目录导航
不了解Burp Bounty的参考如下文章:
昨天发的是Burp Bounty pro,相当于一个扫描器框架,今天发的相当于payloads或者说exp/poc.
Burp Bounty pro只有配合配置文件+规则库才有用.
Burp Bounty规则库列表
├─profiles
│ AccessToken.bb
│ Action_parameters.bb
│ Amazon_AWS_Url.bb
│ Api_path.bb
│ Artica_Web.bb
│ Artica_Web_Proxy_Auth_Bypass_CVE-2020-17506.bb
│ Artica_Web_Request.bb
│ Atlassian_Crowd_RCE_CVE-2019-11580.bb
│ Authorization_Bearer.bb
│ AWS_Access_Key_ID.bb
│ AWS_Region.bb
│ Azure_Blob_Discovered.bb
│ Basic_Auth_Credentials.bb
│ Bitcoin_Address.bb
│ Blind_RCE_Linux.bb
│ Blind_RCE_Windows.bb
│ Blind_XSS_append.bb
│ Blind_XSS_replace.bb
│ Blind_XXE.bb
│ CDN_Detected.bb
│ Cisco_ASA_Device_Found.bb
│ Cisco_ASA_LFI-CVE-2020-3452.bb
│ Cisco_Request_Detected.bb
│ Cisco_Wan_VPN_disclosure-CVE-2019-1653.bb
│ Citrix_ADC_Directory_Traversal_CVE-2019-19781.bb
│ Citrix_Detection.bb
│ Citrix_ShareFile_File_Read_CVE-2020-8982.bb
│ Citrix_XenMobile_PathTraversal.bb
│ CMS_Found.bb
│ CORS Misconfiguration.bb
│ CouchDB_Admin_Exposure.bb
│ CouchDB_Request.bb
│ CouchDB_Response.bb
│ CRLF_append.bb
│ CRLF_replace.bb
│ Debug Pages.bb
│ Debug_Logic_Parameters.bb
│ Debug_variables.bb
│ DigitalOcean_Space_Discovered.bb
│ Docker_API_Response.bb
│ DomainTakeOver_Strings.bb
│ Drupal_Response.bb
│ Drupal_User_Enum.bb
│ Drupal_User_Enum_Redirect.bb
│ easy_wp_smtp_listing_enabled.bb
│ Echo_RCE_append.bb
│ Echo_RCE_replace.bb
│ EndpointsExtractor.bb
│ Expect_RCE.bb
│ F5-BigIP_CVE-2020-5902.bb
│ File_Manager_Wordpress_Backups_CVE-2020-24312.bb
│ Firebase DB detected.bb
│ Fortinet_Panel.bb
│ Fortinet_Request.bb
│ FortiOS_Creds_Disclosure_CVE-2018-13379.bb
│ Fuzzing_directories.bb
│ GCP_Service_Account.bb
│ GCP_Urls.bb
│ GitFinder.bb
│ Gmail_Oauth_2.0.bb
│ Google_Cloud_Buckets.bb
│ GraphQL_Endpoint.bb
│ Hidden Parameters.bb
│ Host_Header_Injection.bb
│ IDOR_parameters.bb
│ Interesting_Keyworks.bb
│ Java_De-Serialization.bb
│ Jenkins_Response.bb
│ Jira_Info_Exposure_CVE-2020-14179.bb
│ Jira_Path_Traversal_CVE-2019-8442.bb
│ Jira_Request.bb
│ Jira_SSRF_CVE-2017-9506.bb
│ Jira_unauthenticated_Info.bb
│ JIRA_Unauthenticated_Sensitive_Info_CVE-2019-8449.bb
│ Jira_User_Enum_CVE-2020-14181.bb
│ Joomla detection.bb
│ JS_Variables.bb
│ Keys.bb
│ Key_Parameters.bb
│ Kubernetes_API_Exposed.bb
│ Kubernetes_Response.bb
│ LFI_RFI_Parameters.bb
│ MAC_Address.bb
│ MAGMI_Request.bb
│ MAGMI_Response.bb
│ MAMGI_Auth_Bypass_CVE-2020-5777.bb
│ Netsweeper_code_injection_CVE-2020-13167.bb
│ Netsweeper_Request.bb
│ Netsweeper_Response.bb
│ NoSQL_Session_Token.bb
│ OAuth_parameters.bb
│ Open Firebase Database.bb
│ OpenRedirect-ParameterPollution.bb
│ OpenRedirect-ParameterPollution_Path.bb
│ OpenRedirect.bb
│ OpenRedirect_SSRF_Collaborator.bb
│ OpenRedirect_SSRF_Collaborator_HTTP0_9.bb
│ OpenRedirect_SSRF_Collaborator_HTTP1_0.bb
│ OpenRedirect_SSRF_Parameters.bb
│ OpenRedirect_to_Account_Takeover.bb
│ Openredirect_to_XSS.bb
│ Oracle_WebLogic_RCE_CVE-2020-2551.bb
│ Outlook_Team.bb
│ PathTraversal_Linux.bb
│ PathTraversal_Windows.bb
│ Path_Traversal_Spring_Cloud_CVE-2020-5410.bb
│ PHP_RCE.bb
│ Private_SSH_Key.bb
│ Pulse_Secure_CVE-2019-11510.bb
│ RCE_Linux.bb
│ RCE_Parameters.bb
│ RCE_Windows.bb
│ Reflected_values_greater_than_three_characters.bb
│ RegisterUser_parameters.bb
│ Ruby on Rails CVE-2019-5418 - WAF bypass.bb
│ Ruby on Rails CVE-2019-5418.bb
│ Secret-keywords-SecLists.bb
│ Secrets_Request.bb
│ Software_Version.bb
│ solarwinds_default_admin.bb
│ Solarwinds_Orion_Request.bb
│ Solarwinds_Orion_Response.bb
│ Source_code.bb
│ Spring Boot Actuators.bb
│ Springboot_Requests.bb
│ Spring_Cloud_Netflix_SSRF-CVE-2020-5412.bb
│ Spring_Cloud_Path_Traversal_CVE-2019-3799.bb
│ Spring_MVC_Path_Traversal_CVE-2018-1271.bb
│ SQLi.bb
│ SQLi_Collaborator.bb
│ SQLi_Parameters.bb
│ SQLi_TimeBased_append.bb
│ SQLi_TimeBased_replace.bb
│ SQL_Message_Detected.bb
│ SSRF-Collaborator.bb
│ SSRF-URLScheme.bb
│ SSRF_Collaborator_HTTP0_9.bb
│ SSRF_Collaborator_HTTP1_0.bb
│ SSTI.bb
│ SSTI_Parameters.bb
│ Subdomain_takeover.bb
│ SVNFinder.bb
│ Swagger-Finder.bb
│ Swagger_found.bb
│ Swagger_Request.bb
│ Symfony_Debug.bb
│ Symfony_Response.bb
│ tags.txt
│ Test_XSS_append.bb
│ Test_XSS_append_encoded.bb
│ Test_XSS_GET_POST.bb
│ Token_Parameters.bb
│ Tomcat_Groovy_CVE-2020-9484.bb
│ Tomcat_Response_Detection.bb
│ Traefik_Open_Redirect-CVE-2020-15129.bb
│ Traefik_Response.bb
│ URL_as_a_Value.bb
│ URL_Path_as_a_Value.bb
│ UserEnum_parameters.bb
│ UUID_Request.bb
│ vBulletin_Response.bb
│ WAF_Found.bb
│ WebCachePoisoning.bb
│ Weblogic_Request.bb
│ Woody_Wordpress_RCE.bb
│ WordPress detection.bb
│ WordPress_Config_Accessible.bb
│ WordPress_directory_listing.bb
│ WordPress_Duplicator_Plugin_LFI_CVE-2020-11738.bb
│ WordPress_JSmol2WP_SSRF.bb
│ WordPress_Path_Traversal.bb
│ wordpress_users_enum_yoastseo.bb
│ WordPress_user_enum_json.bb
│ WordPress_user_enum_oembed.bb
│ WP_Config.bb
│ X-Headers-Collaborator.bb
│ XSS.bb
│ XSS_CVE-2020-14815.bb
│ XSS_HtmlUrlEncode.bb
│ XSS_Parameters.bb
│ XSS_UrlEncode.bb
│ XXE_Linux.bb
│ XXE_Windows.bb
│
└─rules
rule_Artica_Web_Proxy_Auth_bypass.bb
rule_Cisco_Rule.bb
rule_Citrix_Rule.bb
rule_CouchDB_Admin_Exposure.bb
rule_Drupal_Rule.bb
rule_Firebase Database Rule.bb
rule_Fortinet_Fortigate.bb
rule_Jira_Rule.bb
rule_Kubernetes_Rule.bb
rule_LFI_Rule.bb
rule_MAGMI_Remote_Auth.bb
rule_Netsweeper_CodeInjection.bb
rule_OpenRedirect_SSRF_Rule.bb
rule_RCE_Rule.bb
rule_Solarwinds.bb
rule_SpringBoot_Rule.bb
rule_SQLi_Rule.bb
rule_SSTI_Rule.bb
rule_Symfony_Rule.bb
rule_Traefik_Rule.bb
rule_Weblogic_Rule.bb
rule_Wordpress_Rule.bb
rule_XSS_rule.bbprofiles+rules 下载地址
https://yzzpan.com/#sharefile=q5vJOaYo_32433
解压密码:www.ddosi.org
正确使用方法
①下载插件解压.
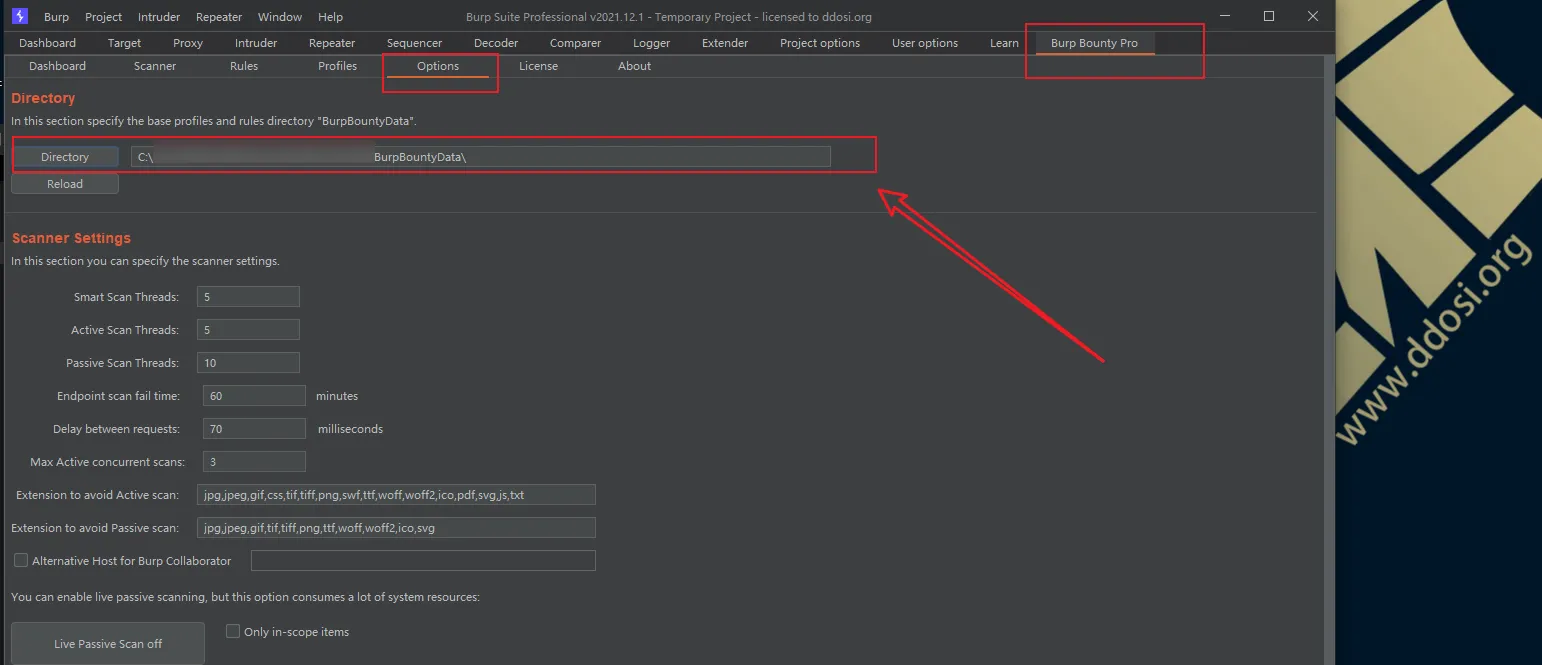
②打开如下选项选择你解压出来的profiles+rules目录
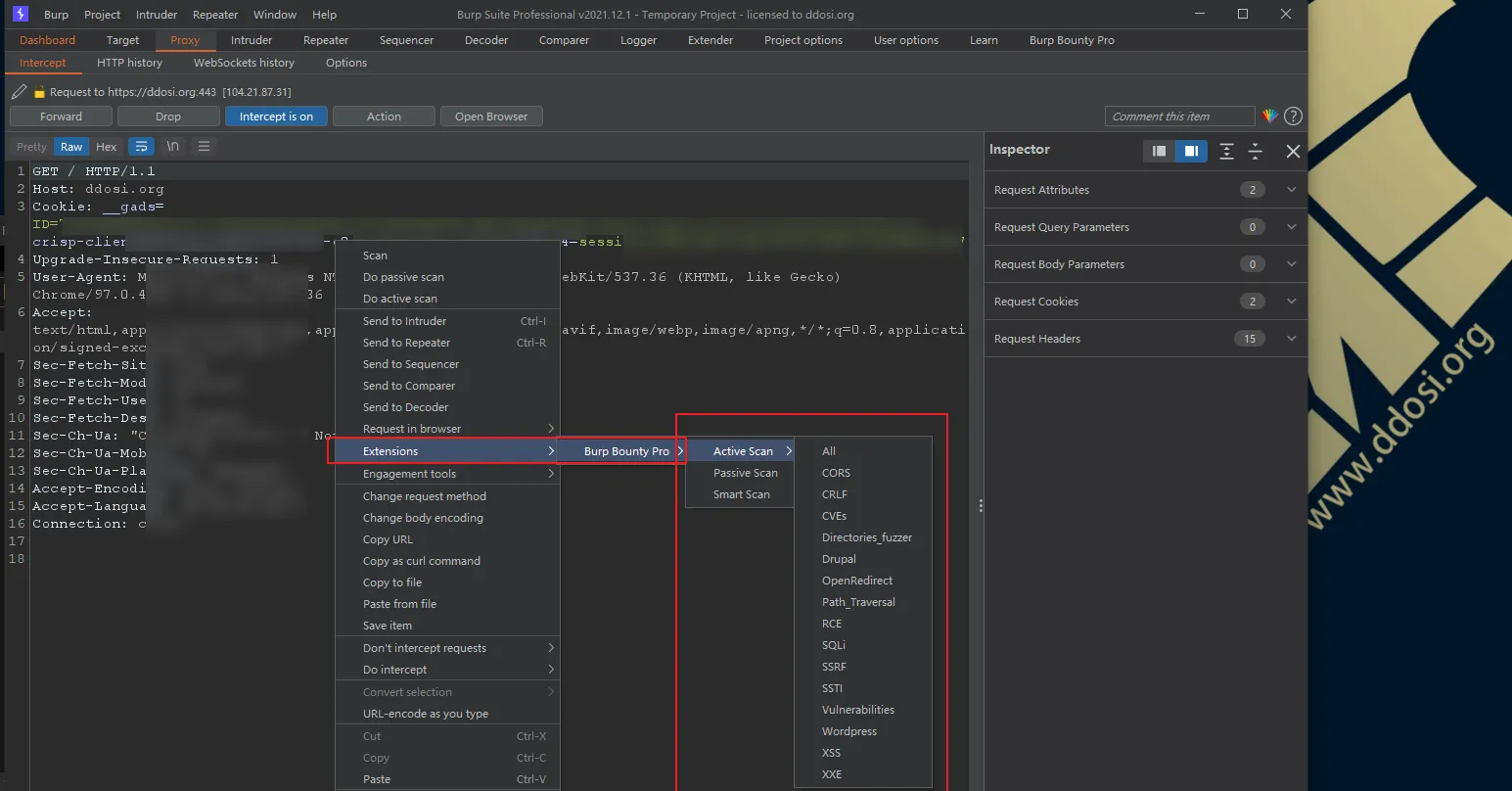
③在抓取到的流量页面右键选择此插件即可扫描
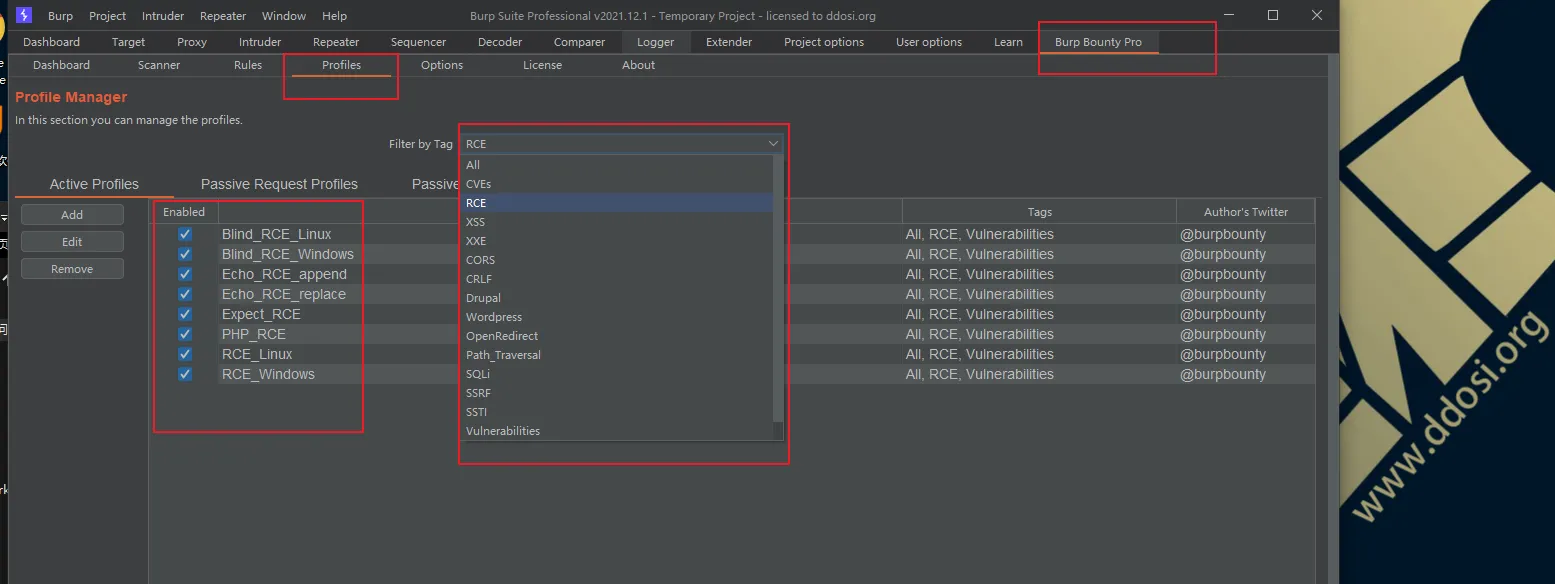
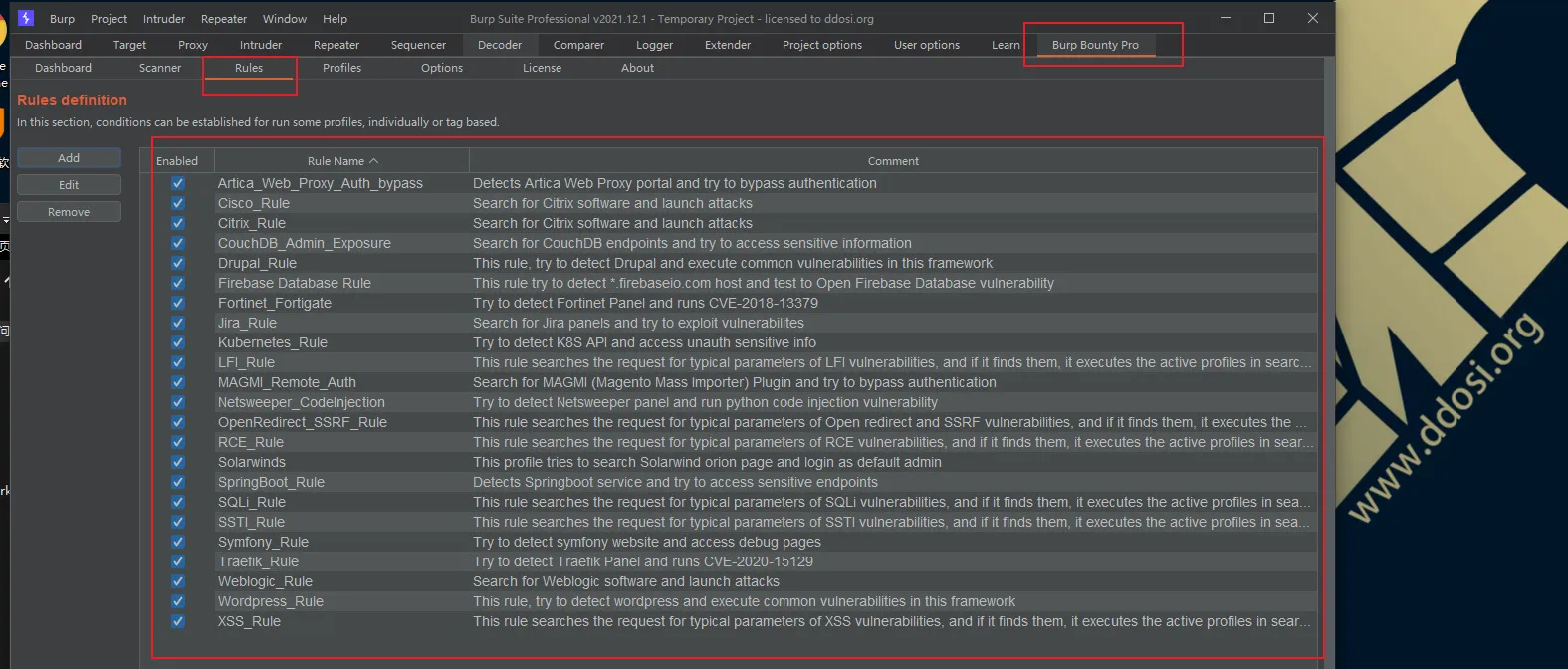
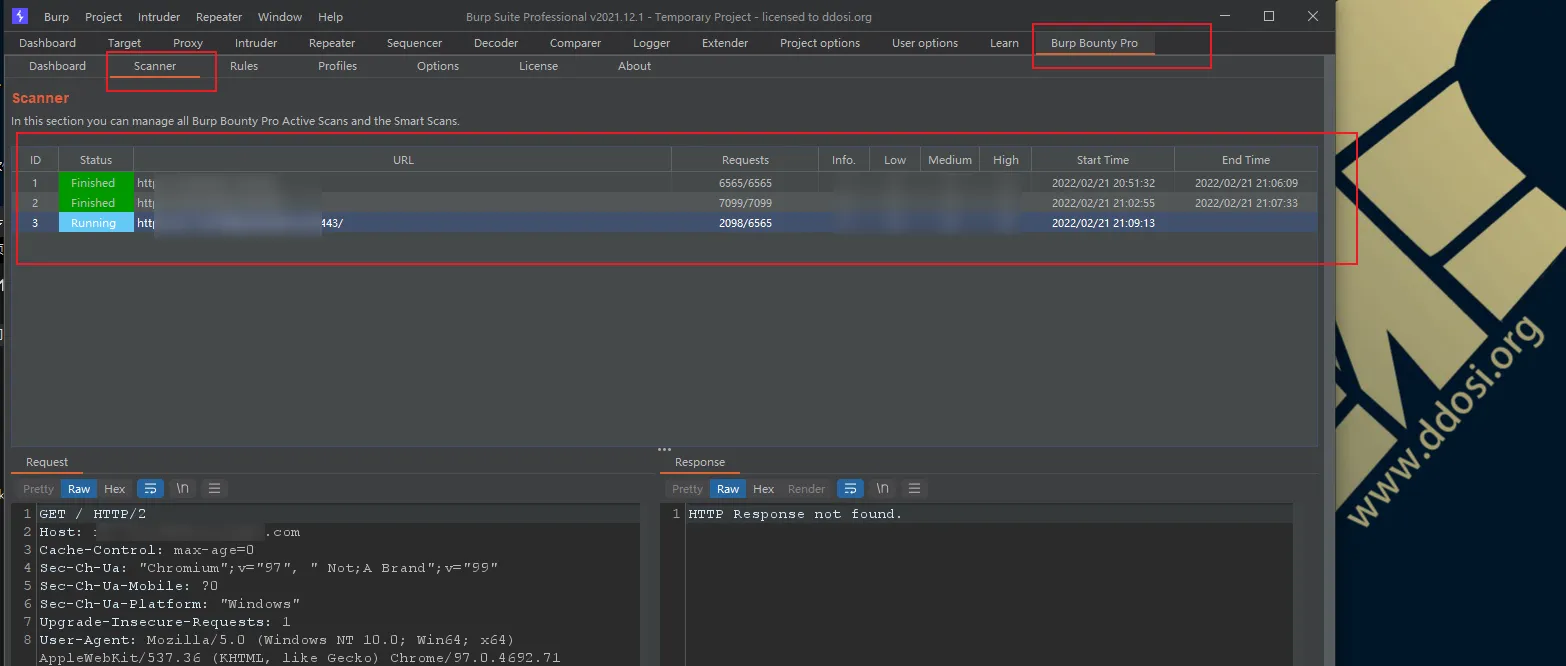
如果其他页面显示如图所示,则成功导入:
转载请注明出处及链接