve_2018_12909.go
| | | Weblogic LDAP Internet RCE CVE-2021-2109.json
| | | Weblogic LDAP 远程代码执行漏洞 CVE-2021-2109.json
| | | Weblogic SSRF漏洞 CVE-2014-4210.json
| | | Weblogic_LDAP_RCE_CVE_2021_2109.json
| | | Weblogic_SSRF.json
| | | WebSVN_before_2.6.1_Injection_RCE_CVE_2021_32305.json
| | | WordPress_Simple_Ajax_Chat_plugin_InfoLeak_CVE_2022_27849.json
| | | WordPress_WPQA_plugin_Unauthenticated_Private_Message_Disclosure_CVE_2022_1598.json
| | | WSO2_fileupload_CVE_2022_29464.json
| | | WSO2_Management_Console_Reflected_XSS_CVE_2022_29548.json
| | | WSO2_Management_Console_Unrestricted_Arbitrary_File_Upload_RCE_CVE_2022_29464.json
| | | xiaomi_Mi_wiFi_From_File_Read_To_Login_CVE_2019_18370.go
| | | Xieda_oa.json
| | | Xieda_OA_Filedownload_CNVD_2021_29066.json
| | | XXL-JOB 任务调度中心 后台默认弱口令.json
| | | XXL_JOB_Default_Login.json
| | | XXL_JOB_Default_password.json
| | | YAPI_RCE.json
| | | YCCMS_XSS.json
| | | Yinpeng_Hanming_Video_Conferencing_Filedownload_CNVD_2020_62437.json
| | | Yinpeng_Hanming_Video_Conferencing__Arbitrary_file_read.json
| | | yiyou__moni_detail.do_Remote_command_execution.json
| | | yongyou_NC_bsh.servlet.BshServlet_RCE.json
| | | Yonyou_UFIDA_NC_bsh.servlet.BshServlet_rce.json
| | | yuanchuangxianfeng_unauthorized_access_vulnerability.json
| | | yunshidai_ERP_SQL_injection.json
| | | yycms_XSS.json
| | | zabbix_saml_cve_2022_23131.json
| | | Zhejiang_Dahua_DSS_System_Filedownload_CNVD_2020_61986.json
| | | zhihuipingtai_FileDownLoad.aspx_Arbitrary_file_read_vulnerability.json
| | | ZhongkeWangwei_Next_generation_firewall_File_read.go
| | | ZhongQing_naibo_Education_Cloud_Platform_Information_leakage.go
| | | ZhongQing_naibo_Education_Cloud_platform_reset_password.go
| | | Zhongxing_F460_web_shell_cmd.gch_RCE.go
| | | ZhongXinJingDun_Default_administrator_password.json
| | | ZhongXinJingDun_Information_Security_Management_System_Default_Login.json
| | | ZhongYuan_iAudit_get_luser_by_sshport.php_RCE.go
| | | ziguang_editPass.html_SQL_injection_CNVD_2021_41638.json
| | | ZZZCMS_parserSearch_RCE.go
| | | ZZZCMS_parserSearch_RCE.go.json
| | | 帆软报表 v8.0 任意文件读取漏洞 CNVD-2018-04757.json
| | | 来福云SQL注入漏洞.json
| | | 致远OA A6 数据库敏感信息泄露.json
| | | 致远OA A6 用户敏感信息泄露.json
| | | 致远OA webmail.do任意文件下载 CNVD-2020-62422.json
| | | 蜂网互联 企业级路由器v4.31 密码泄露漏洞 CVE-2019-16313.json
| | | 锐捷NBR路由器 EWEB网管系统 远程命令执行漏洞.json
| | |
| | +---images
| | | goby.jpg
| | |
| | \---nuclei_pocs
| | admin-file-search.yaml
| | aem-detection.yaml
| | AEM_misconfig.yaml
| | alibaba-canal-info-leak.yaml
| | apache-druid-detect.yaml
| | apache-druid-unauth.yaml
| | apache-filename-brute-force.yaml
| | apache-loadbalancer.yaml
| | apache-nifi-unauth.yaml
| | apache-serverstatus.yaml
| | apache-status-page.yaml
| | api-keys.yaml
| | api_endpoints.yaml
| | apple_app_site.yaml
| | application-ini.yaml
| | artifactory_deploy.yaml
| | auth-js.yaml
| | avtech-dvr-exposure.yaml
| | aws-ec2-sto.yaml
| | aws-metadata.yaml
| | aws-s3-open-bucket.yaml
| | axis2-detect.yaml
| | base64_strings.yaml
| | basic-auth-detection.yaml
| | beward-ipcamera-disclosure.yaml
| | blind-xxe.yaml
| | cacti-detect.yaml
| | chamilo-lms-xss.yaml
| | circarlife-default-login.yaml
| | circleci-config.yaml
| | circleci-ssh-config.yaml
| | clickhouse-db-detect.yaml
| | clickhouse-db-unauth.yaml
| | coldfusion-lucee-auth-bypass.yaml
| | common-error-00.yaml
| | common-error-01.yaml
| | common-forbidden-bypass.yaml
| | comtrend-ct5367-remote-root.yaml
| | config-file.yaml
| | config-ini.yaml
| | config-js.yaml
| | connect-proxy.yaml
| | content_injection.yaml
| | control4-default-login.yaml
| | cors-00.yaml
| | cors-01.yaml
| | couchbase-buckets-rest-api.yaml
| | crlf.yaml
| | CVE-2005-2428.yaml
| | CVE-2007-0885.yaml
| | CVE-2009-0545.yaml
| | CVE-2009-4223.yaml
| | CVE-2010-1871.yaml
| | CVE-2011-4618.yaml
| | CVE-2011-4624.yaml
| | CVE-2011-4926.yaml
| | CVE-2011-5107.yaml
| | CVE-2011-5179.yaml
| | CVE-2011-5181.yaml
| | CVE-2011-5265.yaml
| | CVE-2012-0901.yaml
| | CVE-2012-2371.yaml
| | CVE-2012-4242.yaml
| | CVE-2012-5913.yaml
| | CVE-2013-2287.yaml
| | CVE-2013-3526.yaml
| | CVE-2014-2321.yaml
| | CVE-2014-2323.yaml
| | CVE-2014-9094.yaml
| | CVE-2015-6477.yaml
| | CVE-2016-0957.yaml
| | CVE-2017-0929.yaml
| | CVE-2017-10075.yaml
| | CVE-2017-11444.yaml
| | CVE-2017-12615.yaml
| | CVE-2017-14849.yaml
| | CVE-2017-15715.yaml
| | CVE-2017-16806.yaml
| | CVE-2017-17562.yaml
| | CVE-2017-5487.yaml
| | CVE-2017-5638.yaml
| | CVE-2017-6360.yaml
| | CVE-2017-6361.yaml
| | CVE-2017-7391.yaml
| | CVE-2017-7529.yaml
| | CVE-2017-9506.yaml
| | CVE-2017-9841.yaml
| | CVE-2018-0296.yaml
| | CVE-2018-1000129.yaml
| | CVE-2018-1000600.yaml
| | CVE-2018-11409.yaml
| | CVE-2018-11759.yaml
| | CVE-2018-11784.yaml
| | CVE-2018-1247.yaml
| | CVE-2018-12634.yaml
| | CVE-2018-1271.yaml
| | CVE-2018-13379.yaml
| | CVE-2018-14728.yaml
| | CVE-2018-15640.yaml
| | CVE-2018-16341.yaml
| | CVE-2018-16668.yaml
| | CVE-2018-16670.yaml
| | CVE-2018-16671.yaml
| | CVE-2018-16763.yaml
| | CVE-2018-18069.yaml
| | CVE-2018-18264.yaml
| | CVE-2018-18326.yaml
| | CVE-2018-19386.yaml
| | CVE-2018-19439.yaml
| | CVE-2018-20062.yaml
| | CVE-2018-20824.yaml
| | CVE-2018-2791.yaml
| | CVE-2018-2894.yaml
| | CVE-2018-3167.yaml
| | CVE-2018-3714.yaml
| | CVE-2018-3760.yaml
| | CVE-2018-5230.yaml
| | CVE-2018-6389.yaml
| | CVE-2018-7490.yaml
| | CVE-2018-9126.yaml
| | CVE-2019-0230.yaml
| | CVE-2019-10475.yaml
| | CVE-2019-11043.yaml
| | CVE-2019-11248.yaml
| | CVE-2019-11510.yaml
| | CVE-2019-11580.yaml
| | cve-2019-11581.yaml
| | CVE-2019-11600.yaml
| | CVE-2019-12314.yaml
| | CVE-2019-12461.yaml
| | CVE-2019-12593.yaml
| | CVE-2019-14205.yaml
| | CVE-2019-14322.yaml
| | CVE-2019-14470.yaml
| | CVE-2019-14696.yaml
| | CVE-2019-14974.yaml
| | CVE-2019-15043.yaml
| | CVE-2019-15859.yaml
| | CVE-2019-15889.yaml
| | CVE-2019-16097.yaml
| | CVE-2019-16278.yaml
| | CVE-2019-1653.yaml
| | CVE-2019-16662.yaml
| | CVE-2019-16759.yaml
| | CVE-2019-17382.yaml
| | CVE-2019-17558.yaml
| | CVE-2019-18394.yaml
| | CVE-2019-19368.yaml
| | CVE-2019-19719.yaml
| | CVE-2019-19781.yaml
| | CVE-2019-19908.yaml
| | CVE-2019-19985.yaml
| | CVE-2019-20141.yaml
| | CVE-2019-2588.yaml
| | CVE-2019-2725.yaml
| | CVE-2019-3799.yaml
| | CVE-2019-5418.yaml
| | CVE-2019-6112.yaml
| | CVE-2019-7192.yaml
| | CVE-2019-7238.yaml
| | CVE-2019-7609.yaml
| | CVE-2019-8442.yaml
| | CVE-2019-8446.yaml
| | CVE-2019-8449.yaml
| | CVE-2019-8451.yaml
| | CVE-2019-8903.yaml
| | CVE-2019-8982.yaml
| | CVE-2019-9082.yaml
| | cve-2019-9670.yaml
| | CVE-2019-9978.yaml
| | CVE-2020-0618.yaml
| | CVE-2020-10148.yaml
| | CVE-2020-10199.yaml
| | CVE-2020-10204.yaml
| | CVE-2020-10220.yaml
| | CVE-2020-11034.yaml
| | CVE-2020-11450.yaml
| | CVE-2020-1147.yaml
| | CVE-2020-11530.yaml
| | CVE-2020-11710.yaml
| | CVE-2020-11854.yaml
| | CVE-2020-12145.yaml
| | CVE-2020-12271.yaml
| | CVE-2020-12720.yaml
| | CVE-2020-13167.yaml
| | CVE-2020-13379.yaml
| | CVE-2020-13937.yaml
| | CVE-2020-13942.yaml
| | CVE-2020-14179.yaml
| | CVE-2020-14181.yaml
| | CVE-2020-14750.yaml
| | CVE-2020-14882-1.yaml
| | CVE-2020-14882-2.yaml
| | CVE-2020-14882.yaml
| | CVE-2020-15004.yaml
| | CVE-2020-15129.yaml
| | CVE-2020-15505.yaml
| | CVE-2020-15920.yaml
| | CVE-2020-16139.yaml
| | CVE-2020-16270.yaml
| | CVE-2020-16846.yaml
| | CVE-2020-16952.yaml
| | CVE-2020-17506.yaml
| | CVE-2020-19625.yaml
| | CVE-2020-2096.yaml
| | CVE-2020-2140.yaml
| | CVE-2020-2199.yaml
| | CVE-2020-22840.yaml
| | CVE-2020-23517.yaml
| | CVE-2020-24223.yaml
| | CVE-2020-24312.yaml
| | CVE-2020-24550.yaml
| | CVE-2020-24609.yaml
| | CVE-2020-24765.yaml
| | CVE-2020-24949.yaml
| | CVE-2020-25213.yaml
| | CVE-2020-2551.yaml
| | CVE-2020-25540.yaml
| | CVE-2020-26073.yaml
| | CVE-2020-27982.yaml
| | CVE-2020-28188.yaml
| | CVE-2020-29164.yaml
| | CVE-2020-29395.yaml
| | CVE-2020-3187.yaml
| | CVE-2020-3452.yaml
| | CVE-2020-35846.yaml
| | CVE-2020-36112.yaml
| | CVE-2020-3952.yaml
| | CVE-2020-4038.yaml
| | CVE-2020-4463.yaml
| | CVE-2020-5284.yaml
| | CVE-2020-5377.yaml
| | CVE-2020-5398.yaml
| | CVE-2020-5405.yaml
| | CVE-2020-5410.yaml
| | CVE-2020-5412.yaml
| | CVE-2020-5777.yaml
| | CVE-2020-5902.yaml
| | CVE-2020-6287.yaml
| | CVE-2020-7048.yaml
| | CVE-2020-7209.yaml
| | CVE-2020-7246.yaml
| | CVE-2020-7473.yaml
| | CVE-2020-8091.yaml
| | CVE-2020-8115.yaml
| | CVE-2020-8163.yaml
| | CVE-2020-8193.yaml
| | CVE-2020-8209.yaml
| | CVE-2020-8512.yaml
| | CVE-2020-8772.yaml
| | CVE-2020-8982.yaml
| | CVE-2020-9047.yaml
| | CVE-2020-9054.yaml
| | CVE-2020-9315.yaml
| | CVE-2020-9344.yaml
| | CVE-2020-9402.yaml
| | CVE-2020-9484.yaml
| | CVE-2020-9757.yaml
| | CVE-2021-20837.yaml
| | CVE-2021-21402.yaml
| | CVE-2021-21972.yaml
| | CVE-2021-21975.yaml
| | CVE-2021-21978.yaml
| | CVE-2021-22122.yaml
| | CVE-2021-22873.yaml
| | CVE-2021-24286.yaml
| | CVE-2021-24291.yaml
| | CVE-2021-25646.yaml
| | CVE-2021-26475.yaml
| | CVE-2021-27132.yaml
| | CVE-2021-28937.yaml
| | CVE-2021-29622.yaml
| | CVE-2021-30461.yaml
| | CVE-2021-31249.yaml
| | CVE-2021-31250.yaml
| | CVE-2021-31537.yaml
| | CVE-2021-31581.yaml
| | CVE-2021-31800.yaml
| | CVE-2021-32820.yaml
| | CVE-2021-33221.yaml
| | CVE-2021-3374.yaml
| | CVE-2021-3377.yaml
| | CVE-2021-3378.yaml
| | CVE-2021-33904.yaml
| | darkstat-detect.yaml
| | db-schema.yaml
| | dbeaver-credentials.yaml
| | dbeaver-data-sources.yaml
| | default-config.yaml
| | detect-dns-over-https.yaml
| | detect-drone.yaml
| | detect-rsyncd.yaml
| | detect-tracer-sc-web.yaml
| | detect-workerman-websocket-server.yaml
| | developer_notes.yaml
| | development-logs.yaml
| | dir-listing.yaml
| | dir-traversal.yaml
| | display-via-header.yaml
| | django-debug-enable.yaml
| | django-debug-toolbar.yaml
| | django-debug.yaml
| | Django-DebugMode.yaml
| | django-secret.key.yaml
| | docker-k8s.yaml
| | docker-registry.yaml
| | dockercfg.yaml
| | dom-xss.yaml
| | elasticsearch-cluster-health.yaml
| | email-extraction.yaml
| | error-based-sql-injection.yaml
| | error-logs.yaml
| | errors-n-vulns.yaml
| | esmtprc.yaml
| | exposed-bitkeeper.yaml
| | exposed-bzr.yaml
| | exposed-darcs.yaml
| | exposed-hg.yaml
| | exposed-pii.yaml
| | eyelock-nano-lfd.yaml
| | favinizer.yaml
| | ffserver-detect.yaml
| | firebase-config.yaml
| | firebase_urls.yaml
| | fps-config.yaml
| | ftpconfig.yaml
| | fuzz-oauth.yaml
| | ganglia-xml-grid-monitor.yaml
| | git-credentials.yaml
| | git-mailmap.yaml
| | gitleak.yaml
| | globalprotect-xss.yaml
| | gloo-unauth.yaml
| | glpi-fusioninventory-misconfig.yaml
| | gmail-api-client-secrets.yaml
| | go-pprof-exposed.yaml
| | go-pprof.yaml
| | gogs-install-exposure.yaml
| | goliath-detect.yaml
| | google-floc-disabled.yaml
| | graphite-browser-default-credential.yaml
| | graphite-browser-detect.yaml
| | graphql-playround-xss.yaml
| | graphql_get.yaml
| | hadoop-unauth.yaml
| | haproxy-stat.yaml
| | hashicorp-consul-rce.yaml
| | header-blind-sql-injection.yaml
| | header-blind-ssrf.yaml
| | header-command-injection.yaml
| | header_blind_xss.yaml
| | header_reflection.yaml
| | header_reflection_body.yaml
| | header_sqli.yaml
| | header_user_id.yaml
| | homeworks-illumination-web-keypad.yaml
| | host-header-auth-bypass.yaml
| | host-header-injection.yaml
| | htpasswd-detection.yaml
| | huawei-dg8045-auth-bypass.yaml
| | iis-directory-listing.yaml
| | java-melody-stat.yaml
| | jetbrains-webservers-xml.yaml
| | jetty-information-disclosure.yaml
| | jira-service-desk-signup.yaml
| | joomla-host-injection.yaml
| | joomla-lfi-comfabrik.yaml
| | joomla-sqli-hdwplayer.yaml
| | jupyter-ipython-unauth.yaml
| | kafdrop-xss.yaml
| | kafka-misconfig.yaml
| | kentico-open-redirect.yaml
| | keys-js.yaml
| | kong-detect.yaml
| | kube-dashboard-detect.yaml
| | kubeflow-dashboard-unauth.yaml
| | kubernetes-api-detect.yaml
| | landfill-remote-monitoring-control.yaml
| | laravel-telescope-exposed.yaml
| | laravel-telescope.yaml
| | lfi-00.yaml
| | lfi-01.yaml
| | lfi-02.yaml
| | lfi-03.yaml
| | lfi-04.yaml
| | lfi-05.yaml
| | lfi-06.yaml
| | logins.yaml
| | lucee-detect.yaml
| | lutron-iot-default-login.yaml
| | magento-config.yaml
| | missing-csp.yaml
| | monitorix-exposure.yaml
| | moodle-auth-xss.yaml
| | mrtg-detect.yaml
| | munin-monitoring.yaml
| | netdata-unauth.yaml
| | netgear-router-disclosure.yaml
| | netrc.yaml
| | nginx-conf-exposed.yaml
| | nginx-vhost-traffic-status.yaml
| | nginx-vhost-xss.yaml
| | nginx-vhosts-stat.yaml
| | node-nunjucks-ssti.yaml
| | npmrc.yaml
| | old-copyright.yaml
| | open-redirect-00.yaml
| | open-redirect-01.yaml
| | open-redirect-02.yaml
| | open-redirect-03.yaml
| | open-redirect-04.yaml
| | open-redirect.yaml
| | opengear-detect.yaml
| | openstack-user-secrets.yaml
| | oracle-ebs-config-disclosure.yaml
| | oracle-ebs-credentials-disclosure.yaml
| | oracle-ebs-desr.yaml
| | oracle-ebs-lfi.yaml
| | oracle-ebs-sqllog-disclosure.yaml
| | oracle-ebs-xss.yaml
| | oracle-stat.yaml
| | pagespeed-global-admin.yaml
| | perl-status-page.yaml
| | php-debug-bar.yaml
| | php-fpm-status.yaml
| | php-ini.yaml
| | php-symfony-debug.yaml
| | php-timeclock-xss.yaml
| | php-user-ini.yaml
| | pi-hole-detect.yaml
| | pinpoint-unauth.yaml
| | pmb-directory-traversal.yaml
| | production-logs.yaml
| | prtg-detect.yaml
| | public-documents.yaml
| | putty-user-keyfile.yaml
| | pyramid-debug-toolbar.yaml
| | rails-secret-token.yaml
| | random-fuzz-00.yaml
| | random-fuzz-01.yaml
| | random-fuzz-02.yaml
| | random-fuzz-03.yaml
| | redis-conf.yaml
| | redmine-cli-detect.yaml
| | redmine-db-config.yaml
| | remote-sync.yaml
| | rescro.yaml
| | robomongo.yaml
| | rocketmq-console.yaml
| | route-bypass.yaml
| | routes-ini.yaml
| | rpcbind-portmapper.yaml
| | s3cfg.yaml
| | salesforce-login.yaml
| | sap-directory-listing.yaml
| | schneider-lights.yaml
| | searches.yaml
| | secret.yaml
| | selea-ip-camera.yaml
| | server-private-keys.yaml
| | service-now-exposed.yaml
| | setPreferences-xss.yaml
| | sftp-config.yaml
| | sftp-deployment-config.yaml
| | shells.yaml
| | shell_scripts.yaml
| | simple-xss.yaml
| | soap-defination-probing.yaml
| | solar-log-500.yaml
| | sonarqube-cred.yaml
| | sony-bravia-disclosure.yaml
| | spark-unauth.yaml
| | spidercontrol-scada-server-info.yaml
| | sqli-00.yaml
| | sqli-01.yaml
| | squid-analysis-report-generator.yaml
| | squid-detect.yaml
| | SquirrelMail.yaml
| | ssh-authorized-keys.yaml
| | ssh-known-hosts.yaml
| | ssrf-by-proxy.yaml
| | stats.yaml
| | svn-leak.yaml
| | swagger-xss.yaml
| | symfony-detect.yaml
| | tectuus-scada-monitor.yaml
| | telerik-derserial.yaml
| | template-injection.yaml
| | terraform-detect.yaml
| | tor-socks-proxy.yaml
| | tox-ini.yaml
| | unauthen-elastic.yaml
| | unauthen-kibana.yaml
| | upnp-device.yaml
| | ventrilo-config.yaml
| | vernemq-status.yaml
| | viewlinc-crlf-injection.yaml
| | vscode-sftp.yaml
| | web-config.yaml
| | werkzeug-debug.yaml
| | wordpress-accessible-wpconfig.yaml
| | wordpress-directory-listing.yaml
| | wordpress-misconfig.yaml
| | wordpress-rest-api.yaml
| | wordpress-user-enum.yaml
| | wp-ambience-xss.yaml
| | wp-church-admin-xss.yaml
| | wp-finder-xss.yaml
| | wp-knews-xss.yaml
| | wp-phpfreechat-xss.yaml
| | wp-securimage-xss.yaml
| | wp-socialfit-xss.yaml
| | ws-config.yaml
| | x-hacker.yaml
| | xmlrpc-pingback-ssrf.yaml
| | xss-fuzz.yaml
| | yii-debugger.yaml
| | zabbix-creds.yaml
| | zeroshell-kerbynet-lfd.yaml
| | zipkin-unauth.yaml
| | zwave2mqtt-health-check.yaml
| |
| +---Gr33k
| | | .gitignore
| | | fix_qt_import_error.py
| | | Gr33k.exe
| | | Gr33k.py
| | | Gr33k.spec
| | | linux.ico
| | | requirements.txt
| | | weblogic_gui.py
| | | weblogic_gui.ui
| | |
| | +---build
| | | \---Gr33k
| | | Analysis-00.toc
| | | base_library.zip
| | | EXE-00.toc
| | | Gr33k.exe.manifest
| | | Gr33k.pkg
| | | PKG-00.toc
| | | PYZ-00.pyz
| | | PYZ-00.toc
| | | warn-Gr33k.txt
| | | xref-Gr33k.html
| | |
| | +---dict
| | | brute_password.txt
| | | brute_username.txt
| | | iplist.txt
| | | subdomain.txt
| | | url_index.txt
| | |
| | +---plugins
| | | | apache_rce.py
| | | | config.py
| | | | jboss.py
| | | | port_scan.py
| | | | pyshodan.py
| | | | slowhttp.py
| | | | ssh_username.py
| | | | struts2.py
| | | | subdomain.py
| | | | tomcat.py
| | | | unauthorized.py
| | | | url_scan.py
| | | | use_sqlmap.py
| | | | weblogic_exe.py
| | | | weblogic_scan.py
| | | | windows.py
| | | | __init__.py
| | | |
| | | +---brute
| | | | | Brute_ftp.py
| | | | | Brute_mysql.py
| | | | | Brute_ssh.py
| | | | | Brute_telnet.py
| | | | |
| | | | \---__pycache__
| | | | Brute_ftp.cpython-37.pyc
| | | | Brute_ftp.cpython-38.pyc
| | | | Brute_mysql.cpython-37.pyc
| | | | Brute_mysql.cpython-38.pyc
| | | | Brute_ssh.cpython-37.pyc
| | | | Brute_ssh.cpython-38.pyc
| | | | Brute_telnet.cpython-37.pyc
| | | | Brute_telnet.cpython-38.pyc
| | | |
| | | +---jbosslib
| | | | | CVE_2017_12149.py
| | | | | Runtime_payload.py
| | | | |
| | | | \---__pycache__
| | | | CVE_2017_12149.cpython-37.pyc
| | | | CVE_2017_12149.cpython-38.pyc
| | | | Runtime_payload.cpython-37.pyc
| | | | Runtime_payload.cpython-38.pyc
| | | |
| | | +---tomcatlib
| | | | | CVE_2020_1938.py
| | | | |
| | | | \---__pycache__
| | | | CVE_2020_1938.cpython-38.pyc
| | | |
| | | +---weblogic
| | | | | CVE20144210.py
| | | | | CVE20160638.py
| | | | | CVE20163510.py
| | | | | CVE201710271.py
| | | | | CVE20173248.py
| | | | | CVE20173506.py
| | | | | CVE20182628.py
| | | | | CVE20182893.py
| | | | | CVE20182894.py
| | | | | CVE20192618.py
| | | | | CVE20192725.py
| | | | | CVE20192729.py
| | | | | CVE202014882.py
| | | | | WeblogicConsole.py
| | | | |
| | | | \---__pycache__
| | | | CVE20144210.cpython-37.pyc
| | | | CVE20144210.cpython-38.pyc
| | | | CVE20160638.cpython-37.pyc
| | | | CVE20160638.cpython-38.pyc
| | | | CVE20163510.cpython-37.pyc
| | | | CVE20163510.cpython-38.pyc
| | | | CVE201710271.cpython-37.pyc
| | | | CVE201710271.cpython-38.pyc
| | | | CVE20173248.cpython-37.pyc
| | | | CVE20173248.cpython-38.pyc
| | | | CVE20173506.cpython-37.pyc
| | | | CVE20173506.cpython-38.pyc
| | | | CVE20182628.cpython-37.pyc
| | | | CVE20182628.cpython-38.pyc
| | | | CVE20182893.cpython-37.pyc
| | | | CVE20182893.cpython-38.pyc
| | | | CVE20182894.cpython-37.pyc
| | | | CVE20182894.cpython-38.pyc
| | | | CVE20192618.cpython-37.pyc
| | | | CVE20192618.cpython-38.pyc
| | | | CVE20192725.cpython-37.pyc
| | | | CVE20192725.cpython-38.pyc
| | | | CVE20192729.cpython-37.pyc
| | | | CVE20192729.cpython-38.pyc
| | | | CVE202014882.cpython-38.pyc
| | | | WeblogicConsole.cpython-37.pyc
| | | | WeblogicConsole.cpython-38.pyc
| | | |
| | | +---windowslib
| | | | | CVE_2020_0796.py
| | | | | MS17010.py
| | | | |
| | | | \---__pycache__
| | | | CVE_2020_0796.cpython-37.pyc
| | | | CVE_2020_0796.cpython-38.pyc
| | | | MS17010.cpython-37.pyc
| | | | MS17010.cpython-38.pyc
| | | |
| | | +---XSStrike
| | | | | .gitignore
| | | | | .travis.yml
| | | | | LICENSE
| | | | | requirements.txt
| | | | | t_xss.py
| | | | | xsstrike.py
| | | | | __init__.py
| | | | |
| | | | +---.github
| | | | | |
| | | | | \---ISSUE_TEMPLATE
| | | | |
| | | | +---core
| | | | | | arjun.py
| | | | | | checker.py
| | | | | | colors.py
| | | | | | config.py
| | | | | | dom.py
| | | | | | encoders.py
| | | | | | filterChecker.py
| | | | | | fuzzer.py
| | | | | | generator.py
| | | | | | htmlParser.py
| | | | | | jsContexter.py
| | | | | | log.py
| | | | | | photon.py
| | | | | | prompt.py
| | | | | | requester.py
| | | | | | updater.py
| | | | | | utils.py
| | | | | | wafDetector.py
| | | | | | zetanize.py
| | |
| | +---tool
| | | +---HQLmap-master
| | | | | HQLmap.py
| | | | |
| | | | |
| | | | +---tamper
| | | | | 0eunion.py
| | | | | apostrophemask.py
| | | | | apostrophenullencode.py
| | | | | appendnullbyte.py
| | | | | base64encode.py
| | | | | between.py
| | | | | binary.py
| | | | | bluecoat.py
| | | | | chardoubleencode.py
| | | | | charencode.py
| | | | | charunicodeencode.py
| | | | | charunicodeescape.py
| | | | | commalesslimit.py
| | | | | commalessmid.py
| | | | | commentbeforeparentheses.py
| | | | | concat2concatws.py
| | | | | dunion.py
| | | | | equaltolike.py
| | | | | equaltorlike.py
| | | | | escapequotes.py
| | | | | greatest.py
| | | | | halfversionedmorekeywords.py
| | | | | hex2char.py
| | | | | htmlencode.py
| | | | | ifnull2casewhenisnull.py
| | | | | ifnull2ifisnull.py
| | | | | informationschemacomment.py
| | | | | least.py
| | | | | lowercase.py
| | | | | luanginx.py
| | | | | misunion.py
| | | | | modsecurityversioned.py
| | | | | modsecurityzeroversioned.py
| | | | | multiplespaces.py
| | | | | overlongutf8.py
| | | | | overlongutf8more.py
| | | | | percentage.py
| | | | | plus2concat.py
| | | | | plus2fnconcat.py
| | | | | randomcase.py
| | | | | randomcomments.py
| | | | | schemasplit.py
| | | | | sleep2getlock.py
| | | | | space2comment.py
| | | | | space2dash.py
| | | | | space2hash.py
| | | | | space2morecomment.py
| | | | | space2morehash.py
| | | | | space2mssqlblank.py
| | | | | space2mssqlhash.py
| | | | | space2mysqlblank.py
| | | | | space2mysqldash.py
| | | | | space2plus.py
| | | | | space2randomblank.py
| | | | | sp_password.py
| | | | | substring2leftright.py
| | | | | symboliclogical.py
| | | | | unionalltounion.py
| | | | | unmagicquotes.py
| | | | | uppercase.py
| | | | | varnish.py
| | | | | versionedkeywords.py
| | | | | versionedmorekeywords.py
| | | | | xforwardedfor.py
| | | \---ysoserial
| | | ysoserial-master-6eca5bc740-1.jar
| | | ysoserial-master-8eb5cbfbf6-1.jar
| | |
| | \---__pycache__
| | Gr33k.cpython-38.pyc
| | weblogic_gui.cpython-38.pyc
| |
| +---heartsk
| | | HeartsK.bat
| | | HeartsK.exe
| | | HeartsK1.bat
| | |
| | +---exploits
| | license.lic
| | public.pem
| | scan.sqlite3
| | scan.sqlite3-shm
| | scan.sqlite3-wal
| |
| +---hvvoaexploit
| | HVVExploitApply1.2.jar
| |
| +---jboss
| | jboss反序列化.jar
| | jboss反序列化POC_利用.zip
| |
| +---json
| | data.txt
| | json反序列化检查工具.exe
| |
| +---LiqunKit_1.5.1
| | | config.properties
| | | config.yaml
| | | LiqunKit_1.5.1.jar
| | | shell.txt
| | |
| | +---Driver
| | | mssql.jar
| | | mysql.jar
| | | oracle.jar
| | | postgresql.jar
| | |
| | +---lib
| | | 8.jar
| | | 9.jar
| | |
| | \---Plugins
| | +---Mssql
| | | clr.txt
| | |
| | +---Mysql
| | | udf_linux32_hex.txt
| | | udf_linux64_hex.txt
| | | udf_win32_hex.txt
| | | udf_win64_hex.txt
| | | udf_win_ex_hex.txt
| | |
| | +---PostgreSql
| | | 9.0_linux_64_hex.txt
| | | 9.1_linux_64_hex.txt
| | | 9.1_windows_32_hex.txt
| | | 9.1_windows_64_hex.txt
| | | 9.2_linux_64_hex.txt
| | | 9.2_windows_32_hex.txt
| | | 9.2_windows_64_hex.txt
| | |
| | \---Redis
| | exp.so
| |
| +---LiqunShield
| | config.properties
| | LiqunShield.jar
| |
| +---Log4j
| | | config.db
| | | woodpecker-framework.1.3.3.jar
| | |
| | +---common
| | \---plugin
| | log4j-payload-generator-0.1.1.jar
| | rmi-deserialization-vuldb-0.2.0.jar
| | runtime-exec-encoder-0.2.0.jar
| | weblogic-infodetector-0.2.3.jar
| |
| +---logs
| | debug.log
| |
| +---md5
| | MD5.bat
| | MD5.exe
| | md5.txt
| | 解密明文.txt
| |
| +---Multiple.Database.Utilization.Tools
| | | data.db
| | | Multiple.Database.Utilization.Tools-2.1.1-jar-with-dependencies.jar
| | |
| | +---Driver
| | | mssql.jar
| | | mysql.jar
| | | oracle.jar
| | | postgresql.jar
| | |
| | \---Plugins
| | +---Mssql
| | | clr.txt
| | |
| | +---Mysql
| | | udf_linux32_hex.txt
| | | udf_linux64_hex.txt
| | | udf_win32_hex.txt
| | | udf_win64_hex.txt
| | | udf_win_ex_hex.txt
| | |
| | +---Oracle
| | | FileUtil.java
| | | ShellUtil.java
| | |
| | +---PostgreSql
| | | 9.0_linux_64_hex.txt
| | | 9.1_linux_64_hex.txt
| | | 9.1_windows_32_hex.txt
| | | 9.1_windows_64_hex.txt
| | | 9.2_linux_64_hex.txt
| | | 9.2_windows_32_hex.txt
| | | 9.2_windows_64_hex.txt
| | |
| | +---Redis
| | | exp.so
| | | redis-cus-rogue.py
| | |
| | \---Template
| | mssql_tunnel.aspx
| | mysql_tunnel.php
| | oracle_tunnel.jsp
| | postgresql_tunnel.php
| |
| +---nuclei
| | | nuclei.bat
| | | nuclei.exe
| | | nuclei1.bat
| | |
| | \---nuclei_pocs
| | admin-file-search.yaml
| | aem-detection.yaml
| | AEM_misconfig.yaml
| | alibaba-canal-info-leak.yaml
| | apache-druid-detect.yaml
| | apache-druid-unauth.yaml
| | apache-filename-brute-force.yaml
| | apache-loadbalancer.yaml
| | apache-nifi-unauth.yaml
| | apache-serverstatus.yaml
| | apache-status-page.yaml
| | api-keys.yaml
| | api_endpoints.yaml
| | apple_app_site.yaml
| | application-ini.yaml
| | artifactory_deploy.yaml
| | auth-js.yaml
| | avtech-dvr-exposure.yaml
| | aws-ec2-sto.yaml
| | aws-metadata.yaml
| | aws-s3-open-bucket.yaml
| | axis2-detect.yaml
| | base64_strings.yaml
| | basic-auth-detection.yaml
| | beward-ipcamera-disclosure.yaml
| | blind-xxe.yaml
| | cacti-detect.yaml
| | chamilo-lms-xss.yaml
| | circarlife-default-login.yaml
| | circleci-config.yaml
| | circleci-ssh-config.yaml
| | clickhouse-db-detect.yaml
| | clickhouse-db-unauth.yaml
| | coldfusion-lucee-auth-bypass.yaml
| | common-error-00.yaml
| | common-error-01.yaml
| | common-forbidden-bypass.yaml
| | comtrend-ct5367-remote-root.yaml
| | config-file.yaml
| | config-ini.yaml
| | config-js.yaml
| | connect-proxy.yaml
| | content_injection.yaml
| | control4-default-login.yaml
| | cors-00.yaml
| | cors-01.yaml
| | couchbase-buckets-rest-api.yaml
| | crlf.yaml
| | CVE-2005-2428.yaml
| | CVE-2007-0885.yaml
| | CVE-2009-0545.yaml
| | CVE-2009-4223.yaml
| | CVE-2010-1871.yaml
| | CVE-2011-4618.yaml
| | CVE-2011-4624.yaml
| | CVE-2011-4926.yaml
| | CVE-2011-5107.yaml
| | CVE-2011-5179.yaml
| | CVE-2011-5181.yaml
| | CVE-2011-5265.yaml
| | CVE-2012-0901.yaml
| | CVE-2012-2371.yaml
| | CVE-2012-4242.yaml
| | CVE-2012-5913.yaml
| | CVE-2013-2287.yaml
| | CVE-2013-3526.yaml
| | CVE-2014-2321.yaml
| | CVE-2014-2323.yaml
| | CVE-2014-9094.yaml
| | CVE-2015-6477.yaml
| | CVE-2016-0957.yaml
| | CVE-2017-0929.yaml
| | CVE-2017-10075.yaml
| | CVE-2017-11444.yaml
| | CVE-2017-12615.yaml
| | CVE-2017-14849.yaml
| | CVE-2017-15715.yaml
| | CVE-2017-16806.yaml
| | CVE-2017-17562.yaml
| | CVE-2017-5487.yaml
| | CVE-2017-5638.yaml
| | CVE-2017-6360.yaml
| | CVE-2017-6361.yaml
| | CVE-2017-7391.yaml
| | CVE-2017-7529.yaml
| | CVE-2017-9506.yaml
| | CVE-2017-9841.yaml
| | CVE-2018-0296.yaml
| | CVE-2018-1000129.yaml
| | CVE-2018-1000600.yaml
| | CVE-2018-11409.yaml
| | CVE-2018-11759.yaml
| | CVE-2018-11784.yaml
| | CVE-2018-1247.yaml
| | CVE-2018-12634.yaml
| | CVE-2018-1271.yaml
| | CVE-2018-13379.yaml
| | CVE-2018-14728.yaml
| | CVE-2018-15640.yaml
| | CVE-2018-16341.yaml
| | CVE-2018-16668.yaml
| | CVE-2018-16670.yaml
| | CVE-2018-16671.yaml
| | CVE-2018-16763.yaml
| | CVE-2018-18069.yaml
| | CVE-2018-18264.yaml
| | CVE-2018-18326.yaml
| | CVE-2018-19386.yaml
| | CVE-2018-19439.yaml
| | CVE-2018-20062.yaml
| | CVE-2018-20824.yaml
| | CVE-2018-2791.yaml
| | CVE-2018-2894.yaml
| | CVE-2018-3167.yaml
| | CVE-2018-3714.yaml
| | CVE-2018-3760.yaml
| | CVE-2018-5230.yaml
| | CVE-2018-6389.yaml
| | CVE-2018-7490.yaml
| | CVE-2018-9126.yaml
| | CVE-2019-0230.yaml
| | CVE-2019-10475.yaml
| | CVE-2019-11043.yaml
| | CVE-2019-11248.yaml
| | CVE-2019-11510.yaml
| | CVE-2019-11580.yaml
| | cve-2019-11581.yaml
| | CVE-2019-11600.yaml
| | CVE-2019-12314.yaml
| | CVE-2019-12461.yaml
| | CVE-2019-12593.yaml
| | CVE-2019-14205.yaml
| | CVE-2019-14322.yaml
| | CVE-2019-14470.yaml
| | CVE-2019-14696.yaml
| | CVE-2019-14974.yaml
| | CVE-2019-15043.yaml
| | CVE-2019-15859.yaml
| | CVE-2019-15889.yaml
| | CVE-2019-16097.yaml
| | CVE-2019-16278.yaml
| | CVE-2019-1653.yaml
| | CVE-2019-16662.yaml
| | CVE-2019-16759.yaml
| | CVE-2019-17382.yaml
| | CVE-2019-17558.yaml
| | CVE-2019-18394.yaml
| | CVE-2019-19368.yaml
| | CVE-2019-19719.yaml
| | CVE-2019-19781.yaml
| | CVE-2019-19908.yaml
| | CVE-2019-19985.yaml
| | CVE-2019-20141.yaml
| | CVE-2019-2588.yaml
| | CVE-2019-2725.yaml
| | CVE-2019-3799.yaml
| | CVE-2019-5418.yaml
| | CVE-2019-6112.yaml
| | CVE-2019-7192.yaml
| | CVE-2019-7238.yaml
| | CVE-2019-7609.yaml
| | CVE-2019-8442.yaml
| | CVE-2019-8446.yaml
| | CVE-2019-8449.yaml
| | CVE-2019-8451.yaml
| | CVE-2019-8903.yaml
| | CVE-2019-8982.yaml
| | CVE-2019-9082.yaml
| | cve-2019-9670.yaml
| | CVE-2019-9978.yaml
| | CVE-2020-0618.yaml
| | CVE-2020-10148.yaml
| | CVE-2020-10199.yaml
| | CVE-2020-10204.yaml
| | CVE-2020-10220.yaml
| | CVE-2020-11034.yaml
| | CVE-2020-11450.yaml
| | CVE-2020-1147.yaml
| | CVE-2020-11530.yaml
| | CVE-2020-11710.yaml
| | CVE-2020-11854.yaml
| | CVE-2020-12145.yaml
| | CVE-2020-12271.yaml
| | CVE-2020-12720.yaml
| | CVE-2020-13167.yaml
| | CVE-2020-13379.yaml
| | CVE-2020-13937.yaml
| | CVE-2020-13942.yaml
| | CVE-2020-14179.yaml
| | CVE-2020-14181.yaml
| | CVE-2020-14750.yaml
| | CVE-2020-14882-1.yaml
| | CVE-2020-14882-2.yaml
| | CVE-2020-14882.yaml
| | CVE-2020-15004.yaml
| | CVE-2020-15129.yaml
| | CVE-2020-15505.yaml
| | CVE-2020-15920.yaml
| | CVE-2020-16139.yaml
| | CVE-2020-16270.yaml
| | CVE-2020-16846.yaml
| | CVE-2020-16952.yaml
| | CVE-2020-17506.yaml
| | CVE-2020-19625.yaml
| | CVE-2020-2096.yaml
| | CVE-2020-2140.yaml
| | CVE-2020-2199.yaml
| | CVE-2020-22840.yaml
| | CVE-2020-23517.yaml
| | CVE-2020-24223.yaml
| | CVE-2020-24312.yaml
| | CVE-2020-24550.yaml
| | CVE-2020-24609.yaml
| | CVE-2020-24765.yaml
| | CVE-2020-24949.yaml
| | CVE-2020-25213.yaml
| | CVE-2020-2551.yaml
| | CVE-2020-25540.yaml
| | CVE-2020-26073.yaml
| | CVE-2020-27982.yaml
| | CVE-2020-28188.yaml
| | CVE-2020-29164.yaml
| | CVE-2020-29395.yaml
| | CVE-2020-3187.yaml
| | CVE-2020-3452.yaml
| | CVE-2020-35846.yaml
| | CVE-2020-36112.yaml
| | CVE-2020-3952.yaml
| | CVE-2020-4038.yaml
| | CVE-2020-4463.yaml
| | CVE-2020-5284.yaml
| | CVE-2020-5377.yaml
| | CVE-2020-5398.yaml
| | CVE-2020-5405.yaml
| | CVE-2020-5410.yaml
| | CVE-2020-5412.yaml
| | CVE-2020-5777.yaml
| | CVE-2020-5902.yaml
| | CVE-2020-6287.yaml
| | CVE-2020-7048.yaml
| | CVE-2020-7209.yaml
| | CVE-2020-7246.yaml
| | CVE-2020-7473.yaml
| | CVE-2020-8091.yaml
| | CVE-2020-8115.yaml
| | CVE-2020-8163.yaml
| | CVE-2020-8193.yaml
| | CVE-2020-8209.yaml
| | CVE-2020-8512.yaml
| | CVE-2020-8772.yaml
| | CVE-2020-8982.yaml
| | CVE-2020-9047.yaml
| | CVE-2020-9054.yaml
| | CVE-2020-9315.yaml
| | CVE-2020-9344.yaml
| | CVE-2020-9402.yaml
| | CVE-2020-9484.yaml
| | CVE-2020-9757.yaml
| | CVE-2021-20837.yaml
| | CVE-2021-21402.yaml
| | CVE-2021-21972.yaml
| | CVE-2021-21975.yaml
| | CVE-2021-21978.yaml
| | CVE-2021-22122.yaml
| | CVE-2021-22873.yaml
| | CVE-2021-24286.yaml
| | CVE-2021-24291.yaml
| | CVE-2021-25646.yaml
| | CVE-2021-26475.yaml
| | CVE-2021-27132.yaml
| | CVE-2021-28937.yaml
| | CVE-2021-29622.yaml
| | CVE-2021-30461.yaml
| | CVE-2021-31249.yaml
| | CVE-2021-31250.yaml
| | CVE-2021-31537.yaml
| | CVE-2021-31581.yaml
| | CVE-2021-31800.yaml
| | CVE-2021-32820.yaml
| | CVE-2021-33221.yaml
| | CVE-2021-3374.yaml
| | CVE-2021-3377.yaml
| | CVE-2021-3378.yaml
| | CVE-2021-33904.yaml
| | darkstat-detect.yaml
| | db-schema.yaml
| | dbeaver-credentials.yaml
| | dbeaver-data-sources.yaml
| | default-config.yaml
| | detect-dns-over-https.yaml
| | detect-drone.yaml
| | detect-rsyncd.yaml
| | detect-tracer-sc-web.yaml
| | detect-workerman-websocket-server.yaml
| | developer_notes.yaml
| | development-logs.yaml
| | dir-listing.yaml
| | dir-traversal.yaml
| | display-via-header.yaml
| | django-debug-enable.yaml
| | django-debug-toolbar.yaml
| | django-debug.yaml
| | Django-DebugMode.yaml
| | django-secret.key.yaml
| | docker-k8s.yaml
| | docker-registry.yaml
| | dockercfg.yaml
| | dom-xss.yaml
| | elasticsearch-cluster-health.yaml
| | email-extraction.yaml
| | error-based-sql-injection.yaml
| | error-logs.yaml
| | errors-n-vulns.yaml
| | esmtprc.yaml
| | exposed-bitkeeper.yaml
| | exposed-bzr.yaml
| | exposed-darcs.yaml
| | exposed-hg.yaml
| | exposed-pii.yaml
| | eyelock-nano-lfd.yaml
| | favinizer.yaml
| | ffserver-detect.yaml
| | firebase-config.yaml
| | firebase_urls.yaml
| | fps-config.yaml
| | ftpconfig.yaml
| | fuzz-oauth.yaml
| | ganglia-xml-grid-monitor.yaml
| | git-credentials.yaml
| | git-mailmap.yaml
| | gitleak.yaml
| | globalprotect-xss.yaml
| | gloo-unauth.yaml
| | glpi-fusioninventory-misconfig.yaml
| | gmail-api-client-secrets.yaml
| | go-pprof-exposed.yaml
| | go-pprof.yaml
| | gogs-install-exposure.yaml
| | goliath-detect.yaml
| | google-floc-disabled.yaml
| | graphite-browser-default-credential.yaml
| | graphite-browser-detect.yaml
| | graphql-playround-xss.yaml
| | graphql_get.yaml
| | hadoop-unauth.yaml
| | haproxy-stat.yaml
| | hashicorp-consul-rce.yaml
| | header-blind-sql-injection.yaml
| | header-blind-ssrf.yaml
| | header-command-injection.yaml
| | header_blind_xss.yaml
| | header_reflection.yaml
| | header_reflection_body.yaml
| | header_sqli.yaml
| | header_user_id.yaml
| | homeworks-illumination-web-keypad.yaml
| | host-header-auth-bypass.yaml
| | host-header-injection.yaml
| | htpasswd-detection.yaml
| | huawei-dg8045-auth-bypass.yaml
| | iis-directory-listing.yaml
| | java-melody-stat.yaml
| | jetbrains-webservers-xml.yaml
| | jetty-information-disclosure.yaml
| | jira-service-desk-signup.yaml
| | joomla-host-injection.yaml
| | joomla-lfi-comfabrik.yaml
| | joomla-sqli-hdwplayer.yaml
| | jupyter-ipython-unauth.yaml
| | kafdrop-xss.yaml
| | kafka-misconfig.yaml
| | kentico-open-redirect.yaml
| | keys-js.yaml
| | kong-detect.yaml
| | kube-dashboard-detect.yaml
| | kubeflow-dashboard-unauth.yaml
| | kubernetes-api-detect.yaml
| | landfill-remote-monitoring-control.yaml
| | laravel-telescope-exposed.yaml
| | laravel-telescope.yaml
| | lfi-00.yaml
| | lfi-01.yaml
| | lfi-02.yaml
| | lfi-03.yaml
| | lfi-04.yaml
| | lfi-05.yaml
| | lfi-06.yaml
| | logins.yaml
| | lucee-detect.yaml
| | lutron-iot-default-login.yaml
| | magento-config.yaml
| | missing-csp.yaml
| | monitorix-exposure.yaml
| | moodle-auth-xss.yaml
| | mrtg-detect.yaml
| | munin-monitoring.yaml
| | netdata-unauth.yaml
| | netgear-router-disclosure.yaml
| | netrc.yaml
| | nginx-conf-exposed.yaml
| | nginx-vhost-traffic-status.yaml
| | nginx-vhost-xss.yaml
| | nginx-vhosts-stat.yaml
| | node-nunjucks-ssti.yaml
| | npmrc.yaml
| | old-copyright.yaml
| | open-redirect-00.yaml
| | open-redirect-01.yaml
| | open-redirect-02.yaml
| | open-redirect-03.yaml
| | open-redirect-04.yaml
| | open-redirect.yaml
| | opengear-detect.yaml
| | openstack-user-secrets.yaml
| | oracle-ebs-config-disclosure.yaml
| | oracle-ebs-credentials-disclosure.yaml
| | oracle-ebs-desr.yaml
| | oracle-ebs-lfi.yaml
| | oracle-ebs-sqllog-disclosure.yaml
| | oracle-ebs-xss.yaml
| | oracle-stat.yaml
| | pagespeed-global-admin.yaml
| | perl-status-page.yaml
| | php-debug-bar.yaml
| | php-fpm-status.yaml
| | php-ini.yaml
| | php-symfony-debug.yaml
| | php-timeclock-xss.yaml
| | php-user-ini.yaml
| | pi-hole-detect.yaml
| | pinpoint-unauth.yaml
| | pmb-directory-traversal.yaml
| | production-logs.yaml
| | prtg-detect.yaml
| | public-documents.yaml
| | putty-user-keyfile.yaml
| | pyramid-debug-toolbar.yaml
| | rails-secret-token.yaml
| | random-fuzz-00.yaml
| | random-fuzz-01.yaml
| | random-fuzz-02.yaml
| | random-fuzz-03.yaml
| | redis-conf.yaml
| | redmine-cli-detect.yaml
| | redmine-db-config.yaml
| | remote-sync.yaml
| | rescro.yaml
| | robomongo.yaml
| | rocketmq-console.yaml
| | route-bypass.yaml
| | routes-ini.yaml
| | rpcbind-portmapper.yaml
| | s3cfg.yaml
| | salesforce-login.yaml
| | sap-directory-listing.yaml
| | schneider-lights.yaml
| | searches.yaml
| | secret.yaml
| | selea-ip-camera.yaml
| | server-private-keys.yaml
| | service-now-exposed.yaml
| | setPreferences-xss.yaml
| | sftp-config.yaml
| | sftp-deployment-config.yaml
| | shells.yaml
| | shell_scripts.yaml
| | simple-xss.yaml
| | soap-defination-probing.yaml
| | solar-log-500.yaml
| | sonarqube-cred.yaml
| | sony-bravia-disclosure.yaml
| | spark-unauth.yaml
| | spidercontrol-scada-server-info.yaml
| | sqli-00.yaml
| | sqli-01.yaml
| | squid-analysis-report-generator.yaml
| | squid-detect.yaml
| | SquirrelMail.yaml
| | ssh-authorized-keys.yaml
| | ssh-known-hosts.yaml
| | ssrf-by-proxy.yaml
| | stats.yaml
| | svn-leak.yaml
| | swagger-xss.yaml
| | symfony-detect.yaml
| | tectuus-scada-monitor.yaml
| | telerik-derserial.yaml
| | template-injection.yaml
| | terraform-detect.yaml
| | tor-socks-proxy.yaml
| | tox-ini.yaml
| | unauthen-elastic.yaml
| | unauthen-kibana.yaml
| | upnp-device.yaml
| | ventrilo-config.yaml
| | vernemq-status.yaml
| | viewlinc-crlf-injection.yaml
| | vscode-sftp.yaml
| | web-config.yaml
| | werkzeug-debug.yaml
| | wordpress-accessible-wpconfig.yaml
| | wordpress-directory-listing.yaml
| | wordpress-misconfig.yaml
| | wordpress-rest-api.yaml
| | wordpress-user-enum.yaml
| | wp-ambience-xss.yaml
| | wp-church-admin-xss.yaml
| | wp-finder-xss.yaml
| | wp-knews-xss.yaml
| | wp-phpfreechat-xss.yaml
| | wp-securimage-xss.yaml
| | wp-socialfit-xss.yaml
| | ws-config.yaml
| | x-hacker.yaml
| | xmlrpc-pingback-ssrf.yaml
| | xss-fuzz.yaml
| | yii-debugger.yaml
| | zabbix-creds.yaml
| | zeroshell-kerbynet-lfd.yaml
| | zipkin-unauth.yaml
| | zwave2mqtt-health-check.yaml
| |
| +---poc2jar-WINDOWS
| | | poc2jar.jar
| | |
| | +---poc
| | | +---fanwei
| | | | fileread1.yml
| | | | fileread2.yml
| | | | sqlinject1.yml
| | | | WorkflowServiceXml.yml
| | | |
| | | +---hikvision
| | | | CVE-2017-7921.yml
| | | |
| | | +---turbocrm
| | | | fileread.yml
| | | | getshell.yml
| | | |
| | | \---wanhu
| | | frontgetshell.yml
| | |
| | +---property
| | | cmdlists.txt
| | | config.properties
| | | exetest.txt
| | | fernflower.jar
| | | keys.conf
| | | test.txt
| | |
| | \---pythonexp
| | | poc2jarpiliang.py
| | | poc2jarpiliangyml.py
| | | url.txt
| | | vuln.txt
| | |
| | +---Spring
| | | CVE-2022-22947_POC_EXP.py
| | | CVE-2022-22965_POC_EXP.py
| | | Spring-Cloud-Function-SpEL-POC.py
| | |
| | +---Struts2
| | | CVE_2021_31805_POC_EXP.py
| | |
| | +---sunflower
| | | en_sunflower_RCE_EXP.py
| | |
| | \---weaver
| | weaverOA_sql_injection_POC_EXP.py
| |
| +---redis-rogue-server
| | | exp.so
| | | LICENSE
| | | redis-rogue-server.bat
| | | redis-rogue-server.py
| | | redis-rogue-server1.bat
| | |
| | \---RedisModulesSDK
| | | Makefile
| | | redismodule.h
| | |
| | +---exp
| | | exp.c
| | | Makefile
| |
| +---RequestTemplate
| | App.bat
| | App.exe
| | App_darwin
| | App_linux
| | config.json
| | data.db
| | output1658770046.txt
| | output1661025983.txt
| | RequestTemplate.bat
| | RequestTemplate.jar
| |
| +---shiro
| | | config.properties
| | | Shiro-550-with-NoCC.jar
| | | ShiroExp.jar
| | | ShiroExploit-v2.3.jar
| | | ShiroExploit.jar
| | | ShiroScan-1.1.jar
| | | Shiro反序列化数据包解密及蓝队分析工具.jar
| | |
| | +---ShiroExploit.V2.51
| | | | ShiroExploit.jar
| | | | ysoserial.jar
| | | |
| | | \---config
| | | config.properties
| | | keys.conf
| | | keys.conf.big
| | | shell.jsp
| | |
| | +---shiro_attack2
| | | | shiro_attack-4.5.3-SNAPSHOT-all.jar
| | | |
| | | \---data
| | | shiro_keys.txt
| | |
| | \---shiro_attack_2.2
| | | shiro_attack-2.2.jar
| | |
| | \---data
| | shiro_keys.txt
| |
| +---spring
| | SpringBootExploit-1.3-SNAPSHOT-all.jar
| |
| +---struts2
| | K8_Struts2_EXP.exe
| | struts2_19.jar
| | Struts2_Test17_6.jar
| | Struts2漏洞检查工具2019版_V2.3.exe
| | Struts_2_全版本漏洞检测工具_18.09_过waf版.jar
| |
| +---Thelostworld_OA
| | cXDQEmI1.zip
| | cXDQEmI2.zip
| | Thelostworld_OA.jar
| |
| +---thinkphp
| | config.properties
| | ThinkLog-1.0-SNAPSHOT.jar
| | ThinkPHP.v1.2_Beta.exe
| | ThinkPHP.V2.3.by.jar
| | ThinkphpGUI 2020HackingClub线下典藏版.exe
| | ThinkphpGUI-1.2-SNAPSHOT.jar
| | Thinkphp全网GUI圈子社区专版.exe
| | thinkphp命令执行检测工具.jar
| |
| +---tomcat
| | password.txt
| | tomcat.jar
| | username.txt
| |
| +---WebCrack-master
| | | .gitignore
| | | requirements.txt
| | | url.txt
| | | webcrack.bat
| | | webcrack.py
| | | webcrack1.bat
| |
| +---weblogic
| | | JAVA反序列化漏洞利用工具-WebLogic.jar
| | | Java反序列化漏洞利用工具V1.7.jar
| | | Java反序列化终极测试工具.jar
| | | weblogic-framework.jar
| | | weblogic_exploit-1.0-SNAPSHOT-all.jar
| | |
| | \---weblogic-framework-0.2.3
| | | com.bea.javascript.jar
| | | marshalsec-0.0.3-SNAPSHOT-all.jar
| | | weblogic-framework-0.2.3-all-jar-with-dependencies.jar
| | | weblogic-framework.pdf
| | |
| | +---lib
| | | +---10.3.6.0
| | | | com.bea.core.repackaged.apache.commons.logging.jar
| | | | com.bea.core.repackaged.springframework.spring.jar
| | | |
| | | +---12.1.3.0
| | | | coherence.jar
| | | |
| | | +---12.2.1.0
| | | | coherence.jar
| | | | com.bea.core.repackaged.apache.commons.logging.jar
| | | | com.bea.core.repackaged.springframework.spring.jar
| | | |
| | | +---12.2.1.2.0
| | | | coherence.jar
| | | | com.bea.core.repackaged.apache.commons.logging.jar
| | | | com.bea.core.repackaged.springframework.spring.jar
| | | |
| | | +---12.2.1.3.0
| | | | coherence.jar
| | | | com.bea.core.repackaged.apache.commons.logging.jar
| | | | com.bea.core.repackaged.springframework.spring.jar
| | | |
| | | \---12.2.1.4.0
| | | coherence.jar
| | |
| | \---poc
| | PocServerClusterMasterRemote.class
| | PocServerRemoteChannelService.class
| | PocServerRemoteLeasingBasis.class
| | PocServerRemoteMigratableServiceCoordinator.class
| | PocServerSingletonMonitorRemote.class
| | PocServerSubCoordinatorRM.class
| |
| +---XSStrike-master
| | | .gitignore
| | | .travis.yml
| | | LICENSE
| | | requirements.txt
| | | xsstrike.bat
| | | xsstrike.py
| | |
| | +---.github
| | | |
| | | \---ISSUE_TEMPLATE
| | |
| | +---core
| | | | arjun.py
| | | | checker.py
| | | | colors.py
| | | | config.py
| | | | dom.py
| | | | encoders.py
| | | | filterChecker.py
| | | | fuzzer.py
| | | | generator.py
| | | | htmlParser.py
| | | | jsContexter.py
| | | | log.py
| | | | photon.py
| | | | prompt.py
| | | | requester.py
| | | | updater.py
| | | | utils.py
| | | | wafDetector.py
| | | | zetanize.py
| | |
| | +---db
| | | definitions.json
| | | wafSignatures.json
| | |
| | +---modes
| | | | bruteforcer.py
| | | | crawl.py
| | | | scan.py
| | | | singleFuzz.py
| |
| +---yongyou
| | yongyou.bat
| | yync.exe
| |
| \---zhiyuan
| zhiyuan.jar
| zyoa.bat
| zyoa.jar
| zyoa1.bat
| 致远OA漏洞全版本扫描工具GUI版.bat
|
+---gui_shouji
| | 2022-06-25-05-48-57.mv.db
| | 2022-08-20-10-03-55.mv.db
| | 2022-08-20-10-05-43.mv.db
| | 2022-08-20-10-10-06.mv.db
| | webfinder-next.jar
| |
| +---dirscan_3.0
| | | run.bat
| | | scandir-3.0.jar
| | |
| | \---dict
| | 1.pack.txt
| | 10.cgi.txt
| | 2.dir.txt
| | 3.asp.txt
| | 4.aspx.txt
| | 5.php.txt
| | 6.jsp.txt
| | 8.py.txt
| | 9.cfm.txt
| | asp.txt
| | aspx.txt
| | dir.txt
| | jsp.txt
| | loudong-SEC.txt
| | MDB.txt
| | php.txt
| | php字典.txt
| | z.txt
| | 全部.txt
| | 编辑器.txt
| |
| +---fofaviewer
| | config.properties
| | fofaviewer.jar
| | rules.db
| |
| +---goon
| | conf.yml
| | goon.bat
| | goon1.bat
| | goon3_win_amd64.exe
| |
| +---Layer子域名挖掘机5.0
| | ARSoft.Tools.Net.dll
| | ARSoft.Tools.Net.xml
| | BouncyCastle.Crypto.dll
| | dic.txt
| | dic1.txt
| | Layer.exe
| | 子域名.txt
| |
| +---leiying
| | |
| | \---SnowShadow_v1.0
| | | SnowShadow.bat
| | | SnowShadow.exe
| |
| +---subdomain
| | subdomain.bat
| | subdomain.py
| | subdomain1.bat
| | subnames_big.txt
| |
| +---TideFinger-master
| | |
| | +---666
| | | |
| | | \---python2
| | | cms_finger.db
| | | count_file_md5.py
| | |
| | \---TideFinger-master
| | | cms_finger.db
| | | requirements.txt
| | | technologies.json
| | | TideFinger-master.bat
| | | TideFinger-master1.bat
| | | TideFinger.py
| | | url.txt
| | | Wappalyzer.py
| | |
| | +---webanalyzer
| | | | cli.py
| | | | condition.py
| | | | utils.py
| | | | webanalyzer.py
| | | |
| | | +---rules
| | | \---__pycache__
| | | condition.cpython-310.pyc
| | | utils.cpython-310.pyc
| | | webanalyzer.cpython-310.pyc
| | |
| | \---__pycache__
| | Wappalyzer.cpython-310.pyc
| |
| \---yjdirscanv1.1
| | readme.txt
| | yjdirscan.exe
| | 御剑目录扫描专业版v1.1.exe
| |
| \---files
| asp.txt
| aspx.txt
| bak.txt
| dir.txt
| jsp.txt
| mdb.txt
| php.txt
| Set.ini
| test.txt
| UserAgent.ini
| UserAgent.list
| 御剑去重字典.zip
|
+---gui_webshell
| | GBByPass.jar
| | new.aspx
| | Webshell_Generate-1.0.jar
| |
| +---AntSword
| | | ant_hex.php
| | | hack.php
| | |
| | +---AntSword-Loader-v4.0.3-win32-x64
| | | | AntSword.exe
| +---Behinder
| | | Behinder.jar
| | | data.db
| | | start.bat
| | | 更新日志.txt
| | |
| | \---server
| | 360.php
| | shell.asp
| | shell.aspx
| | shell.jsp
| | shell.jspx.jsp
| | shell.php
| | shell_java9.jsp
| |
| +---Behinder-Mode
| | | Behinder-Mode.jar
| | | data.db
| | |
| | +---profiles
| | | 401.profile
| | | 403.profile
| | | 404.profile
| | | 500.profile
| | | bt.profile
| | | github.profile
| | | google.profile
| | |
| | \---server
| | | shell.aspx
| | | shell.jsp
| | | shell.jspx
| | | shell.php
| | | shell_java9.jsp
| | |
| | \---cofuse
| | shell.jsp
| | shell.jspx
| | shell_java9.jsp
| | shell_new.php
| |
| +---Behinder4
| | Behinder.jar
| | data.db
| | 更新日志.txt
| |
| +---Godzilla
| | | data.db
| | | Godzilla.jar
| | |
| | \---GodzillaCache
| | cache.db
| |
| \---TianXie
| | 使用手册0.1.docx
| | 天蝎权限管理工具.jar
| | 更新说明.txt
| | 服务端脚本说明.txt
| \---Tools
| +---demo
| | | beer.py
| | | eiffel.py
| | | hanoi.py
| | | life.py
| | | markov.py
| | | mcast.py
| | | queens.py
| | | redemo.py
| | | rpython.py
| | | rpythond.py
| | | sortvisu.py
| | | ss1.py
| | | vector.py工具下载地址:
云中转网盘:
yunzhongzhuan.com/#sharefile=fQVEGHV5_75391
解压密码:www.ddosi.org
作者公众号下载:
https://mp.weixin.qq.com/s/NiW-5LpvTqVlkL8tuUV6HQ
转载请注明出处及链接


就是那个一把梭出现了回溯(最近一次调用最后):
文件“Serein.py”,第 4 行,在
进口商谈
ModuleNotFoundError: 没有名为 ‘shodan 的模块