目录导航
afrog简介
afrog 是一款性能卓越、快速稳定、PoC 可定制的漏洞扫描工具,PoC 包含 CVE、CNVD、默认口令、信息泄露、指纹识别、未授权访问、任意文件读取、命令执行等多种漏洞类型,帮助网络安全从业者快速验证并及时修复漏洞。
特点
- 开源
- 快速、稳定、误报低
- 详细的 html 漏洞报告
- PoC 可定制化、稳定更新
- 活跃的社区 交流群
- 长期维护
示例
基本用法
# 扫描一个目标
afrog -t http://127.0.0.1
# 扫描多个目标
afrog -T urls.txt
# 指定漏扫报告文件
afrog -t http://127.0.0.1-o result.html
高级用法
# 测试 PoC
afrog -t http://127.0.0.1 -P ./test/
afrog -t http://127.0.0.1 -P ./test/demo.yaml
# 按 PoC 关键字扫描
afrog -t http://127.0.0.1 -s tomcat,springboot,shiro
# 按 Poc 漏洞等级扫描
afrog -t http://127.0.0.1 -S high,critical
# 在线更新 afrog-pocs
afrog --up
# 禁用指纹识别,直接漏扫
afrog -t http://127.0.0.1 --nf
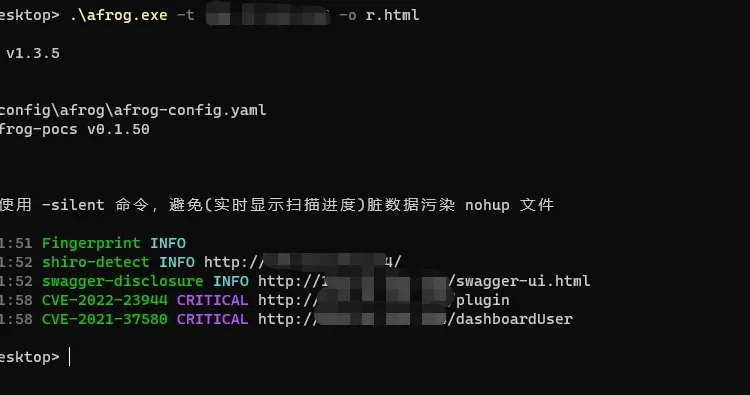
截图
控制台
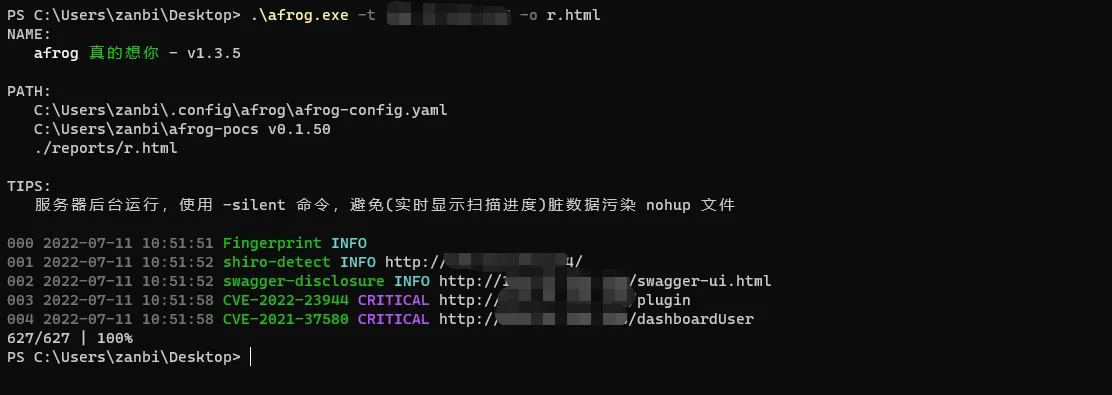
html 报告
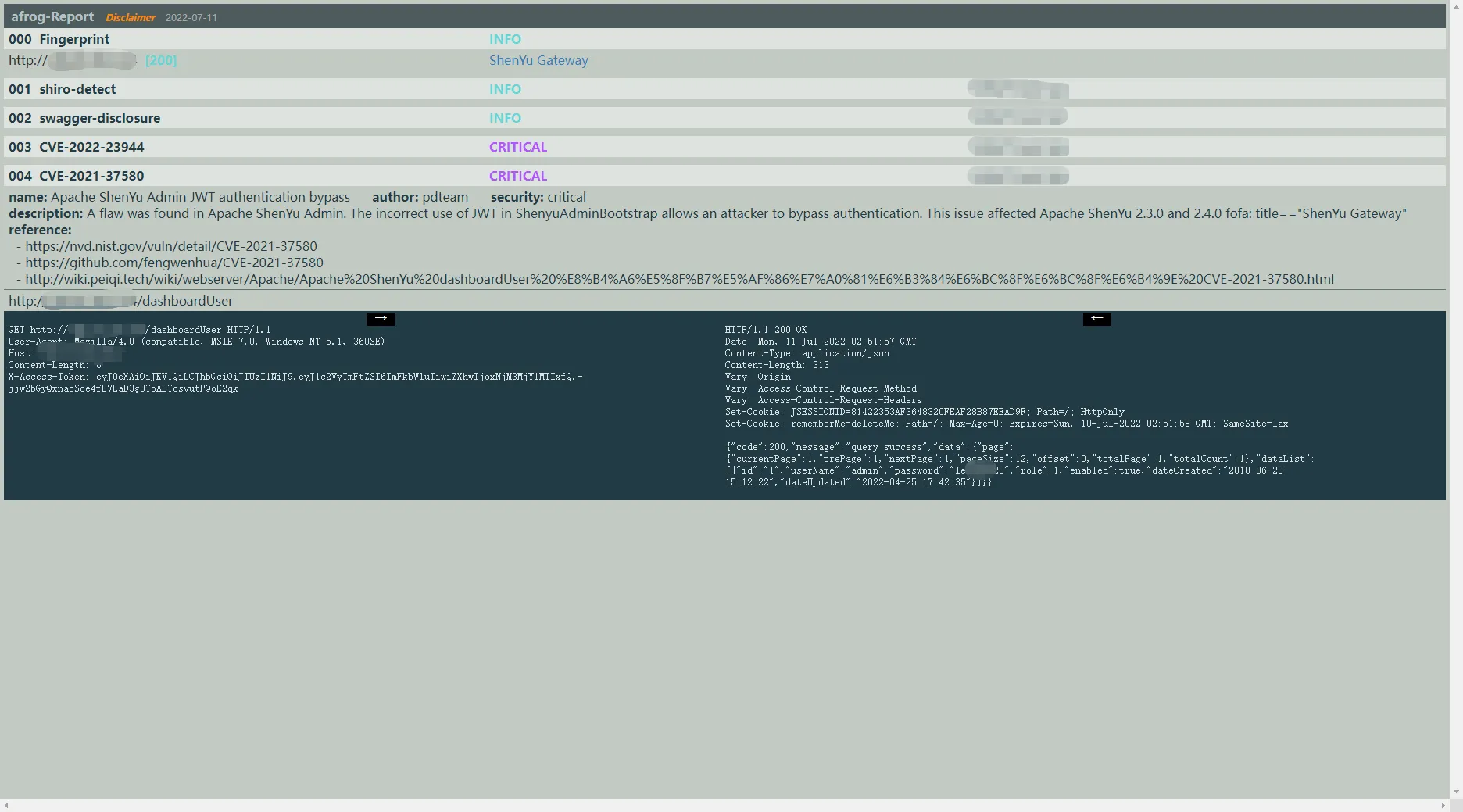
选项参数
版本:
1.3.5
命令:
help, h 显示命令列表或某个命令的帮助.
全局选项:
--target value, -t value 要扫描的目标url/主机
--targets value, -T value 包含要扫描的目标url /主机列表的文件路径(每行一个)
--pocs afrog-pocs, -P afrog-pocs 扫描指定的漏洞时使用的poc.Yaml或poc目录路径(没有默认的afrog-pocs目录)
--output value, -o value 输出HTML报告,例如:-o result.html
--search keyword, -s keyword 通过关键字搜索PoC,例如:-s tomcat,phpinfo
--severity value, -S value 基于严重性运行Pocs,取值为:info、low、medium、high、critical、unknown
--silent 没有进度,只有结果(默认值:false)
--nofinger, --nf 禁用指纹识别(默认:false)
--notips, --nt 禁用显示提示(默认为false)
--updatepocs, --up 更新afrog-pocs(默认值:false)
--help, -h 显示帮助(默认值:false)
--version, -v 输出版本信息(默认为false)扫描测试:
下载地址
①GitHub:
- afrog_darwin_amd64.tar.gz9.91 MB
- afrog_linux_amd64.tar.gz10 MB
- afrog_linux_arm64.tar.gz9.2 MB
- afrog_windows_amd64.zip10.3 MB
②云中转网盘:
yunzhongzhuan.com/#sharefile=hmcKPMeG_61456
解压密码:www.ddosi.org
工具中包含的文件(poc)列表:
----afrog-main
| .gitignore
| go.mod
| go.sum
| LICENSE
| paused.conf
| README.md
|
+---afrog-pocs
| | README.md
| | version
| |
| +---CVE
| | \---2021
| | CVE-2021-27250.yaml
| |
| \---vulnerability
| gitlab-api-user-enum.yaml
| gitlab-public-repos.yaml
| gitlab-public-snippets.yaml
| gitlab-uninitialized-password.yaml
| gitlab-user-enum.yaml
| landray-oa-treexml-rce.yaml
| thinkphp-30-rce.yaml
| thinkphp-50-rce.yaml
| thinkphp-5010-rce.yaml
|
+---cmd
| +---afrog
| | main.go
| |
| +---api
| | main.go
| |
| +---celgo
| | main.go
| |
| +---download
| | main.go
| |
| +---fingerprint
| | | main.go
| | |
| | \---struts
| | structs.go
| |
| +---flag
| | main.go
| |
| +---html
| | main.go
| |
| +---poc
| | main.go
| |
| +---rules
| | main.go
| |
| +---socket
| | main.go
| |
| +---title
| | main.go
| |
| +---workgroup
| | main.go
| |
| \---xray
| | main.go
| |
| \---gopoc
| a.go
| b.go
| c.go
| p.go
| test.go
|
+---docs
| CONTRIBUTION.md
| CONTRIBUTION_en.md
| GUIDE.md
| GUIDE_en.md
| POCLIST.md
| README_en.md
|
+---images
| 2.png
| 3.png
| afrog.jpg
| afrog.png
| con-1.png
| con-2.png
| con-3.png
| con-5.png
| con-6.png
| fourscan.png
| onescan.png
| report-new.png
| scan-new.png
| starlink.png
| threescan.png
| twoscan.png
|
+---internal
| \---runner
| banner.go
| runner.go
|
+---pkg
| +---catalog
| | catalog.go
| | find.go
| | folder.go
| | path.go
| |
| +---config
| | config.go
| | options.go
| |
| +---core
| | cel.go
| | celcompile.go
| | celprogram.go
| | checker.go
| | engine.go
| | excute.go
| | result.go
| | workpool.go
| |
| +---errors
| | errors.go
| |
| +---fingerprint
| | fingerprint.go
| | web_fingerprint_v3.json
| |
| +---gopoc
| | gopoc.go
| | memcache.go
| | mongodb.go
| | ms17010.go
| | redis.go
| | rsync.go
| | tomcat.go
| | zookeeper.go
| |
| +---html
| | html.go
| |
| +---log
| | color.go
| | zap.go
| |
| +---poc
| | poc.go
| |
| +---proto
| | http.pb.go
| | http.proto
| |
| +---protocols
| | +---http
| | | http.go
| | |
| | \---raw
| | http.go
| | raw.go
| |
| +---scan
| | cdn.go
| | ips.go
| | ports.go
| | scan.go
| |
| +---upgrade
| | upgrade.go
| |
| \---utils
| file.go
| iconhash.go
| rand.go
| severity.go
| stringslice.go
| syncfile.go
| tcp.go
| tips.go
| unzip.go
| utils.go
| version.go
|
\---pocs
| d-link-router-command-injection.yaml
| poc.go
|
+---afrog-pocs
| | README.md
| | version
| |
| +---a-fingerprinting
| | activemq-panel.yaml
| | adminer-panel.yaml
| | apisix-panel.yaml
| | appex-lotwan-login-panel.yaml
| | avtech-avn801-camera-panel.yaml
| | azure-kubernetes-service.yaml
| | directadmin-login-panel.yaml
| | django-admin-panel.yaml
| | dlink-panel.yaml
| | dubbo-detect.yaml
| | emessage-panel.yaml
| | fanruanoa-detect.yaml
| | fckeditor.yaml
| | gitlab-panel.yaml
| | grafana-detect.yaml
| | huawei-hg532e-panel.yaml
| | javamelody-detect.yaml
| | jenkins-api-panel.yaml
| | jenkins-login.yaml
| | jira-panel.yaml
| | jupyter-notebook-tech.yaml
| | kubernetes-dashboard.yaml
| | kubernetes-enterprise-manager.yaml
| | kubernetes-metrics.yaml
| | kubernetes-mirantis.yaml
| | kubernetes-resource-report.yaml
| | kubernetes-version.yaml
| | landrayoa-panel.yaml
| | microsoft-exchange-panel.yaml
| | minio-browser.yaml
| | minio-console.yaml
| | mongodb-ops-manager.yaml
| | openerp-database.yaml
| | phpmyadmin-panel.yaml
| | rabbitmq-dashboard.yaml
| | rocketmq-console-exposur.yaml
| | shiro-detect.yaml
| | solarwinds-orion-panel.yaml
| | sonicwall-management-panel.yaml
| | sonicwall-sslvpn-panel.yaml
| | swagger-api-disclosure.yaml
| | terramaster-panel.yaml
| | thinkphp-detect.yaml
| | tomcat-detect.yaml
| | upupw-panel.yaml
| | utt-panel.yaml
| | wayos-panel.yaml
| | weblogic-panel.yaml
| | wordpress-login.yaml
| | zabbix-panel.yaml
| | zentao-detect.yaml
| |
| +---b-disclosure
| | alibaba-canal-info-leak.yaml
| | aspcms-backend-leak.yaml
| | avtech-dvr-exposure.yaml
| | avtech-password-disclosure.yaml
| | dlink-850l-info-leak.yaml
| | e-office-mysql-config-leak.yaml
| | hadoop-disclosure.yaml
| | hikvision-info-leak.yaml
| | hjtcloud-directory-file-leak.yaml
| | huawei-dg8045-home-gateway-exposures.yaml
| | hue-login-panel.yaml
| | kyan-network-monitoring-account-password-leakage.yaml
| | laravel-debug-info-leak.yaml
| | nsfocus-uts-password-leak.yaml
| | openvpn-monitor-disclosure.yaml
| | phpinfo-disclosure.yaml
| | ruijie-eg-info-leak.yaml
| | ruijie-nbr1300g-cli-password-leak.yaml
| | ruijie-smartweb-password-disclosure.yaml
| | seeyon-a6-employee-info-leak.yaml
| | seeyon-oa-cookie-leak.yaml
| | seeyon-session-leak.yaml
| | thinkphp-509-information-disclosure.yaml
| | tianqing-info-leak.yaml
| |
| +---c-unauthorized
| | airflow-unauth.yaml
| | bt742-pma-unauthorized-access.yaml
| | couchdb-unauthorized.yaml
| | druid-monitor-unauth.yaml
| | elasticsearch-unauth.yaml
| | etcd-unauth.yaml
| | frp-dashboard-unauth.yaml
| | h2-database-web-console-unauthorized-access.yaml
| | hadoop-yarn-unauth.yaml
| | hp-officepro-printer-unauthorized.yaml
| | influxdb-unauth.yaml
| | jboss-unauth.yaml
| | jeecg-boot.yaml
| | jenkins-unauthorized-access.yaml
| | jira-service-desk-signup.yaml
| | jira-unauthenticated-adminprojects.yaml
| | jira-unauthenticated-dashboards.yaml
| | jira-unauthenticated-installed-gadgets.yaml
| | jira-unauthenticated-projectcategories.yaml
| | jira-unauthenticated-projects.yaml
| | jira-unauthenticated-resolutions.yaml
| | jira-unauthenticated-screens.yaml
| | jira-unauthenticated-user-picker.yaml
| | jupyter-notebook-unauthorized-access.yaml
| | kafka-manager-unauth.yaml
| | kibana-unauth.yaml
| | kubernetes-unauth.yaml
| | nacos-v1-auth-bypass.yaml
| | nifi-api-unauthorized-access.yaml
| | pyspider-unauthorized-access.yaml
| | qizhi-fortressaircraft-unauthorized.yaml
| | ruoyi-cms-unauth.yaml
| | spark-api-unauth.yaml
| | spark-webui-unauth.yaml
| | springboot-actuator-unauth.yaml
| | storm-unauthorized-access.yaml
| | tensorboard-unauth.yaml
| | tongda-meeting-unauth.yaml
| | zabbix-authentication-bypass.yaml
| | zabbix-dashboards-access.yaml
| |
| +---d-default-pwd
| | activemq-default-password.yaml
| | alibaba-canal-default-password.yaml
| | ambari-default-password.yaml
| | aolynk-br304-default-password.yaml
| | arl-default-password.yaml
| | axis2-default-password.yaml
| | azkaban-default-password.yaml
| | chinaunicom-default-login.yaml
| | datang-ac-default-password-cnvd-2021-04128.yaml
| | dell-idrac9-default-password.yaml
| | dlink-default-password.yaml
| | dubbo-admin-default-password.yaml
| | exacqvision-default-password.yaml
| | gitlab-weak-login.yaml
| | grafana-default-password.yaml
| | hikvision-intercom-service-default-password.yaml
| | ibm-storage-default-password.yaml
| | jenkins-default-pwd.yaml
| | jinher-oa-c6-default-password.yaml
| | jmx-default-password.yaml
| | kafka-center-default-password.yaml
| | kingsoft-v8-default-password.yaml
| | minio-default-password.yaml
| | mofi4500-default-password.yaml
| | netentsec-icg-default-password.yaml
| | nexus-default-password.yaml
| | nps-default-password.yaml
| | nsicg-default-password.yaml
| | ofbiz-default-password.yaml
| | openerp-default-password.yaml
| | oracle-business-intelligence-password.yaml
| | panabit-gateway-default-password.yaml
| | panabit-ixcache-default-password.yaml
| | rabbitmq-default-password.yaml
| | rancher-default-password.yaml
| | ricoh-weak-password.yaml
| | rockmongo-default-password.yaml
| | rseenet-default-password.yaml
| | secnet-ac-default-password.yaml
| | seeddms-default-password.yaml
| | showdoc-default-password.yaml
| | spectracom-default-password.yaml
| | telecom-gateway-default-password.yaml
| | tomcat-default-login.yaml
| | trilithic-viewpoint-default-password.yaml
| | utt-default-password.yaml
| | versa-default-password.yaml
| | wayos-default-password.yaml
| | weblogic-weak-login.yaml
| | xerox7-default-password.yaml
| | zabbix-default-password.yaml
| |
| +---e-vulnerability
| | acti-video-read-file.yaml
| | alibaba-canal-config-leak.yaml
| | amtt-hiboss-server-ping-rce.yaml
| | anyproxy-directory-traversal.yaml
| | bohuangwanglong-cmd-php-rce.yaml
| | bohuawanglong-users-xml-password-leak.yaml
| | byzoro-smart-importhtml-rce.yaml
| | cacti-weathermap-file-write.yaml
| | clickhouse-api-unauth.yaml
| | consul-rexec-rce.yaml
| | consul-service-rce.yaml
| | couchdb-adminparty.yaml
| | dahua-dss-file-read.yaml
| | dedecms-carbuyaction-fileinclude.yaml
| | dedecms-guestbook-sqli.yaml
| | dedecms-membergroup-sqli.yaml
| | dedecms-url-redirection.yaml
| | discuz-v72-sqli.yaml
| | discuz-wechat-plugins-unauth.yaml
| | dlink-dsl-2888a-rce.yaml
| | dlink-sharecenter-dns-320-rce.yaml
| | docker-registry.yaml
| | docker-remote-api-unauth.yaml
| | docker-remote-api.yaml
| | dockercfg-config.yaml
| | dotnetcms-sqli.yaml
| | duomicms-sqli.yaml
| | e-bridge-saveyzjfile-file-read.yaml
| | e-cology-arbitrary-file-upload.yaml
| | e-cology-e-office-officeserver-file-read.yaml
| | e-cology-filedownload-directory-traversal.yaml
| | e-cology-getsqldata-sql-inject.yaml
| | e-cology-springframework-directory-traversal.yaml
| | e-cology-syncuserinfo-sqli.yaml
| | e-cology-v8-sqli.yaml
| | e-cology-validate-sqli.yaml
| | e-cology-workflowcentertreedata-sqli.yaml
| | e-office-v10-sql-inject.yaml
| | ecshop-collection-list-sqli.yaml
| | ecshop-rce.yaml
| | egroupware-rce.yaml
| | etouch-v2-sqli.yaml
| | eyou-mail-moni-detail-rce.yaml
| | fangweicms-sqli.yaml
| | fanruan-oa-v9-designsavevg-upload-file.yaml
| | fastjson-1-2-24-rce.yaml
| | fastjson-1-2-41-rce.yaml
| | fastjson-1-2-42-rce.yaml
| | fastjson-1-2-43-rce.yaml
| | fastjson-1-2-47-rce.yaml
| | fastjson-1-2-62-rce.yaml
| | fastjson-1-2-67-rce.yaml
| | fastjson-1-2-68-rce.yaml
| | feifeicms-lfr.yaml
| | feiyuxing-info-leak.yaml
| | finecms-sqli.yaml
| | finereport-directory-traversal.yaml
| | flink-upload-rce.yaml
| | flix-ax8-download-read-file.yaml
| | generic-windows-lfi.yaml
| | git-leak.yaml
| | grafana-file-read.yaml
| | h3c-imc-rce.yaml
| | h3c-mpsec-isg1000-file-read.yaml
| | h3c-secparh-any-user-login.yaml
| | h3c-secpath-firewall-file-read.yaml
| | hanming-video-conferencing-file-read.yaml
| | haofeng-firewall-setdomain-unauth.yaml
| | hikvision-gateway-data-file-read.yaml
| | hikvision-showfile-file-read.yaml
| | hjtcloud-arbitrary-fileread.yaml
| | huawei-home-gateway-hg659-fileread.yaml
| | huijietong-cloud-fileread.yaml
| | huiwen-book-config-properties-info-leak.yaml
| | iis-put-getshell.yaml
| | ikuai-login-panel.yaml
| | ioffice-oa-iofileexport-read-file.yaml
| | jeewms-showordownbyurl-fileread.yaml
| | jinher-oa-c6-download-file-read.yaml
| | joomla-component-vreview-sql.yaml
| | jumpserver-unauth-rce.yaml
| | kedacom-gateway-file-read.yaml
| | kedacom-mts-file-read.yaml
| | kingdee-eas-directory-traversal.yaml
| | kingsoft-v8-file-read.yaml
| | kingsoft-v8-get-file-content-file-read.yaml
| | kingsoft-v8-rce.yaml
| | kyan-network-license-php-rce.yaml
| | kyan-network-module-php-rce.yaml
| | kyan-network-time-php-rce.yaml
| | landray-oa-admin-do-jndi-rce.yaml
| | landray-oa-custom-jsp-fileread.yaml
| | landray-oa-syssearchmain-rce.yaml
| | laravel-improper-webdir.yaml
| | maccms-rce.yaml
| | maccmsv10-backdoor.yaml
| | magicflow-main-xp-file-read.yaml
| | maike-ras-cookie-bypass.yaml
| | metinfo-file-read.yaml
| | msa-gateway-read-file.yaml
| | msvod-sqli.yaml
| | myucms-lfr.yaml
| | natshell-arbitrary-file-read.yaml
| | netentsec-ngfw-rce.yaml
| | netmizer-log-management-cmd-php-rce.yaml
| | netmizer-log-management-data-directory-traversal.yaml
| | netpower-download-php-file-read.yaml
| | ns-asg-file-read.yaml
| | nuuo-file-inclusion.yaml
| | oa8000-workflowservice-sql-inject.yaml
| | odoo-file-read.yaml
| | pbootcms-database-file-download.yaml
| | php-zerodium-backdoor.yaml
| | phpmyadmin-misconfiguration.yaml
| | phpmyadmin-server-import.yaml
| | phpmyadmin-setup-deserialization.yaml
| | phpmyadmin-setup.yaml
| | phpok-sqli.yaml
| | phpshe-sqli.yaml
| | phpstudy-backdoor-rce.yaml
| | phpstudy-nginx-wrong-resolve.yaml
| | powercreator-arbitrary-file-upload.yaml
| | qibocms-sqli.yaml
| | qilin-bastion-host-rce.yaml
| | resin-inputfile-fileread.yaml
| | resin-viewfile-fileread.yaml
| | ruijie-eg-cli-rce.yaml
| | ruijie-eg-file-read.yaml
| | ruoyi-management-fileread.yaml
| | samsung-wea453e-default-pwd.yaml
| | samsung-wea453e-rce.yaml
| | samsung-wlan-ap-wea453e-rce.yaml
| | sangfor-ba-rce.yaml
| | sangfor-edr-arbitrary-admin-login.yaml
| | sangfor-edr-cssp-rce.yaml
| | sangfor-edr-tool-rce.yaml
| | sapido-router-rce.yaml
| | seacms-before-v992-rce.yaml
| | seacms-rce.yaml
| | seacms-sqli.yaml
| | seacms-v654-rce.yaml
| | seacmsv645-command-exec.yaml
| | seeyon-a6-config-disclosure.yaml
| | seeyon-a6-createmysql-disclosure.yaml
| | seeyon-a6-setextno-sql-inject.yaml
| | seeyon-a8-htmlofficeservlet-upload.yaml
| | seeyon-a8-status-disclosure.yaml
| | seeyon-wooyun-2015-0108235-sqli.yaml
| | seeyon-wooyun-2015-148227.yaml
| | selea-targa-camera-lfi.yaml
| | selea-targa-camera-read-file.yaml
| | shiziyu-cms-apicontroller-sqli.yaml
| | showdoc-uploadfile.yaml
| | smartoa-emaildownload-file-read.yaml
| | solr-admin-query.yaml
| | solr-file-read.yaml
| | solr-log4j-rce.yaml
| | sonicwall-ssl-vpn-rce.yaml
| | spon-ip-intercom-file-read.yaml
| | spon-ip-intercom-ping-rce.yaml
| | springboot-h2-db-rce.yaml
| | svn-leak.yaml
| | tamronos-iptv-rce.yaml
| | tenda-11n-cookie-unauth-access.yaml
| | tenda-w15e-routercfm-cfg-config-leak.yaml
| | thinkadmin-v6-readfile.yaml
| | thinkcmf-lfi.yaml
| | thinkcmf-write-shell.yaml
| | thinkphp-2-rce.yaml
| | thinkphp-5022-5129-rce.yaml
| | thinkphp-5023-rce.yaml
| | thinkphp-5024-5130-rce.yaml
| | thinkphp-v6-file-write.yaml
| | tongda-insert-sql-inject.yaml
| | tongda-logincheck-code-getcookie.yaml
| | tongda-path-traversal.yaml
| | tongda-report_bi-func-sql-inject.yaml
| | tongda-swfupload-new-sql-inject.yaml
| | tongda-user-session-disclosure.yaml
| | tongda-v2014-disclosure.yaml
| | tongda-v2017-uploadfile.yaml
| | tpshop-directory-traversal.yaml
| | tpshop-sqli.yaml
| | typecho-rce.yaml
| | unifi-network-log4j-rce.yaml
| | vesystem-upload-file.yaml
| | vmware-vcenter-arbitrary-file-read.yaml
| | vrealize-operations-log4j-rce.yaml
| | wanhu-oa-download-ftp-file-read.yaml
| | wanhu-oa-download-old-file-read.yaml
| | wanhu-oa-downloadhttp-file-read.yaml
| | wanhu-oa-fileupload-controller-upload.yaml
| | wanhu-oa-smartupload-upload-file.yaml
| | web-config.yaml
| | weblogic-ssrf.yaml
| | weiphp-path-traversal.yaml
| | weiphp-sql.yaml
| | wholeton-vpn-info-leak.yaml
| | wisegiga-nas-down-data-php-file-read.yaml
| | wisegiga-nas-group-php-rce.yaml
| | WOOYUN-2010-080723.yaml
| | wordpress-ext-adaptive-images-lfi.yaml
| | wordpress-ext-mailpress-rce.yaml
| | wuzhicms-v410-sqli.yaml
| | xdcms-sql.yaml
| | yapi-rce.yaml
| | yccms-rce.yaml
| | yimi-oa-getfile-file-read.yaml
| | yongyou-fe-templateoftaohong-manager-path-traversal.yaml
| | yongyou-u8-oa-sqli.yaml
| | yonyou-grp-u8-sqli-to-rce.yaml
| | yonyou-grp-u8-sqli.yaml
| | yonyou-nc-arbitrary-file-upload.yaml
| | yonyou-nc-bsh-servlet-bshservlet-rce.yaml
| | yungoucms-sqli.yaml
| | zcms-v3-sqli.yaml
| | zzcms-zsmanage-sqli.yaml
| |
| +---f-CNVD
| | +---2007
| | | CNVD-200705-315.yaml
| | |
| | +---2016
| | | CNNVD-201610-923.yaml
| | |
| | +---2017
| | | CNVD-2017-20077.yaml
| | |
| | +---2018
| | | CNVD-2018-04757.yaml
| | | CNVD-2018-13393.yaml
| | |
| | +---2019
| | | CNVD-2019-01348.yaml
| | | CNVD-2019-16798.yaml
| | | CNVD-2019-22239.yaml
| | | CNVD-2019-32204.yaml
| | | CNVD-2019-34135.yaml
| | |
| | +---2020
| | | CNVD-2020-23735.yaml
| | | CNVD-2020-57264.yaml
| | | CNVD-2020-58823.yaml
| | | CNVD-2020-62422.yaml
| | | CNVD-2020-62853.yaml
| | | CNVD-2020-67113.yaml
| | | CNVD-2020-73282.yaml
| | |
| | \---2021
| | CNVD-2021-01627.yaml
| | CNVD-2021-04128.yaml
| | CNVD-2021-09650.yaml
| | CNVD-2021-10543.yaml
| | CNVD-2021-14536.yaml
| | CNVD-2021-15822.yaml
| | CNVD-2021-15824.yaml
| | CNVD-2021-32799.yaml
| | CNVD-2021-33202.yaml
| | CNVD-2021-39012.yaml
| | CNVD-2021-39067.yaml
| | CNVD-2021-42372.yaml
| | CNVD-2021-49104.yaml
| |
| +---g-CVE
| | +---2007
| | | CVE-2007-4556.yaml
| | |
| | +---2010
| | | CVE-2010-1871.yaml
| | | CVE-2010-2861.yaml
| | |
| | +---2012
| | | CVE-2012-0392.yaml
| | | CVE-2012-1823.yaml
| | |
| | +---2013
| | | CVE-2013-1965.yaml
| | | CVE-2013-2251.yaml
| | |
| | +---2014
| | | CVE-2014-3120.yaml
| | | CVE-2014-3704.yaml
| | | CVE-2014-6271.yaml
| | |
| | +---2015
| | | CVE-2015-1427.yaml
| | | CVE-2015-3337.yaml
| | | CVE-2015-5531.yaml
| | | CVE-2015-7297.yaml
| | | CVE-2015-8399.yaml
| | |
| | +---2016
| | | CVE-2016-10134.yaml
| | | CVE-2016-3081.yaml
| | | CVE-2016-3088.yaml
| | | CVE-2016-4977.yaml
| | |
| | +---2017
| | | CVE-2017-1000028.yaml
| | | CVE-2017-10271.yaml
| | | CVE-2017-11610.yaml
| | | CVE-2017-12149.yaml
| | | CVE-2017-12611.yaml
| | | CVE-2017-12615.yaml
| | | CVE-2017-12629.yaml
| | | CVE-2017-12635.yaml
| | | CVE-2017-16877.yaml
| | | CVE-2017-16894.yaml
| | | CVE-2017-5521.yaml
| | | CVE-2017-5638.yaml
| | | CVE-2017-7504.yaml
| | | CVE-2017-7921.yaml
| | | CVE-2017-8229.yaml
| | | CVE-2017-8917.yaml
| | | CVE-2017-9791.yaml
| | | CVE-2017-9841.yaml
| | |
| | +---2018
| | | CVE-2018-1000533.yaml
| | | CVE-2018-1000600.yaml
| | | CVE-2018-1000861.yaml
| | | CVE-2018-10735.yaml
| | | CVE-2018-10736.yaml
| | | CVE-2018-10737.yaml
| | | CVE-2018-10738.yaml
| | | CVE-2018-11686.yaml
| | | CVE-2018-11759.yaml
| | | CVE-2018-11776.yaml
| | | CVE-2018-12613.yaml
| | | CVE-2018-1273.yaml
| | | CVE-2018-13379.yaml
| | | CVE-2018-17246.yaml
| | | CVE-2018-19127.yaml
| | | CVE-2018-3760.yaml
| | | CVE-2018-6605.yaml
| | | CVE-2018-6910.yaml
| | | CVE-2018-7314.yaml
| | | CVE-2018-7490.yaml
| | | CVE-2018-7600.yaml
| | | CVE-2018-7662.yaml
| | | CVE-2018-7700.yaml
| | | CVE-2018-8033.yaml
| | | CVE-2018-8715.yaml
| | | CVE-2018-8770.yaml
| | | CVE-2018-9995.yaml
| | |
| | +---2019
| | | CVE-2019-0193.yaml
| | | CVE-2019-0230.yaml
| | | CVE-2019-10758.yaml
| | | CVE-2019-11248.yaml
| | | CVE-2019-11510.yaml
| | | CVE-2019-11581.yaml
| | | CVE-2019-12725.yaml
| | | CVE-2019-15107.yaml
| | | CVE-2019-16097.yaml
| | | CVE-2019-16278.yaml
| | | CVE-2019-16313.yaml
| | | CVE-2019-16663.yaml
| | | CVE-2019-16759.yaml
| | | CVE-2019-16920.yaml
| | | CVE-2019-16996.yaml
| | | CVE-2019-16997.yaml
| | | CVE-2019-17418.yaml
| | | CVE-2019-17506.yaml
| | | CVE-2019-17558.yaml
| | | CVE-2019-18394.yaml
| | | CVE-2019-19781.yaml
| | | CVE-2019-19985.yaml
| | | CVE-2019-20085.yaml
| | | CVE-2019-20224.yaml
| | | CVE-2019-2725.yaml
| | | CVE-2019-2729.yaml
| | | CVE-2019-3396.yaml
| | | CVE-2019-3799.yaml
| | | CVE-2019-5127.yaml
| | | CVE-2019-5418.yaml
| | | CVE-2019-6340.yaml
| | | CVE-2019-7192.yaml
| | | CVE-2019-7238.yaml
| | | CVE-2019-8442.yaml
| | | CVE-2019-8449.yaml
| | | CVE-2019-8451.yaml
| | | CVE-2019-9670.yaml
| | |
| | +---2020
| | | CVE-2020-10148.yaml
| | | CVE-2020-10199.yaml
| | | CVE-2020-10204.yaml
| | | CVE-2020-11455.yaml
| | | CVE-2020-11710.yaml
| | | CVE-2020-11738.yaml
| | | CVE-2020-11991.yaml
| | | CVE-2020-13937.yaml
| | | CVE-2020-13945.yaml
| | | CVE-2020-14179.yaml
| | | CVE-2020-14181.yaml
| | | CVE-2020-14750.yaml
| | | CVE-2020-15568.yaml
| | | CVE-2020-16846.yaml
| | | CVE-2020-17519.yaml
| | | CVE-2020-17530.yaml
| | | CVE-2020-21224.yaml
| | | CVE-2020-24571.yaml
| | | CVE-2020-25078.yaml
| | | CVE-2020-26413.yaml
| | | CVE-2020-27986.yaml
| | | CVE-2020-28185.yaml
| | | CVE-2020-28187.yaml
| | | CVE-2020-28188.yaml
| | | CVE-2020-3452.yaml
| | | CVE-2020-35476.yaml
| | | CVE-2020-35736.yaml
| | | CVE-2020-5284.yaml
| | | CVE-2020-5405.yaml
| | | CVE-2020-5410.yaml
| | | CVE-2020-5515.yaml
| | | CVE-2020-5902.yaml
| | | CVE-2020-7980.yaml
| | | CVE-2020-8191.yaml
| | | CVE-2020-8193.yaml
| | | CVE-2020-8209.yaml
| | | CVE-2020-8515.yaml
| | | CVE-2020-9376.yaml
| | | CVE-2020-9483.yaml
| | | CVE-2020-9496.yaml
| | | CVE-2020-9757.yaml
| | |
| | +---2021
| | | CVE-2021-1497.yaml
| | | CVE-2021-1499.yaml
| | | CVE-2021-21234.yaml
| | | CVE-2021-21402.yaml
| | | CVE-2021-21972.yaml
| | | CVE-2021-21975.yaml
| | | CVE-2021-21985.yaml
| | | CVE-2021-22145.yaml
| | | CVE-2021-22205.yaml
| | | CVE-2021-22214.yaml
| | | CVE-2021-22986.yaml
| | | CVE-2021-25282.yaml
| | | CVE-2021-26084.yaml
| | | CVE-2021-26085.yaml
| | | CVE-2021-26855.yaml
| | | CVE-2021-27905.yaml
| | | CVE-2021-28164.yaml
| | | CVE-2021-29622.yaml
| | | CVE-2021-3019.yaml
| | | CVE-2021-30461.yaml
| | | CVE-2021-3129.yaml
| | | CVE-2021-31602.yaml
| | | CVE-2021-31805.yaml
| | | CVE-2021-3223.yaml
| | | CVE-2021-3297.yaml
| | | CVE-2021-33044.yaml
| | | CVE-2021-36260.yaml
| | | CVE-2021-3654.yaml
| | | CVE-2021-36749.yaml
| | | CVE-2021-37580.yaml
| | | CVE-2021-40438.yaml
| | | CVE-2021-41349.yaml
| | | CVE-2021-41381.yaml
| | | CVE-2021-41773.yaml
| | | CVE-2021-42013.yaml
| | | CVE-2021-43287.yaml
| | | CVE-2021-43734.yaml
| | | CVE-2021-44451.yaml
| | | CVE-2021-46422.yaml
| | |
| | \---2022
| | CVE-2022-0540.yaml
| | CVE-2022-1388.yaml
| | CVE-2022-21371.yaml
| | CVE-2022-22947.yaml
| | CVE-2022-22954.yaml
| | CVE-2022-22963.yaml
| | CVE-2022-22965.yaml
| | CVE-2022-23131.yaml
| | CVE-2022-23134.yaml
| | CVE-2022-23178.yaml
| | CVE-2022-23944.yaml
| | CVE-2022-24112.yaml
| | CVE-2022-24124.yaml
| | CVE-2022-24260.yaml
| | CVE-2022-24990.yaml
| | CVE-2022-25084.yaml
| | CVE-2022-25369.yaml
| | CVE-2022-25568.yaml
| | CVE-2022-26134.yaml
| | CVE-2022-26148.yaml
| | CVE-2022-26352.yaml
| | CVE-2022-29303.yaml
| | CVE-2022-29464.yaml
| | CVE-2022-30525.yaml
| |
| \---h-unreviewed
| apache-ofbiz-log4j-rce.yaml
| mobileiron-log4j-jndi-rce.yaml
| springboot-log4j-rce.yaml
|
+---deleted
| alphaweb-default-password.yaml
| CVE-2015-7450.yaml
| CVE-2020-13925.yaml
| CVE-2021-44228.yaml
| h2-console-panel.yaml
| pbootcms-rce.yaml
| robots-txt.yaml
|
+---peiqi
| | README.md
| |
| \---img
| afrog.ico
|
\---test
demo.yaml
poc.yaml
stop_if_match_test.yaml自定义poc:
POC,全称 Proof of Concept,指一段漏洞证明的说明或攻击样例
文件名
后缀 .yaml
CVE-2022-0202.yaml
id
[公司]产品-漏洞名称|CVE/CNVD-2021-XXXX
id: CVE-2022-0202 // good id: seeyon-ajax-unauth // good id: zhiyuan-oa-unauth // bad
info
包含 name、author、severity、description、reference
id: CVE-2022-22947
info:
name: Spring Cloud Gateway Code Injection
author: alex
severity: critical
description: |
Spring Cloud Gateway 远程代码执行漏洞(CVE-2022-22947)发生在Spring Cloud Gateway...
影响版本:Spring Cloud Gateway 3.1.x < 3.1.1 、Spring Cloud Gateway < 3.0.7
官方已发布安全版本,请及时下载更新,下载地址:https://github.com/spring-cloud/spring-cloud-gateway
FOFA:app="vmware-SpringBoot-framework"
reference:
- https://mp.weixin.qq.com/s/qIAcycsO_L9JKisG5Bgg_w // 必须是列表(数组)形式
name:漏洞名称,尽量英文且官方用语
author:大佬名称
severity: 漏洞等级,分为critical、high、mideum、low、info,请参考 [National Vulnerability Database]
description: (可选填)包含 漏洞描述、漏洞影响、网络测绘、修复建议 等
reference: (可选填)参考链接,必须数组形式,否则 poc 无法验证
rules
示例
rules:
r0:
request:
method: GET
path: /phpinfo.php
exppression: response.status == 200 && response.body.bcontains(b'PHP Version')
stop_if_match: true
r1:
before_sleep: 6
request:
method: GET
path: /info.php
expresssion: response.status == 200 && response.body.bcontains(b'PHP Version')
stop_if_mismatch: true
expression: r0() || r1()
rules:定义规则组
r0 / r1 : 子规则,自定义名称,不能重复
request: 表示 http request 请求
method: 表示 http request method 方法
path: 表示 http request URL 请求的 PATH
expresssion:子规则的验证表达式,用于验证 r0 或 r1 是否匹配规则。比如:response.status == 200 && response.body.bcontains(b'PHP Version')表示 request 请求返回状态码必须是 200 且 源码必须含有 PHP Version 关键字
stop_if_match: 如果匹配就停止
stop_if_mismatch:如果不匹配就停止
before_sleep: 顾名思义,http 请求前 sleep 6 秒钟
expression: 最外面的 expression 是 rules 的验证表达式,r0() || r1() 表示 r0 和 r1 两个规则,匹配一个表达式就为 true,代表漏洞存在。
如果 rules 表达式都是
||关系,比如:r0() || r1() || r2() … ,默认执行stop_if_match动作。同理,如果表达式都是&&关系,默认执行stop_if_mismatch动作。
raw http
set:
hostname: request.url.host
rules:
r0:
request:
raw: |
GET .//WEB-INF/web.xml HTTP/1.1
Host: {{hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
expression: response.status == 200 && response.body.bcontains(b'<web-app') && response.body.bcontains(b'</web-app>') && (response.raw_header.bcontains(b'application/xml') || response.raw_header.bcontains(b'text/xml'))
r1:
request:
raw: |
GET .//WEB-INF/weblogic.xml HTTP/1.1
Host: {{hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:99.0) Gecko/20100101 Firefox/99.0
expression: response.status == 200 && response.body.bcontains(b'<weblogic-web-app') && response.body.bcontains(b'</weblogic-web-app>') && (response.raw_header.bcontains(b'application/xml') || response.raw_header.bcontains(b'text/xml'))
expression: r0() || r1()
raw: 顾名思义,支持原生 http 请求
免责声明
本工具仅面向合法授权的企业安全建设行为,如您需要测试本工具的可用性,请自行搭建靶机环境。
为避免被恶意使用,本项目所有收录的poc均为漏洞的理论判断,不存在漏洞利用过程,不会对目标发起真实攻击和漏洞利用。
在使用本工具进行检测时,您应确保该行为符合当地的法律法规,并且已经取得了足够的授权。请勿对非授权目标进行扫描。
如您在使用本工具的过程中存在任何非法行为,您需自行承担相应后果,我们将不承担任何法律及连带责任。
在安装并使用本工具前,请您务必审慎阅读、充分理解各条款内容,限制、免责条款或者其他涉及您重大权益的条款可能会以加粗、加下划线等形式提示您重点注意。 除非您已充分阅读、完全理解并接受本协议所有条款,否则,请您不要安装并使用本工具。您的使用行为或者您以其他任何明示或者默示方式表示接受本协议的,即视为您已阅读并同意本协议的约束。
项目地址:
GitHub:
https://github.com/zan8in/afrog
转载请注明出处及链接