目录导航
简述
haveibeenpwned密码泄露查询API,命令行工具Pwned
Pwned是一个简单的命令行python脚本,用于检查您是否有一个在数据泄露中泄露的密码。这个脚本使用haveibeenpwned API来检查您的密码是否泄露。
该API使用k-匿名模型,允许通过部分散列搜索密码,以便匿名验证密码是否泄漏,但是不会泄露搜索到的密码。
项目地址:
github :https://github.com/sameera-madushan/Pwned
安装方法:
# clone the repo [①克隆git代码]
git clone https://github.com/sameera-madushan/Pwned.git
# change the working directory to Pwned [②切换目录到Pwned目录下]
cd Pwned
# install the requirements [③安装python所需的环境库]
pip3 install -r requirements.txtkali安装pip3
如果你的kali上没有pip,输入下面的命令即可安装pip.
apt-get install python3-pip
使用方法:
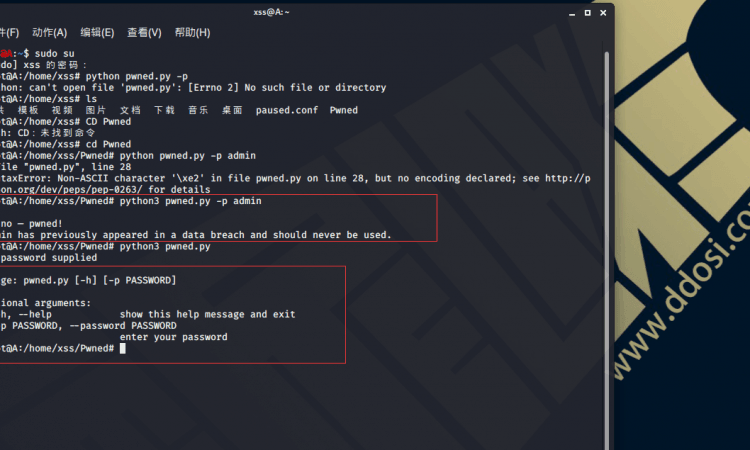
python pwned.py -p <这里输入你的要检测的密码>例如:
python pwned.py -p admin在kali里面的话请加上个3运行,如下所示:
python3 pwned.py -p admin
pwned.py代码如下:
由于github时常会抽筋,对中国区来说很不友好,不知道是国情所致还是国外所封,因.此我把代码直接放上来了.
import hashlib
import requests
import argparse
import re
def check_leak(x):
SHA1 = hashlib.sha1(x.encode('utf-8'))
hash_string = SHA1.hexdigest().upper()
prefix = hash_string[0:5]
header = {
'User-Agent': 'password checker'
}
url = "https://api.pwnedpasswords.com/range/{}".format(prefix)
req = requests.get(url, headers=header).content.decode('utf-8')
hashes = req.split('\r\n')
for suffix in hashes:
hash_list = re.sub(r':(.*)', "", req).split('\n')
for i in hash_list:
real_hash = prefix + i
if hash_string == real_hash:
print("\nOh no — pwned!")
print("{} has previously appeared in a data breach and should never be used. ".format(x))
break
if hash_string != real_hash:
print("\nGood news — no pwnage found!")
print("{} wasn't found in any of the Pwned Passwords loaded into Have I Been Pwned.".format(x))
exit()
parser = argparse.ArgumentParser()
parser.add_argument("-p", "--password", help="enter your password")
args = parser.parse_args()
argv = vars(args)
x = argv['password']
if args.password:
check_leak(x)
else:
print("No password supplied\n")
parser.print_help()
'''
-References-
https://haveibeenpwned.com/API/v3#PwnedPasswords
https://www.troyhunt.com/ive-just-launched-pwned-passwords-version-2/
'''在线随机密码生成器
如果检测到你的密码已泄露,建议使用在线随机密码生成器,生成随机密码,保护你的隐私安全 .
地址: http://www.ddosi.org/mm.html