目录导航
用于检查漏洞CVE-2021-21972的Nmap脚本-vCenter Server RCE
使用方法
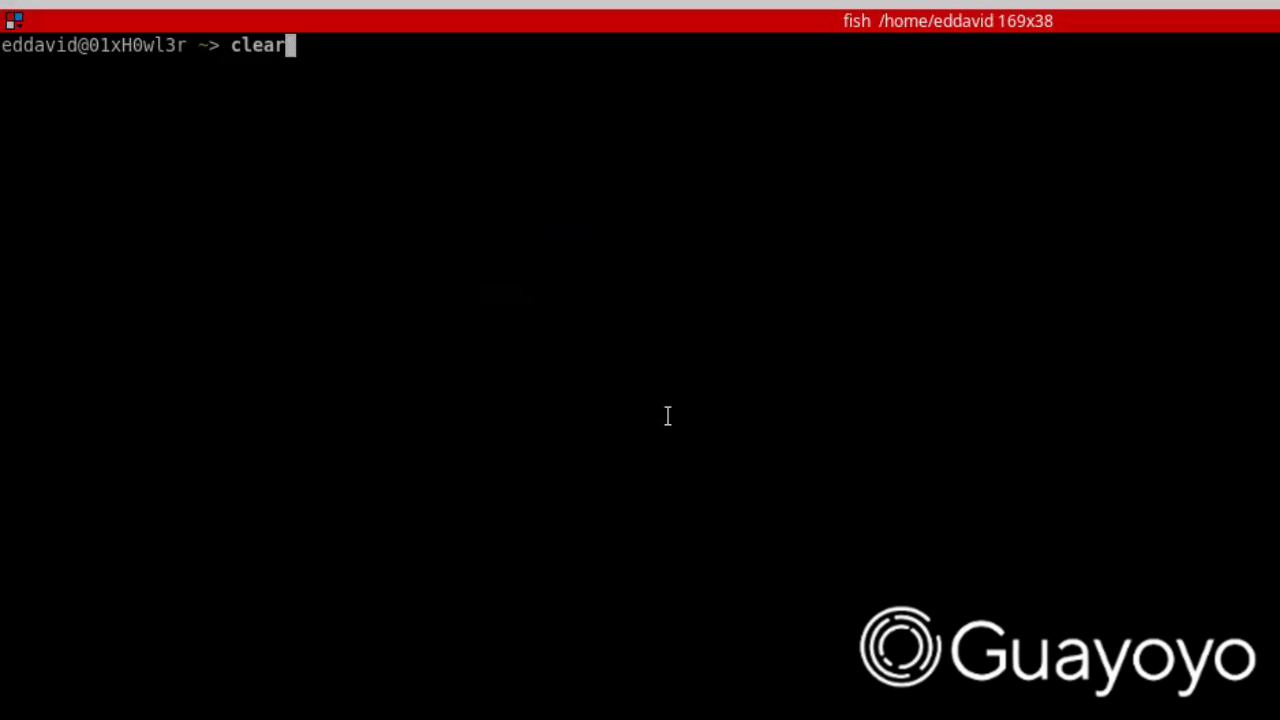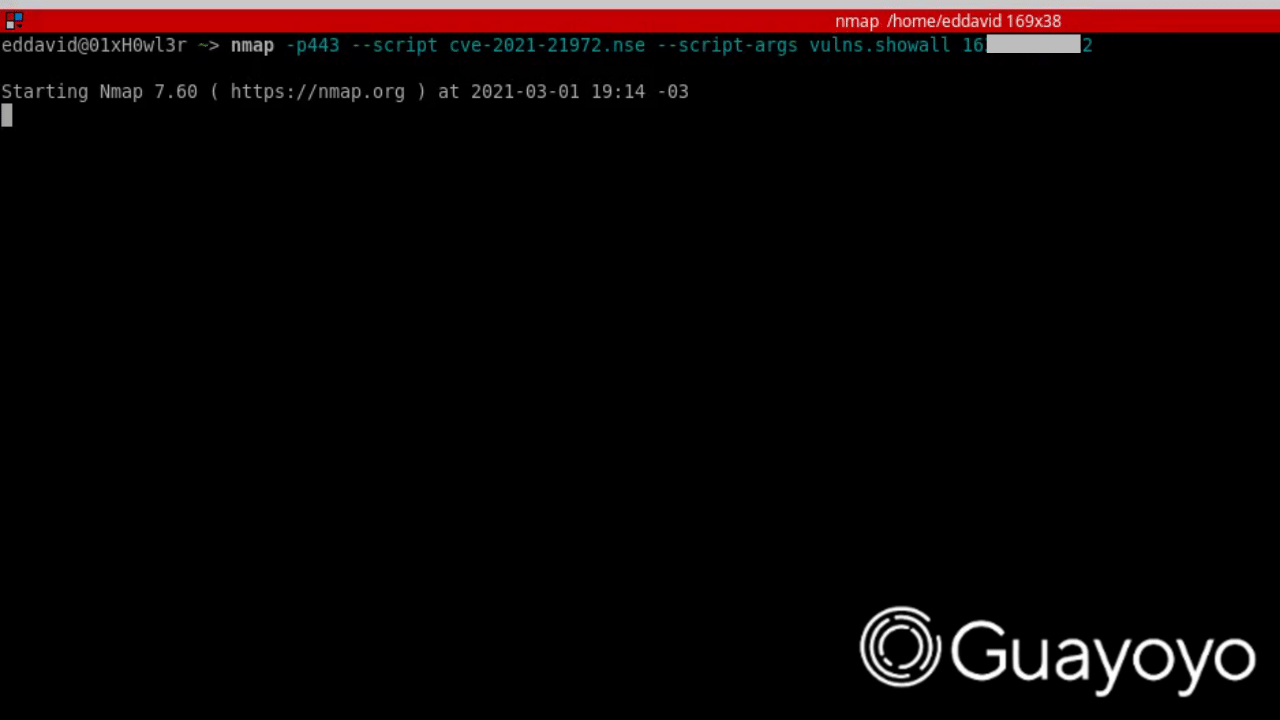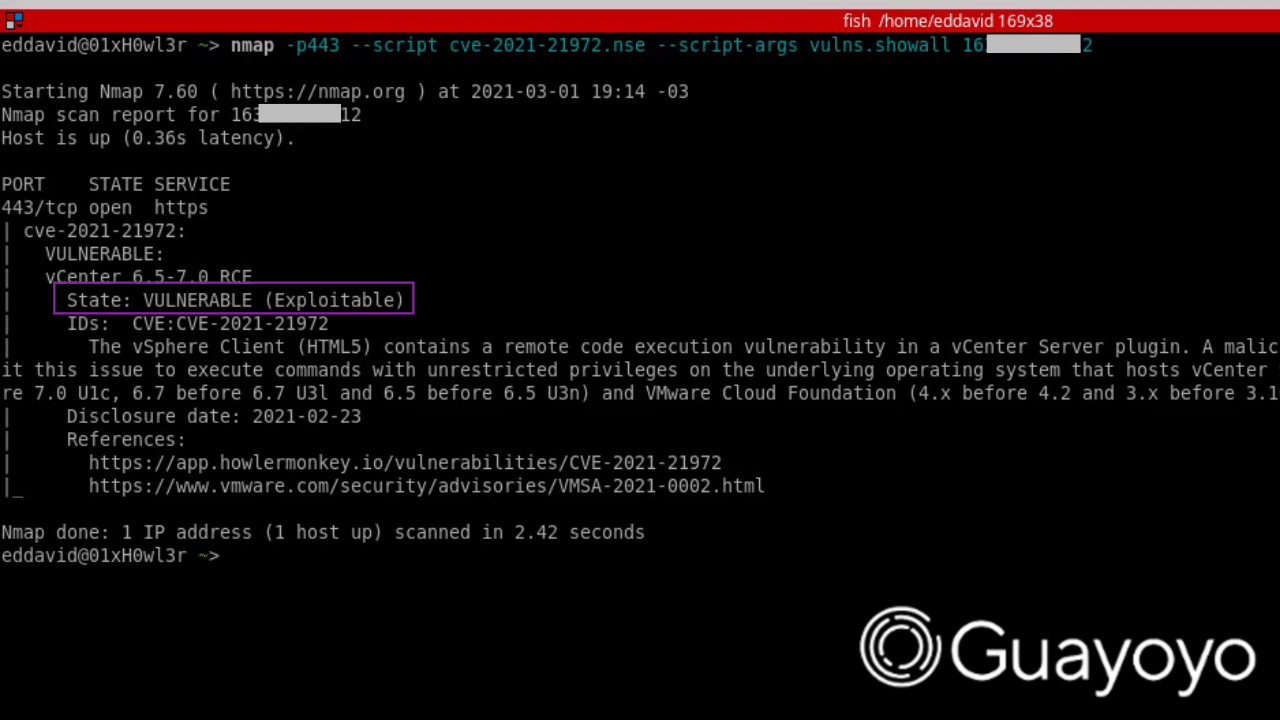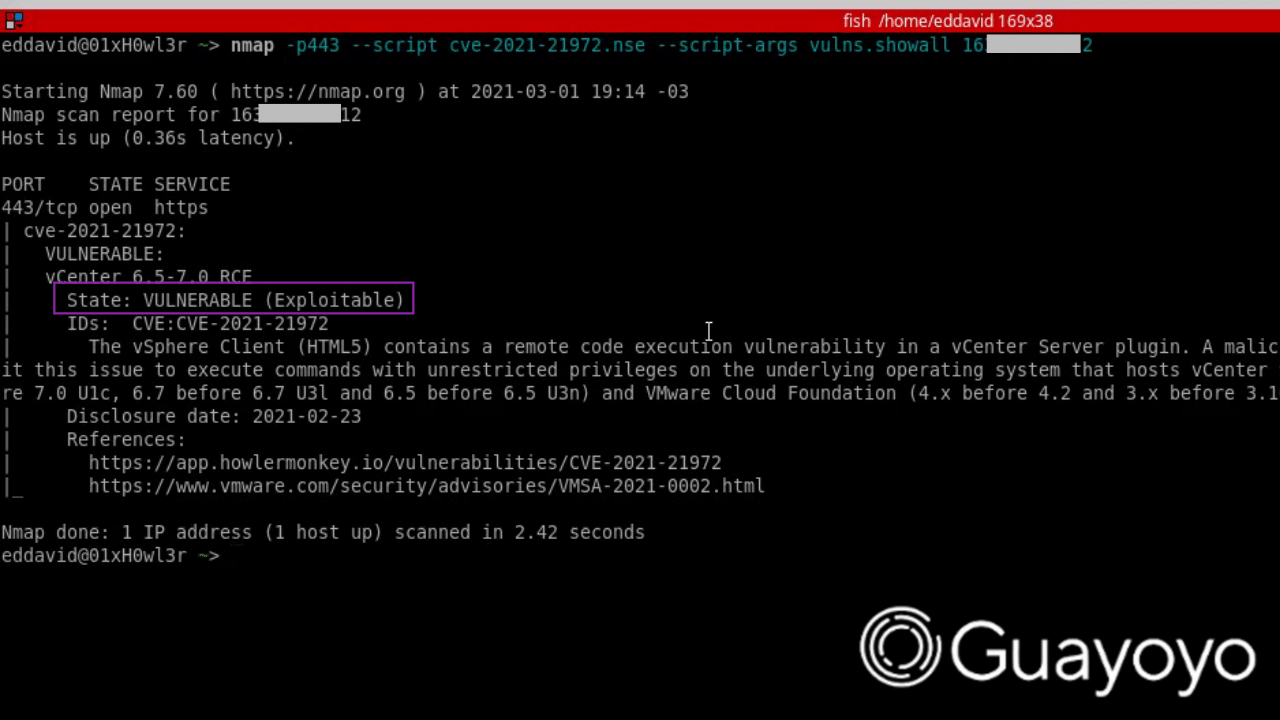
nmap -p443 --script cve-2021-21972.nse --script-args vulns.showall IP
cve-2021-21972.nse下载地址
GitHub: cve-2021-21972.nse
雨苁网盘: w.ddosi.workers.dev
解压密码: www.ddosi.org
cve-2021-21972.nse文件内容:
description = [[
VMware vCenter Server CVE-2021-21972 RCE Vulnerability - Check
Este script de Nmap busca verificar la vulnerabilidad CVE-2021-21972 en la siguiente ruta
"/ui/vropspluginui/rest/services/uploadova" mediante una solicitud POST e interpretando la
respuesta HTTP 500 si se encuentra la palabra "uploadFile", eso significa que vCenter está
disponible para aceptar archivos vía POST sin restricciones
Este script está basado en el script original de Alex Hernandez aka alt3kx (https://github.com/alt3kx/CVE-2021-21972)
References:
https://app.howlermonkey.io/vulnerabilities/CVE-2021-21972
https://www.vmware.com/security/advisories/VMSA-2021-0002.html
]]
---
-- @usage
-- nmap -p443 --script CVE-2021-21972.nse <target>
-- @output
-- PORT STATE SERVICE
-- 443/tcp open https
-- | CVE-2021-21972:
-- | VULNERABLE:
-- | vCenter 6.5-7.0 RCE
-- | State: VULNERABLE (Exploitable)
-- | IDs: CVE:CVE-2021-21972
-- | Risk factor: HIGH CVSS: 9.8
-- | The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin.
-- | A malicious actor with network access to port 443 may exploit this issue to execute commands with
-- | unrestricted privileges on the underlying operating system that hosts vCenter Server. This affects
-- | VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and VMware
-- | Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2).
-- | Disclosure date: 2021-02-23
-- | References:
-- | https://app.howlermonkey.io/vulnerabilities/CVE-2021-21972
-- |_ https://www.vmware.com/security/advisories/VMSA-2021-0002.html
author= "Edgar Salazar <[email protected]>"
license = "Same as Nmap--See http://nmap.org/book/man-legal.html"
categories = {"vuln", "exploit"}
local shortport = require "shortport"
local http = require "http"
local stdnse = require "stdnse"
local string = require "string"
local vulns = require "vulns"
portrule = shortport.http
action = function(host, port)
local vuln = {
title = "vCenter 6.5-7.0 RCE",
state = vulns.STATE.NOT_VULN,
risk_factor = "HIGH",
scores = {
CVSS = "9.8",
},
IDS = { CVE = 'CVE-2021-21972' },
description = [[
The vSphere Client (HTML5) contains a remote code execution vulnerability in a vCenter Server plugin.
A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted
privileges on the underlying operating system that hosts vCenter Server.
This affects VMware vCenter Server (7.x before 7.0 U1c, 6.7 before 6.7 U3l and 6.5 before 6.5 U3n) and
VMware Cloud Foundation (4.x before 4.2 and 3.x before 3.10.1.2).
]],
references = {
'https://app.howlermonkey.io/vulnerabilities/CVE-2021-21972',
'https://www.vmware.com/security/advisories/VMSA-2021-0002.html'
},
dates = {
disclosure = {year = '2021', month = '02', day = '23'},
},
}
local report = vulns.Report:new(SCRIPT_NAME, host, port)
local uri = "/ui/vropspluginui/rest/services/uploadova"
local options = {header={}}
options['header']['User-Agent'] = "Guayoyo - Mozilla/5.0 (compatible; vCenter)"
vuln.state = vulns.STATE.NOT_VULN
local response = http.post(host, port, uri)
if ( response.status == 500 ) then
local title = string.match(response.body, "uploadFile")
if (title == "uploadFile") then
vuln.state = vulns.STATE.EXPLOIT
end
else
uri = "/ui/vropspluginui/rest/services/getstatus"
options = {header={}}
options['header']['User-Agent'] = "Guayoyo - Mozilla/5.0 (compatible; vCenter)"
response = http.get(host, port, uri)
if ( response.status == 200 and string.find(response.body, "States") ) then
vuln.state = vulns.STATE.LIKELY_VULN
end
end
return report:make_output (vuln)
end

