目录导航
Web Security & Bug Bounty: Learn Penetration Testing in 2021
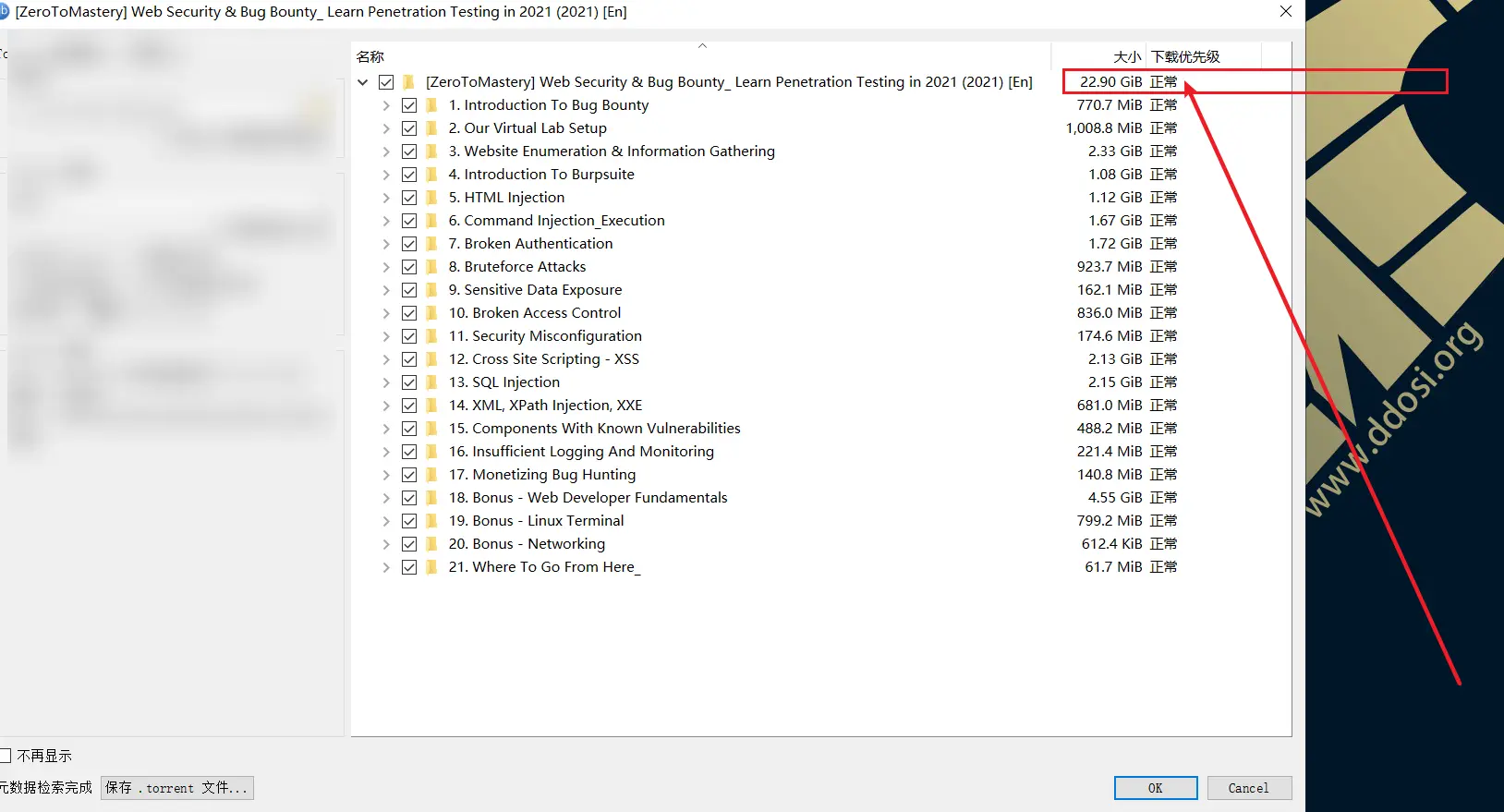
此教程文件总大小为22.91GB
语言:英语
雨苁:祝愿每位愿意付出时间学习的hack都能更上一层楼.
文件目录
大纲[英文]
1. Introduction To Bug Bounty
2. Our Virtual Lab Setup
3. Website Enumeration & Information Gathering
4. Introduction To Burpsuite
5. HTML Injection
6. Command Injection_Execution
7. Broken Authentication
8. Bruteforce Attacks
9. Sensitive Data Exposure
10. Broken Access Control
11. Security Misconfiguration
12. Cross Site Scripting - XSS
13. SQL Injection
14. XML, XPath Injection, XXE
15. Components With Known Vulnerabilities
16. Insufficient Logging And Monitoring
17. Monetizing Bug Hunting
18. Bonus - Web Developer Fundamentals
19. Bonus - Linux Terminal
20. Bonus - Networking
21. Where To Go From Here_大纲[中文]
1. Bug Bounty简介
2. 我们的虚拟实验室安装
3. 网站枚举和信息收集
4. 介绍Burpsuite
5. HTML注入
6. 命令Injection_Execution
7. 破碎的身份验证
8. Bruteforce攻击
9. 敏感数据暴露
10. 破碎的访问控制
11. 安全错误配置
12. 跨站脚本- XSS
13. SQL注入
14. XML, XPath注入,XXE
15. 具有已知漏洞的组件
16. 日志和监控不足
17. 货币化Bug狩猎
18. 奖金- Web开发人员基础
19. 奖金- Linux终端
20. 奖金——网络
21. 何去何从完整目录列表
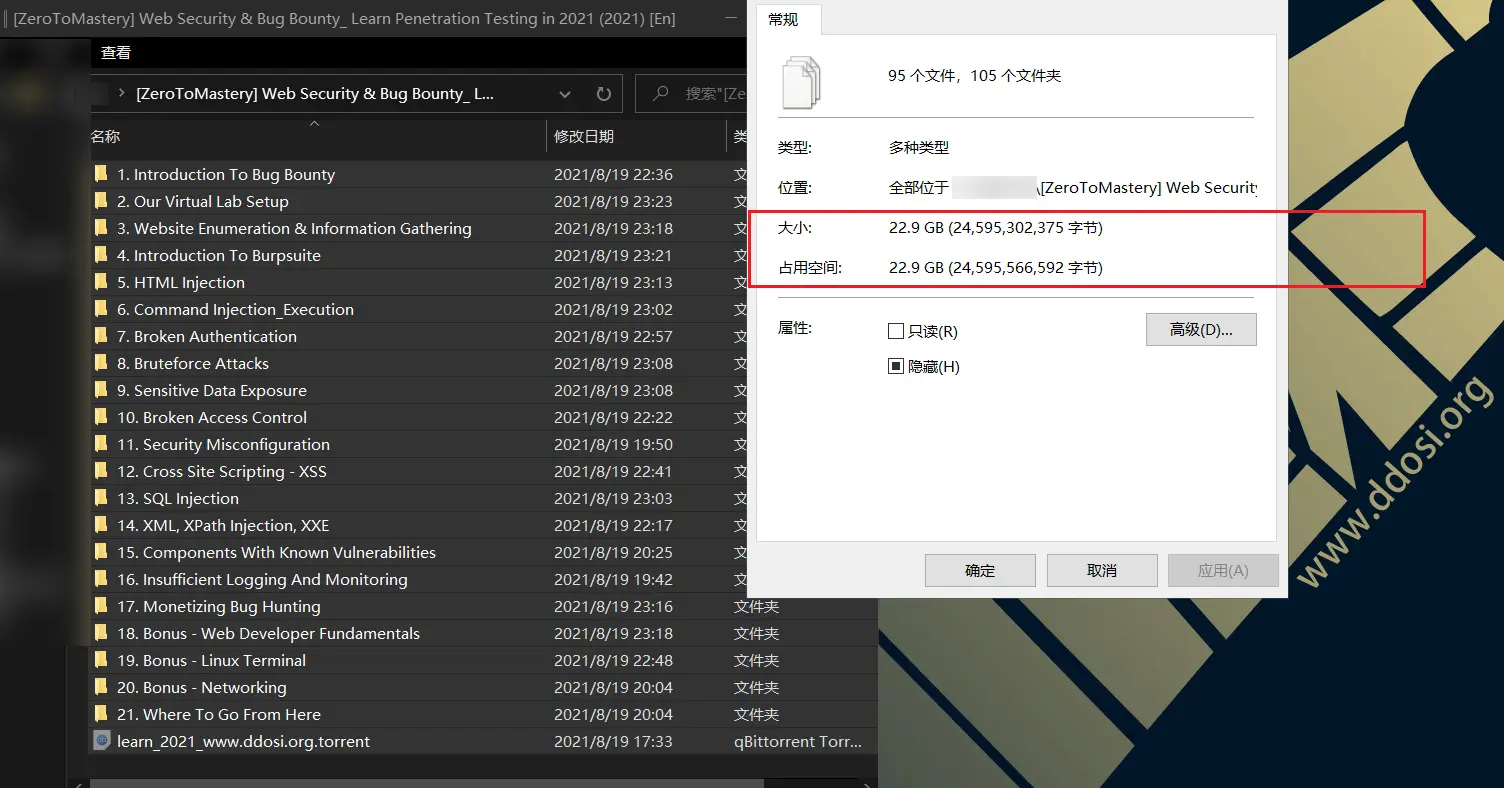
[ZeroToMastery] Web Security & Bug Bounty_ Learn Penetration Testing in 2021 (2021) [En]
│
├─1. Introduction To Bug Bounty
│ │ Course Guide- Bug Bounty _ Web Security by ZTM.pdf
│ │ Course Resources + Guide .pdf
│ │ Exercise_ Meet The Community.pdf
│ │ Join Our Online Classroom!.pdf
│ │
│ ├─Course Outline
│ │ Course Outline.mp4
│ │
│ ├─What is a Bug Bounty
│ │ What is a Bug Bounty.mp4
│ │
│ └─What is Penetration Testing
│ What is Penetration Testing.mp4
│
├─2. Our Virtual Lab Setup
│ ├─2 Paths
│ │ 2 Paths.mp4
│ │
│ ├─Creating TryHackMe Account
│ │ Creating TryHackMe Account.mp4
│ │
│ ├─Important- New Kali Linux Categories
│ │ Important- New Kali Linux Categories.mp4
│ │
│ ├─Kali Linux Installation
│ │ Kali Linux Installation.mp4
│ │
│ ├─OWASPBWA Installation
│ │ OWASPBWA Installation.mp4
│ │
│ └─Virtual Box, Kali Linux Download
│ Virtual Box, Kali Linux Download.mp4
│
├─3. Website Enumeration & Information Gathering
│ ├─Dirb
│ │ Dirb.mp4
│ │
│ ├─Google Dorks
│ │ Google Dorks.mp4
│ │
│ ├─Nikto
│ │ Nikto.mp4
│ │
│ ├─Nmap
│ │ Nmap.mp4
│ │
│ ├─Ping, Host, Nslookup .__
│ │ Ping, Host, Nslookup ....mp4
│ │
│ ├─Website Enumeration - Theory
│ │ Website Enumeration - Theory.mp4
│ │
│ └─Whatweb
│ Whatweb.mp4
│
├─4. Introduction To Burpsuite
│ ├─Burpsuite Configuration
│ │ Burpsuite Configuration.mp4
│ │
│ ├─Burpsuite Intercept
│ │ Burpsuite Intercept.mp4
│ │
│ ├─Burpsuite Intruder
│ │ Burpsuite Intruder.mp4
│ │
│ └─Burpsuite Repeater
│ Burpsuite Repeater.mp4
│
├─5. HTML Injection
│ ├─Advance Example of HTML Injection
│ │ Advance Example of HTML Injection.mp4
│ │
│ ├─HTML Injection - Theory
│ │ HTML Injection - Theory.mp4
│ │
│ ├─HTML Injection 1 on TryHackMe
│ │ HTML Injection 1 on TryHackMe.mp4
│ │
│ ├─HTML Injection 2 - Injecting User-Agent Header
│ │ HTML Injection 2 - Injecting User-Agent Header.mp4
│ │
│ └─Injecting Cookie Field and Redirecting The Page
│ Injecting Cookie Field and Redirecting The Page.mp4
│
├─6. Command Injection_Execution
│ ├─Bypassing Input Filter And Executing Command
│ │ Bypassing Input Filter And Executing Command.mp4
│ │
│ ├─Command Injection On TryHackMe and Blind Command Injection
│ │ Command Injection On TryHackMe and Blind Command Injection.mp4
│ │
│ ├─Command Injection Theory
│ │ Command Injection Theory.mp4
│ │
│ ├─Running PHP Reverse Shell With Command Execution Vulnerability
│ │ Running PHP Reverse Shell With Command Execution Vulnerability.mp4
│ │
│ └─Solving Challenges With Command Injection
│ Solving Challenges With Command Injection.mp4
│
├─7. Broken Authentication
│ ├─Basic Authorization in HTTP Request
│ │ Basic Authorization in HTTP Request.mp4
│ │
│ ├─Broken Authentication On TryHackMe
│ │ Broken Authentication On TryHackMe.mp4
│ │
│ ├─Broken Authentication Theory
│ │ Broken Authentication Theory.mp4
│ │
│ ├─Broken Authentication Via Cookie
│ │ Broken Authentication Via Cookie.mp4
│ │
│ ├─Forgot Password Challenge
│ │ Forgot Password Challenge.mp4
│ │
│ └─Session Fixation Challenge
│ Session Fixation Challenge.mp4
│
├─8. Bruteforce Attacks
│ ├─Bonus - Hydra SSH Attack
│ │ Bonus - Hydra SSH Attack.mp4
│ │
│ ├─Cluster Bomb Bruteforce
│ │ Cluster Bomb Bruteforce.mp4
│ │
│ ├─Hydra Bwapp Form Bruteforce
│ │ Hydra Bwapp Form Bruteforce.mp4
│ │
│ └─Hydra Post Request Form Bruteforce
│ Hydra Post Request Form Bruteforce.mp4
│
├─9. Sensitive Data Exposure
│ └─Sensitive Data Exposure Example
│ Sensitive Data Exposure Example.mp4
│
├─10. Broken Access Control
│ ├─Accessing passwd With BAC
│ │ Accessing passwd With BAC.mp4
│ │
│ ├─Broken Access Control - Theory
│ │ Broken Access Control - Theory.mp4
│ │
│ └─Ticket Price IDOR
│ Ticket Price IDOR.mp4
│
├─11. Security Misconfiguration
│ └─Security Misconfiguration - Default App Credentials
│ Security Misconfiguration - Default App Credentials.mp4
│
├─12. Cross Site Scripting - XSS
│ ├─Bypassing Simple Filter
│ │ Bypassing Simple Filter.mp4
│ │
│ ├─Changing Page Content With XSS
│ │ Changing Page Content With XSS.mp4
│ │
│ ├─DOM XSS Password Generator
│ │ DOM XSS Password Generator.mp4
│ │
│ ├─Downloading a File With XSS Vulnerability
│ │ Downloading a File With XSS Vulnerability.mp4
│ │
│ ├─JSON XSS
│ │ JSON XSS.mp4
│ │
│ ├─Old Vulnerable Real Applications
│ │ Old Vulnerable Real Applications.mp4
│ │
│ └─XSS Theory
│ XSS Theory.mp4
│
├─13. SQL Injection
│ ├─Blind SQL Injection
│ │ Blind SQL Injection.mp4
│ │
│ ├─Bypassing Filter In SQL Query
│ │ Bypassing Filter In SQL Query.mp4
│ │
│ ├─Extracting Passwords From Database
│ │ Extracting Passwords From Database.mp4
│ │
│ ├─Getting Entire Database
│ │ Getting Entire Database.mp4
│ │
│ ├─Guide To Exploiting SQL Injection
│ │ Guide To Exploiting SQL Injection.mp4
│ │
│ └─SQL Injection Theory
│ SQL Injection Theory.mp4
│
├─14. XML, XPath Injection, XXE
│ ├─XPath Injection
│ │ XPath Injection.mp4
│ │
│ ├─XPath Injection 2
│ │ XPath Injection 2.mp4
│ │
│ └─XXE
│ XXE.mp4
│
├─15. Components With Known Vulnerabilities
│ └─Components With Known Vulnerabilities
│ Components With Known Vulnerabilities.mp4
│
├─16. Insufficient Logging And Monitoring
│ └─Insufficient Logging And Monitoring Example
│ Insufficient Logging And Monitoring Example.mp4
│
├─17. Monetizing Bug Hunting
│ │ Unique and Interesting Bugs Discovered.pdf
│ │
│ └─What's Next & How To Earn Money By Finding Vulnerabilities
│ What_s Next and How To Earn Money By Finding Vulnerabilities.mp4
│
├─18. Bonus - Web Developer Fundamentals
│ ├─Breaking Google
│ │ Breaking Google.mp4
│ │
│ ├─Browsing the Web
│ │ Browsing the Web.mp4
│ │
│ ├─Build Your First Website
│ │ Build Your First Website.mp4
│ │
│ ├─HTML Tags
│ │ HTML Tags.mp4
│ │
│ ├─HTML, CSS, Javascript
│ │ HTML, CSS, Javascript.mp4
│ │
│ ├─HTTP_HTTPS
│ │ HTTP_HTTPS.mp4
│ │
│ ├─Introduction To Databases
│ │ Introduction To Databases.mp4
│ │
│ ├─Javascript On Our Webpage
│ │ Javascript On Our Webpage.mp4
│ │
│ ├─SQL - Create Table
│ │ SQL - Create Table.mp4
│ │
│ ├─SQL - Insert Into + Select
│ │ SQL - Insert Into + Select.mp4
│ │
│ ├─The Internet Backbone
│ │ The Internet Backbone.mp4
│ │
│ ├─Traceroute
│ │ Traceroute.mp4
│ │
│ ├─What Is Javascript
│ │ What Is Javascript.mp4
│ │
│ ├─What is PHP
│ │ What is PHP.mp4
│ │
│ ├─Your First CSS
│ │ Your First CSS.mp4
│ │
│ └─Your First Javascript
│ Your First Javascript.mp4
│
├─19. Bonus - Linux Terminal
│ ├─Linux 1 - ls, cd, pwd, touch.__
│ │ Linux 1 - ls, cd, pwd, touch....mp4
│ │
│ ├─Linux 2 - sudo, nano, clear .__
│ │ Linux 2 - sudo, nano, clear ....mp4
│ │
│ └─Linux 3 - ifconfig, nslookup, host .__
│ Linux 3 - ifconfig, nslookup, host ....mp4
│
├─20. Bonus - Networking
│ Networking Cheatsheet (Resource).pdf
│ Networking Cheatsheet.pdf
│
└─21. Where To Go From Here
│ │ Become An Alumni.pdf
│ │ Endorsements On LinkedIn.pdf
│ │ Learning Guideline.pdf
│ │
│ └─Thank You
│ Thank You.mp4下载地址
①种子文件:
magnet:?xt=urn:btih:d0d7bfd41eb5fef91b8b348e1e92267ec8bf9ccf&dn=[underver.se].t216987.torrent&tr=udp%3A%2F%2Ftracker.coppersurfer.tk%3A6969&tr=udp%3A%2F%2Ftracker.leechers-paradise.org%3A6969&tr=udp%3A%2F%2Fexplodie.org%3A6969&tr=udp%3A%2F%2Ftracker.opentrackr.org%3A1337&tr=http%3A%2F%2Fretracker.local/announce&tr=http%3A%2F%2Fund3rv3rse.info%2Ffree%2Fannounce
②zer0daylab
https://zer0daylab.com/ZMWSABB/
或
zer0daylab.7z
③torrent文件
learn_2021_www.ddosi.org.torrent
学习资料截图
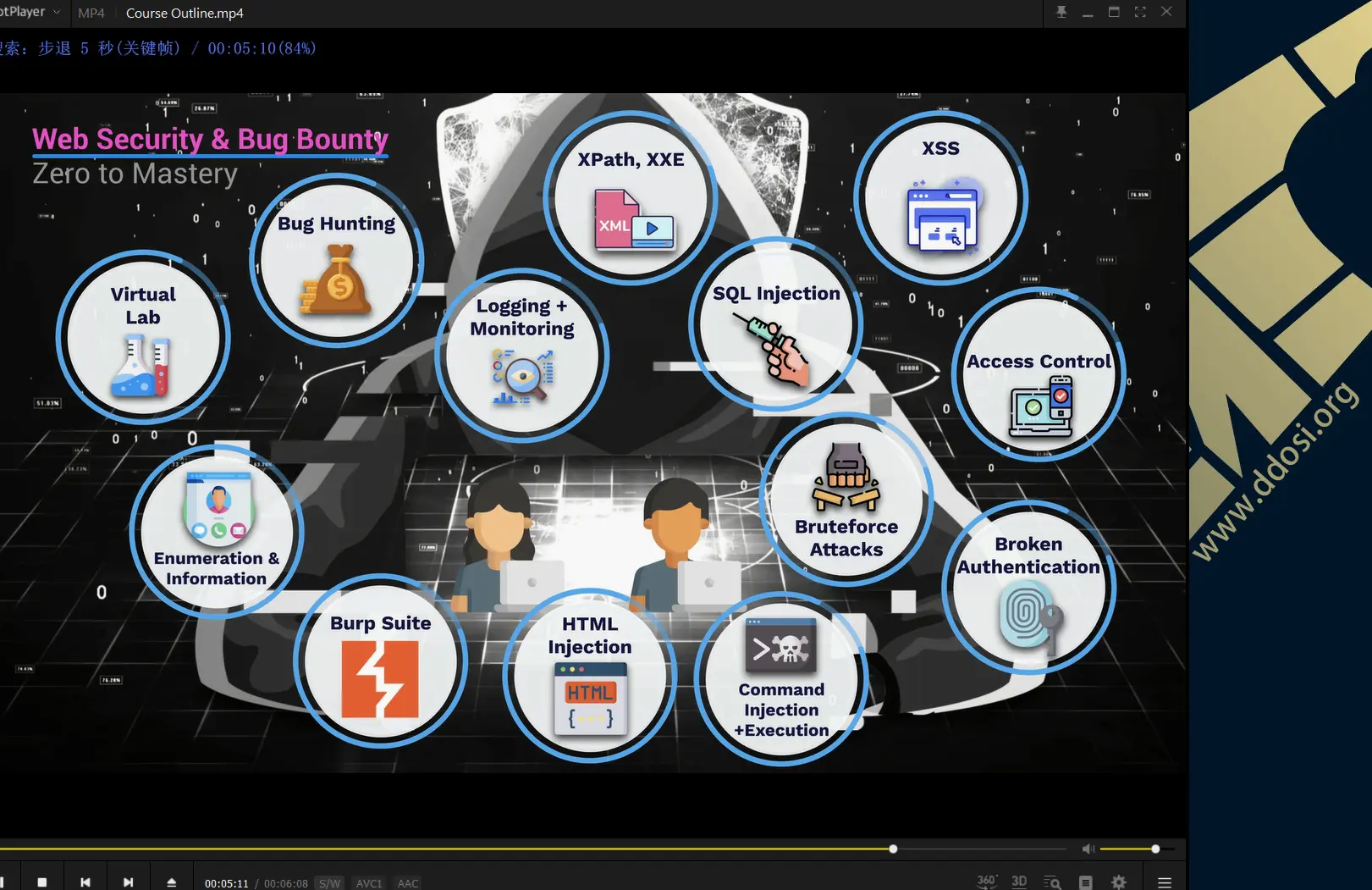
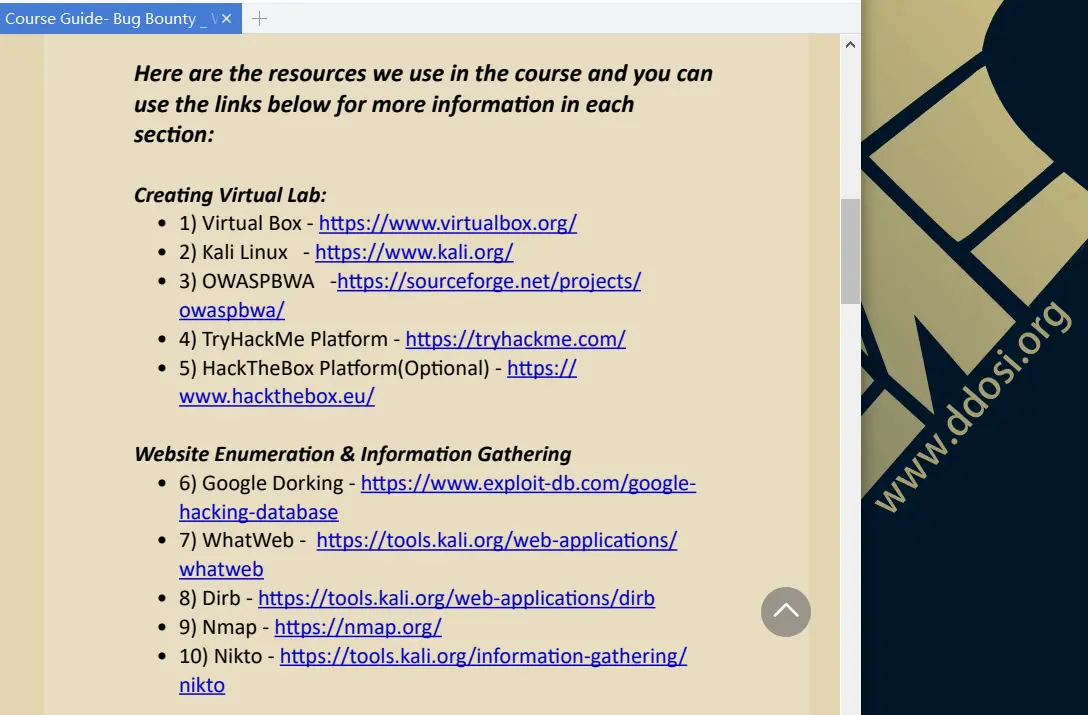
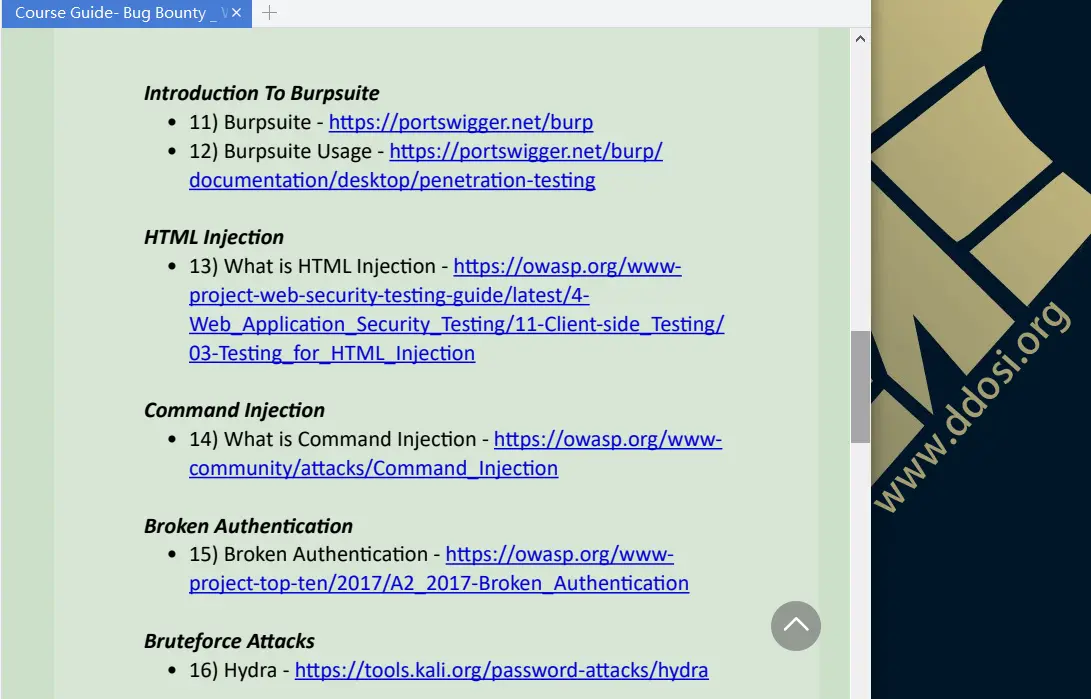
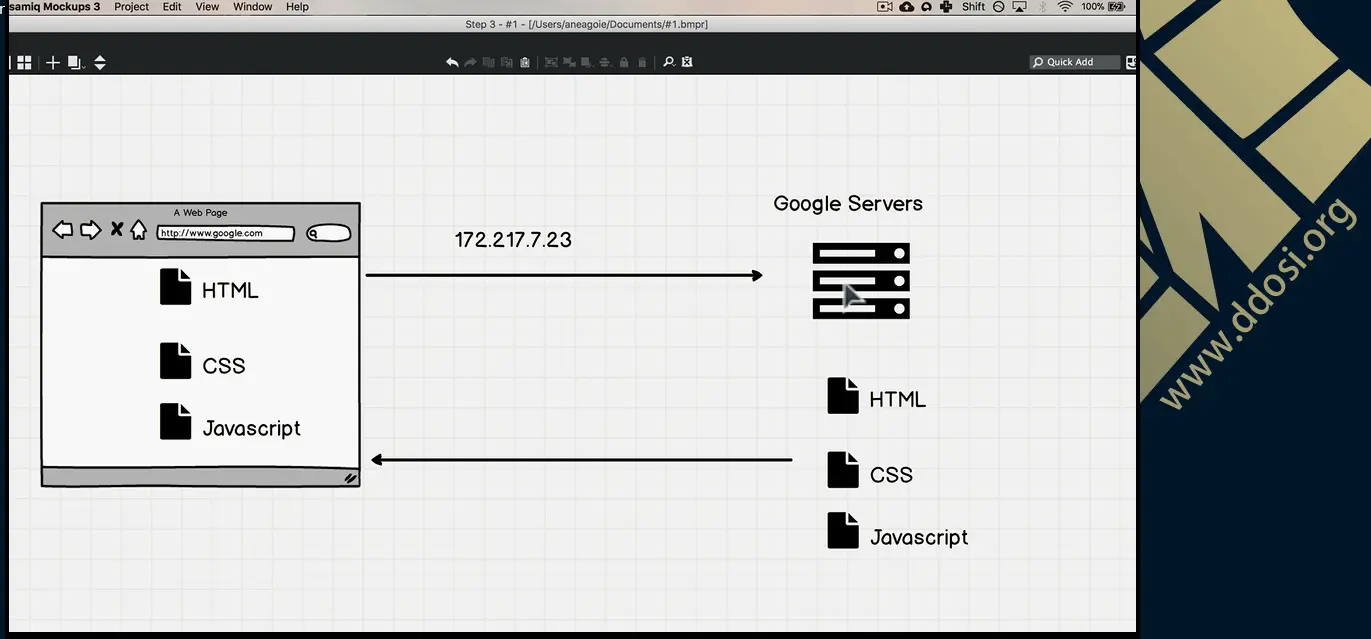
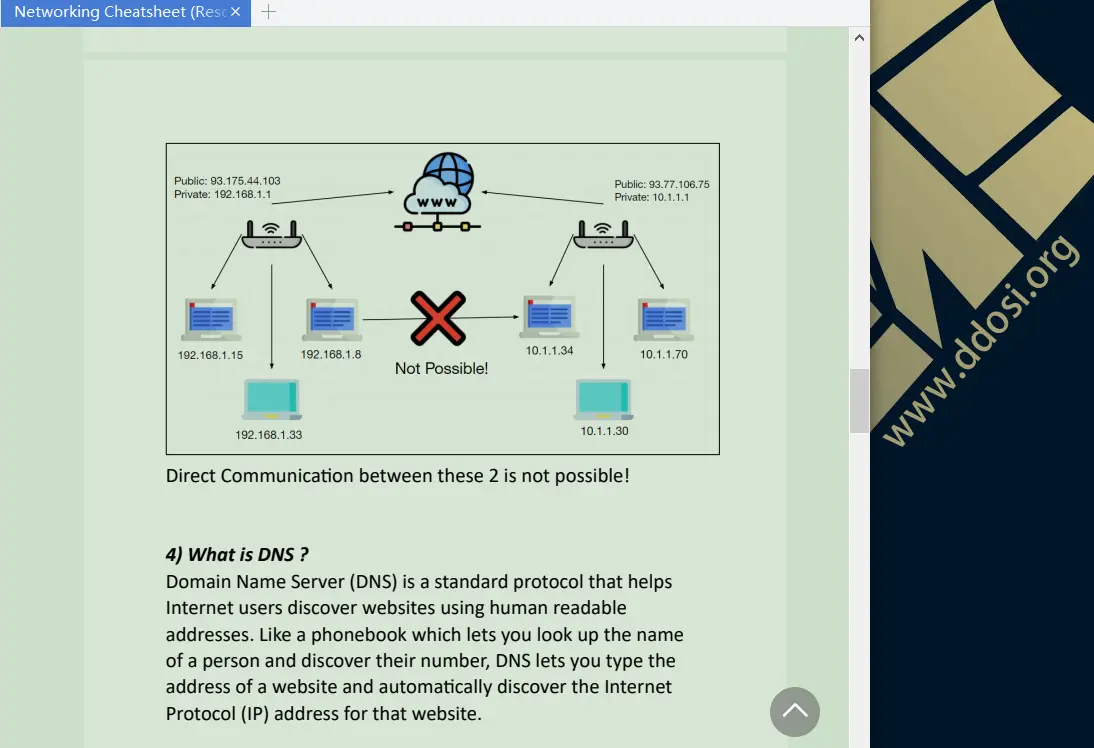
大体看了一下,个人感觉此教程也就一般货色,但有些地方也值得学习借鉴,有需要的可取其精华.
注意:全英文版本,听力不佳者慎重下载.
转载请注明出处及链接