目录导航
对Burp Bounty不了解的自行参考如下文章:
Burp Bounty Pro 2.4.2更新日志
Burp Bounty Pro 2.4.2 更新于 2022年5月4日
- 在Burp Suite Pro v2022.3中,由于安全原因,它已经禁用了Swing组件中的HTML渲染。我们修复了HTML代码。
- 添加了代理授权和凭据授权选项。
Burp Bounty Pro v2.4.2 Changelog
In Burp Suite Pro v2022.3 it has been disabled HTML rendering in Swing components for security reasons.We fixed our HTML code.
The license authentication through proxy and credentials option has been added.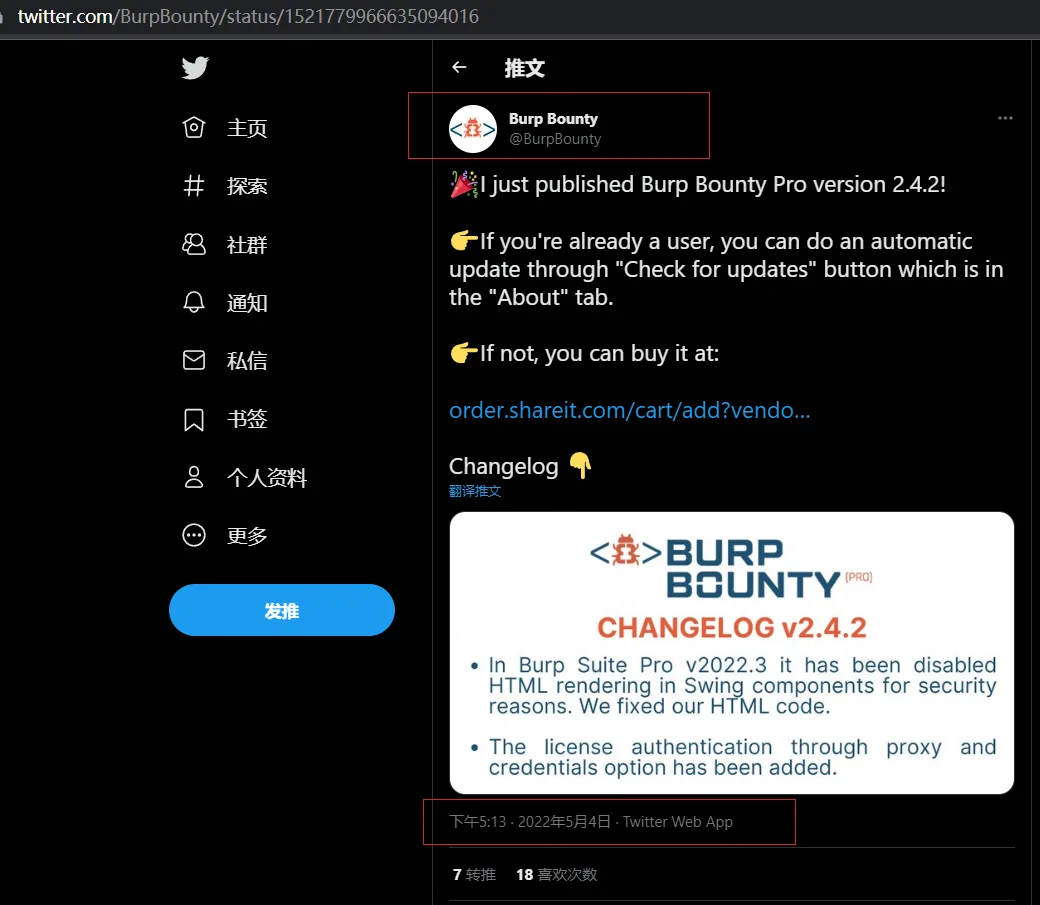
Burp Bounty Pro 2.4.2下载地址
https://www.yunzhongzhuan.com/#sharefile=p1FmWAeR_51416
解压密码:www.ddosi.org
压缩包包含的文件内容
包含一本指导手册:BurpBountyPro_2_documentation_v1.0.pdf
BurpBountyPro_v2.4.2_Cracked
│ BurpBountyPro_2_documentation_v1.0.pdf
│ BurpBountyPro_v2.4.2_Cracked.jar
│
└─BurpBountyData
│ version.txt
│
├─profiles
│ AccessToken.bb
│ Action_parameters.bb
│ Amazon_AWS_Url.bb
│ Api_path.bb
│ Artica_Web.bb
│ Artica_Web_Request.bb
│ Authorization_Bearer.bb
│ AWS_Access_Key_ID.bb
│ AWS_Region.bb
│ Azure_Blob_Discovered.bb
│ Basic_Auth_Credentials.bb
│ Bitcoin_Address.bb
│ Blind_RCE_Linux.bb
│ Blind_RCE_Linux_GETParams.bb
│ Blind_RCE_Linux_POSTParams.bb
│ Blind_RCE_Windows.bb
│ Blind_RCE_Windows_GETParams.bb
│ Blind_RCE_Windows_POSTParams.bb
│ Blind_XSS.bb
│ Blind_XSS_GETParams.bb
│ Blind_XSS_POSTParams.bb
│ Blind_XXE.bb
│ CDN_Detected.bb
│ Cisco_ASA_Device_Found.bb
│ Cisco_Request_Detected.bb
│ Citrix_Detection.bb
│ CMS_Found.bb
│ CORS Misconfiguration.bb
│ CouchDB_Admin_Exposure.bb
│ CouchDB_Request.bb
│ CouchDB_Response.bb
│ CRLF.bb
│ CRLF_GETParams.bb
│ CRLF_POSTParams.bb
│ CVE-2017-9506_Jira_SSRF.bb
│ CVE-2018-1271_Spring_MVC_Path_Traversal.bb
│ CVE-2018-13379_FortiOS_Creds_Disclosure.bb
│ CVE-2019-11510_Pulse_Secure.bb
│ CVE-2019-11580_Atlassian_Crowd_RCE.bb
│ CVE-2019-1653_Cisco_Wan_VPN_disclosure.bb
│ CVE-2019-19781_Citrix_ADC_Directory_Traversal.bb
│ CVE-2019-3799_Spring_Cloud_Path_Traversal.bb
│ CVE-2019-5418_Ruby on Rails - WAF bypass.bb
│ CVE-2019-5418_Ruby on Rails.bb
│ CVE-2019-8442_Jira_Path_Traversal.bb
│ CVE-2019-8449_Jira_Unauthenticated_Sensitive_Info.bb
│ CVE-2020-11738_Wordpress_Duplicator_Plugin_LFI.bb
│ CVE-2020-13167_Netsweeper_code_injection.bb
│ CVE-2020-13379_Grafana_SSRF.bb
│ CVE-2020-14179_Jira_Info_Exposure.bb
│ CVE-2020-14181_Jira_User_Enum.bb
│ CVE-2020-14815_XSS.bb
│ CVE-2020-15129_Traefik_Open_Redirect.bb
│ CVE-2020-17506_Artica_Web_Proxy_Auth_Bypass.bb
│ CVE-2020-24312_File_Manager_Wordpress_Backups.bb
│ CVE-2020-2551_Oracle_WebLogic.bb
│ CVE-2020-3452_Cisco_ASA_LFI.bb
│ CVE-2020-5410_Path_Traversal_Spring_Cloud.bb
│ CVE-2020-5412_Spring_Cloud_Netflix.bb
│ CVE-2020-5777_MAMGI_Auth_Bypass.bb
│ CVE-2020-5902_F5-BigIP.bb
│ CVE-2020-8209_Citrix_XenMobile_PathTraversal.bb
│ CVE-2020-8982_Citrix_ShareFile_File_Read.bb
│ CVE-2020-9484_Tomcat_Groovy.bb
│ CVE-2021-26086_PathTraversal_Atlassian_Jira.bb
│ CVE-2021-40438_Apache_mod_proxy_SSRF.bb
│ CVE-2021-40539_Zoho_ManageEngine_ADSelfService.bb
│ CVE-2021-43798_Grafana_LFI.bb
│ CVE-2021-44228_RCE_Log4j.bb
│ CVE-2021-44228_RCE_Log4j_GETPOST.bb
│ CVE-2021-44228_RCE_Log4j_urlEncode.bb
│ Debug Pages.bb
│ Debug_Logic_Parameters.bb
│ Debug_variables.bb
│ DigitalOcean_Space_Discovered.bb
│ Docker_API_Response.bb
│ DomainTakeOver_Strings.bb
│ Drupal_Response.bb
│ Drupal_User_Enum.bb
│ Drupal_User_Enum_Redirect.bb
│ easy_wp_smtp_listing_enabled.bb
│ Echo_RCE.bb
│ EndpointsExtractor.bb
│ Expect_RCE.bb
│ Firebase DB detected.bb
│ Fortinet_Panel.bb
│ Fortinet_Request.bb
│ Fuzzing_directories.bb
│ GCP_Service_Account.bb
│ GCP_Urls.bb
│ GitFinder.bb
│ Gmail_Oauth_2.0.bb
│ Google_Cloud_Buckets.bb
│ Graphql Introspection.bb
│ GraphQL_Endpoint.bb
│ Hidden Parameters.bb
│ Host_Header_Injection.bb
│ IDOR_parameters.bb
│ Interesting_Keyworks.bb
│ Java_De-Serialization.bb
│ Jenkins_Response.bb
│ Jira_Request.bb
│ Jira_unauthenticated_Info.bb
│ Joomla detection.bb
│ JS_Variables.bb
│ Keys.bb
│ Key_Parameters.bb
│ Kubernetes_API_Exposed.bb
│ Kubernetes_Response.bb
│ LFI_RFI_Parameters.bb
│ MAC_Address.bb
│ MAGMI_Request.bb
│ MAGMI_Response.bb
│ Netsweeper_Request.bb
│ Netsweeper_Response.bb
│ NoSQL_Session_Token.bb
│ OAuth_parameters.bb
│ Open Firebase Database.bb
│ OpenRedirect-ParameterPollution.bb
│ OpenRedirect-ParameterPollution_Path.bb
│ OpenRedirect.bb
│ OpenRedirect_GETParams.bb
│ OpenRedirect_POSTParams.bb
│ OpenRedirect_SSRF_Collaborator.bb
│ OpenRedirect_SSRF_Collaborator_GETParams.bb
│ OpenRedirect_SSRF_Collaborator_HTTP0_9.bb
│ OpenRedirect_SSRF_Collaborator_HTTP1_0.bb
│ OpenRedirect_SSRF_Collaborator_POSTParams.bb
│ OpenRedirect_SSRF_Parameters.bb
│ OpenRedirect_to_Account_Takeover.bb
│ Openredirect_to_XSS.bb
│ Outlook_Team.bb
│ Password-Reset-Headers.bb
│ Password-Reset-Params.bb
│ Password-Reset-URL.bb
│ PathTraversal_Linux.bb
│ PathTraversal_Linux_GETParams.bb
│ PathTraversal_Linux_POSTParams.bb
│ PathTraversal_Windows.bb
│ PathTraversal_Windows_GETParams.bb
│ PathTraversal_Windows_POSTParams.bb
│ PHP_RCE.bb
│ PHP_RCE_GETParams.bb
│ PHP_RCE_POSTParams.bb
│ Private_SSH_Key.bb
│ RCE_Linux.bb
│ RCE_Linux_GETParams.bb
│ RCE_Linux_POSTParams.bb
│ RCE_Parameters.bb
│ RCE_Windows.bb
│ RCE_Windows_GETParams.bb
│ RCE_Windows_POSTParams.bb
│ Reflected_values_greater_than_three_characters.bb
│ RegisterUser_parameters.bb
│ Secret-keywords-SecLists.bb
│ Secrets_Request.bb
│ Software_Version.bb
│ solarwinds_default_admin.bb
│ Solarwinds_Orion_Request.bb
│ Solarwinds_Orion_Response.bb
│ Source_code.bb
│ Spring Boot Actuators.bb
│ Springboot_Requests.bb
│ SQLi.bb
│ SQLi_Collaborator.bb
│ SQLi_Collaborator_GETParams.bb
│ SQLi_Collaborator_POSTParams.bb
│ SQLi_GETParams.bb
│ SQLi_Parameters.bb
│ SQLi_POSTParams.bb
│ SQLi_TimeBased.bb
│ SQLi_TimeBased_GETParams.bb
│ SQLi_TimeBased_POSTParams.bb
│ SQL_Message_Detected.bb
│ SSRF-Collaborator.bb
│ SSRF-Collaborator_GETParams.bb
│ SSRF-Collaborator_POSTParams.bb
│ SSRF-URLScheme.bb
│ SSRF-URLScheme_GETParams.bb
│ SSRF-URLScheme_POSTParams.bb
│ SSRF_Collaborator_HTTP0_9.bb
│ SSRF_Collaborator_HTTP1_0.bb
│ SSTI.bb
│ SSTI_GET_Params.bb
│ SSTI_Parameters.bb
│ SSTI_POST_Params.bb
│ Subdomain_takeover.bb
│ SVNFinder.bb
│ Swagger-Finder.bb
│ Swagger_found.bb
│ Swagger_Request.bb
│ Symfony_Debug.bb
│ Symfony_Response.bb
│ tags.txt
│ Test_XSS_append.bb
│ Test_XSS_append_encoded.bb
│ Test_XSS_append_GetParams.bb
│ Test_XSS_append_POSTParams.bb
│ Test_XSS_discover.bb
│ Test_XSS_GET_POST.bb
│ Token_Parameters.bb
│ Tomcat_Response_Detection.bb
│ Traefik_Response.bb
│ URL_as_a_Value.bb
│ URL_Path_as_a_Value.bb
│ UserEnum_parameters.bb
│ UUID_Request.bb
│ vBulletin_Response.bb
│ WAF_Found.bb
│ WebCachePoisoning.bb
│ Weblogic_Request.bb
│ Woody_Wordpress_RCE.bb
│ WordPress Config.bb
│ WordPress detection.bb
│ WordPress_Config_Accessible.bb
│ WordPress_directory_listing.bb
│ WordPress_JSmol2WP_SSRF.bb
│ WordPress_Path_Traversal.bb
│ wordpress_users_enum_yoastseo.bb
│ WordPress_user_enum_json.bb
│ WordPress_user_enum_oembed.bb
│ WordPress_XMLRPC_ListMethods.bb
│ WordPress_XMLRPC_Pingback.bb
│ WP_Config.bb
│ X-Headers-Collaborator.bb
│ XSS.bb
│ XSS_GETPOST.bb
│ XSS_GET_Params.bb
│ XSS_HtmlUrlEncode.bb
│ XSS_Parameters.bb
│ XSS_POST_Params.bb
│ XSS_UrlEncode.bb
│ XXE_Linux.bb
│ XXE_Windows.bb
│
└─rules
rule_Artica_Web_Proxy_Auth_bypass.bb
rule_Cisco_Rule.bb
rule_Citrix_Rule.bb
rule_CouchDB_Admin_Exposure.bb
rule_Drupal_Rule.bb
rule_Firebase Database Rule.bb
rule_Fortinet_Fortigate.bb
rule_Jira_Rule.bb
rule_Kubernetes_Rule.bb
rule_LFI_Rule.bb
rule_MAGMI_Remote_Auth.bb
rule_Netsweeper_CodeInjection.bb
rule_OpenRedirect_SSRF_Rule.bb
rule_RCE_Rule.bb
rule_Solarwinds.bb
rule_SpringBoot_Rule.bb
rule_SQLi_Rule.bb
rule_SSTI_Rule.bb
rule_Symfony_Rule.bb
rule_Traefik_Rule.bb
rule_Weblogic_Rule.bb
rule_Wordpress_Rule.bb
rule_XSS_rule.bb使用截图
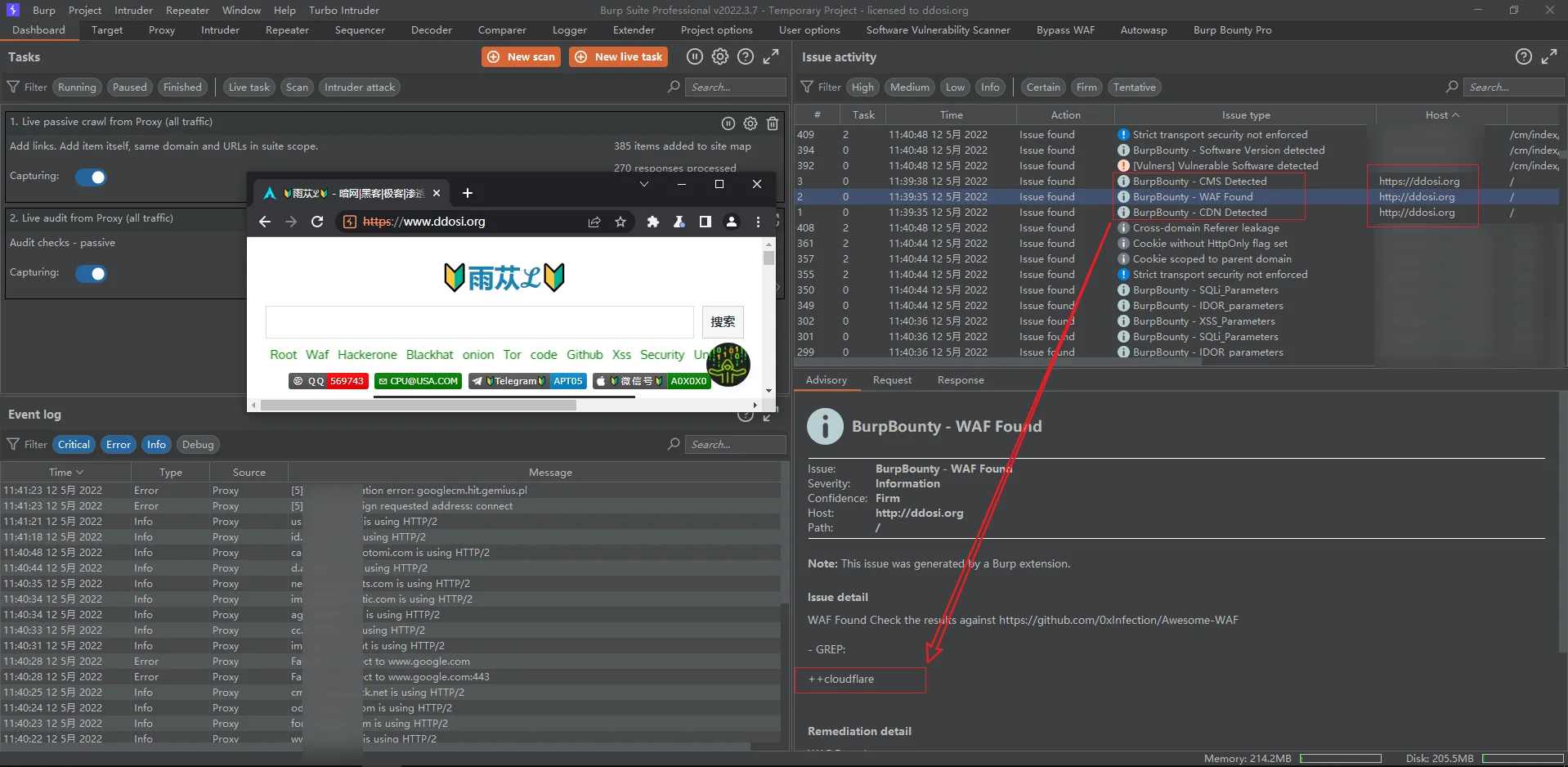
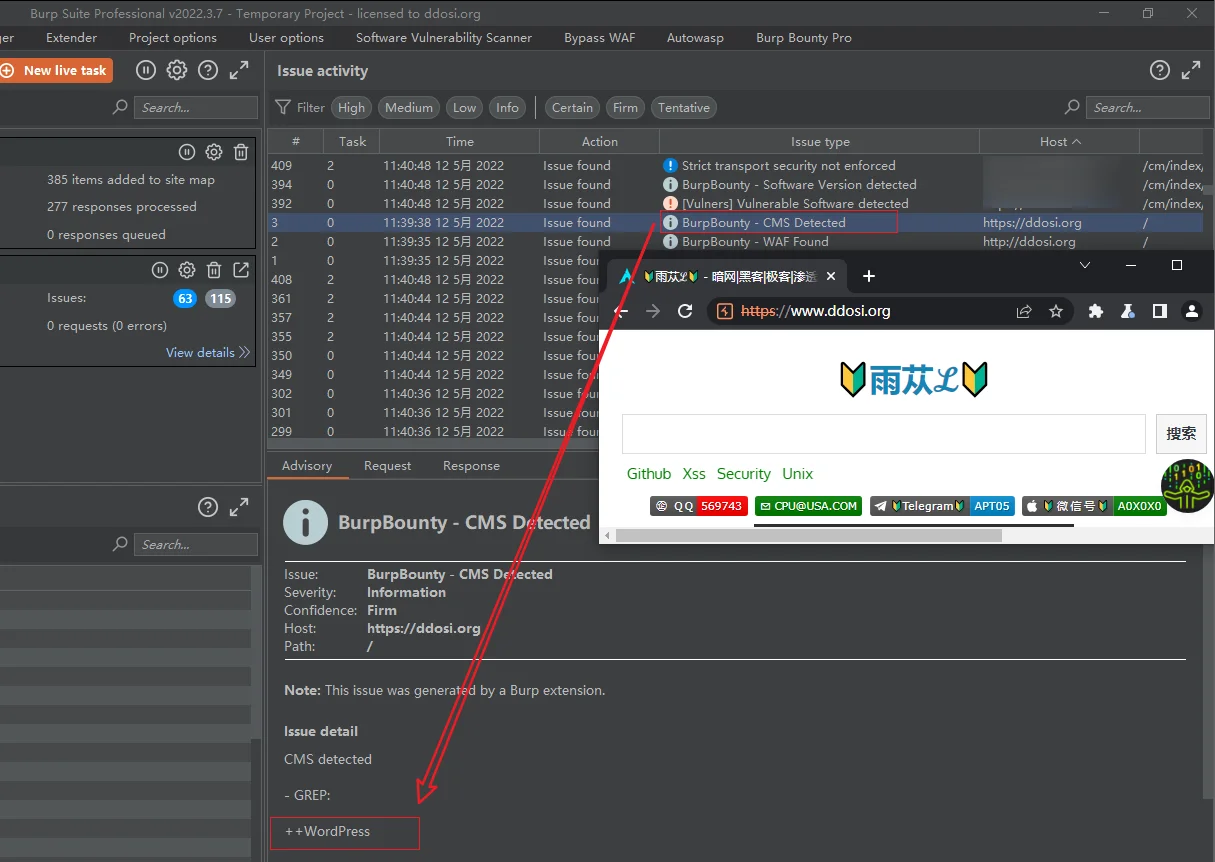
使用方法参考如下往期文章
转载请注明出处及链接

安装报错了是对java版本有限制嘛
看2.3版本安装方法,先安装jython
我在插件中看到zer0daylab,请问这是一个什么组织呢?
你可以理解为供应商